It’s not uncommon to see criminals use disasters or current events to enhance their social engineering tactics, and the recent COVID-19 pandemic is no different. During a recent investigation, we received an email originating from 69.112.92.34 (x-originating-ip: [69.112.92.34]) with a [redacted]@[redacted].k12.ct.us email address and the following message body:
Due to the recent COVID-19 outbreak, IT Helpdesk is currently working on advance Staff portal in order to keep our staff/employee on task & organized schedules. All Staff/Employee are required to update their Staff Portal. To access the portal, Click on STAFF PORTAL for update. Failure to update your Staff portal, you will be deleted from our database. Sincerely, IT Helpdesk ©2020 Microsoft outlook. All rights reserved
The malicious user is employing the COVID-19 crisis to provide credibility as to why the impersonated IT Helpdesk would need the victim to update their personal information.
When clicked, the PORTAL link directs victims first to the URL shortener service bit.ly and then passed them along to the malicious phishing subdomain designmysite[.]pro:
hxxps://bit[.]ly/2Qu0dMZ ⤋ hxxp://8li9c1sr9queececshfj5lulh.designmysite[.]pro
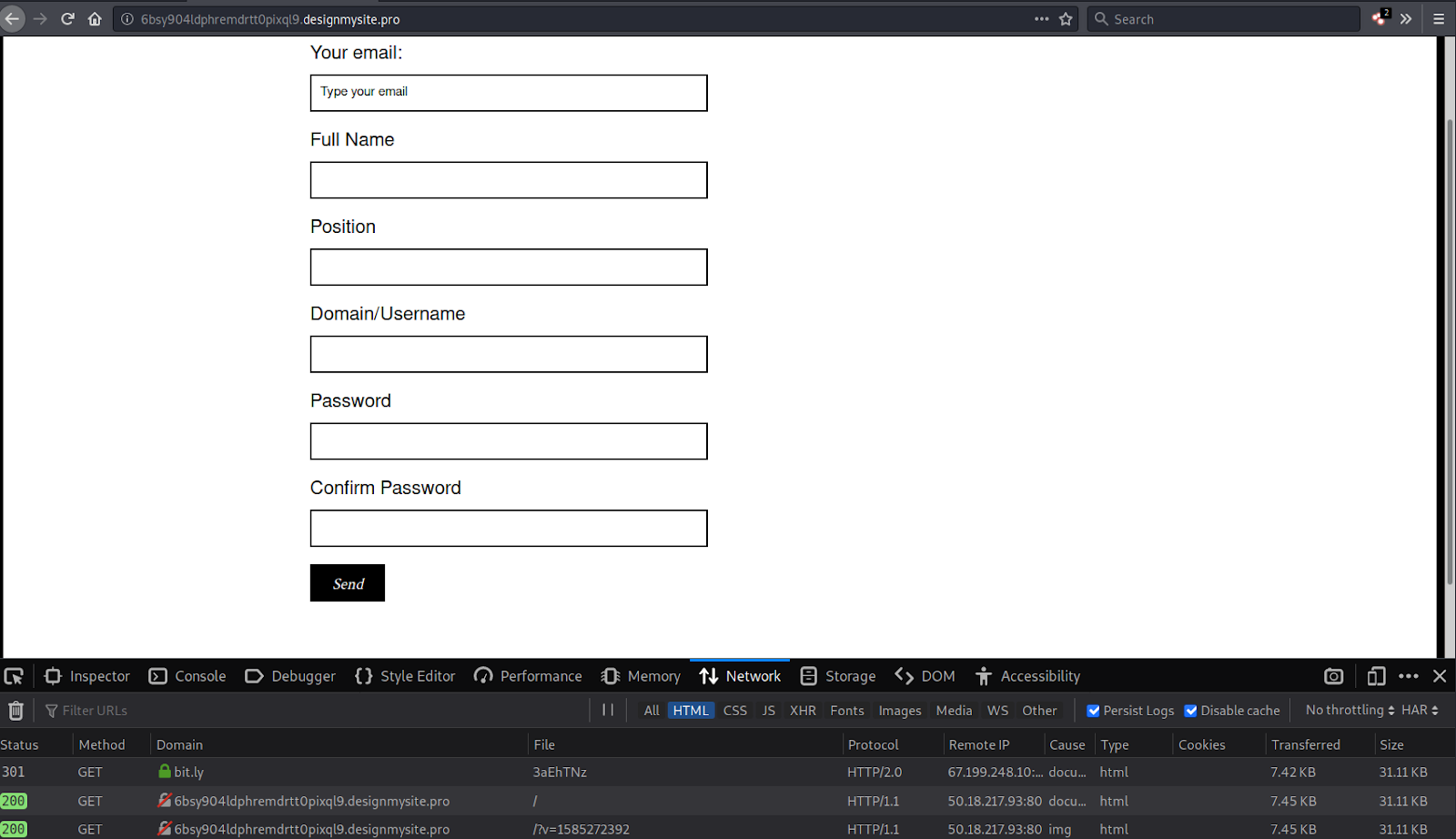
The subdomain 8li9c1sr9queececshfj5lulh.designmysite[.]pro was disabled before I could properly load it, however this is not the first phishing scam attempted by this domain. Continuing my research, I found another phishing page on a similar subdomain 6bsy904ldphremdrtt0pixql9.designmysite[.]pro:
As seen in the malicious COVID-19 phishing campaign, this particular phishing form is also disseminated through a bit.lyb> shortened URL. What’s more, there are multiple reports going all the way back to 2018 which show designmysite[.]pro spoofing or compromising existing educator email addresses:
- https://blogs.k-state.edu/scams/2018/07/17/phishing-scam-071718-attention-staff/
- https://its.unc.edu/phish-alert/it-help-desk-4/
When viewing the source of the phishing forms, it becomes clear that the email address spamingboxtool101@outlook.com is being used to collect the phished information submitted by victims:
"widget":{},"uniqueId":"Ajj7NKp9ACuwjMj","parentUniqueId":"ffpV5Q4d2ksrav0"},"page-zones__main-widgets__responsivecolumns1-zones__5e654f40427e2-widgets__5e654f405b223":{"ref":"5921879","uniqueHTMLId":"page-zones__main-widgets__responsivecolumns1-zones__5e654f40427e2-widgets__5e654f405b223","name":"5e654f405b223","fixed":false,"libraryItemRef":"0","pageRef":"1910011","temporary":{},"changed":{},"type":"widget.advancedcontactform","data":{"email":"spamingboxtool101@outlook.com","text":"Send","formTitle":"box","fromEmailLabel":"Your email:","fromEmailPlaceholder":"Type your email","collectEmailAddress":"1","localClass":"widget-advancedcontactform-84336F","uniqueId":"c7Z6hf92oPJCEEC","formFields":[{"title":"Full Name","type":"singleline","options":[],"mandatory":1,"id":"c7acbb10-6177-11ea-96dc-65cdea8475cd","order":1}...
This recent investigation clearly demonstrates why it’s important to keep an eye out for phishing campaigns – as well as misinformation in general. Familiarize yourself with the steps you can take to recognize a phishing campaign and avoid becoming a victim.