Navigating the world of website security can feel like stepping into a minefield, especially when you have to navigate threats like zero-day vulnerabilities. Zero-days are security flaws that, worryingly, remain hidden from everyone involved — from dev teams and users, to even the most conscientious vulnerability researchers.
In this post, we’ll take a look at what zero-day vulnerabilities are, what they mean for you and your website, and how to mitigate risk and protect your environment.
Definition of a zero-day vulnerability
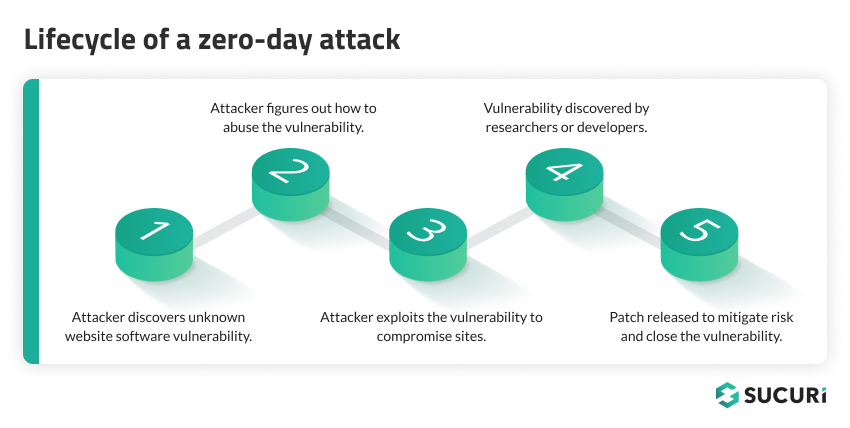
A zero-day vulnerability refers to a security flaw in software that is unknown to the party or parties responsible for patching or fixing the software. The term zero-day is derived from the fact that developers have ‘0 days’ to fix the problem that has just been exposed — and potentially already exploited by hackers.
In other words, by the time developers become aware of the vulnerability, it may already have been exploited. This makes it one of the most dangerous types of vulnerabilities, as it gives website owners and developers no time to defend against the initial wave of attacks.
A vulnerability is considered to be a zero-day vulnerability if it’s unknown to:
- The team maintaining the project
- The users of the project
- Vulnerability researchers
Vulnerability researchers are the good guys – people who won’t take advantage of the vulnerability for their own gain and who will exercise responsible disclosure.
Let’s illustrate this concept with a small example.
Example of a zero-day
Let’s say I’m the only maintainer of a premium WordPress plugin with a small user base, and I recently rolled out an update containing a vulnerability to all my plugin users.
In this example, I don’t have code audits by other developers, and this vulnerability was not picked up by either my manual or automatic tests. To complement this bad scenario, not a single plugin user cared to audit the new code either. So, this vulnerability is just sitting there, unnoticed.
Is this a zero-day vulnerability? Yes, it is!
If an attacker learns about this vulnerability, they won’t be interested in patching it. However, they will definitely be interested in exploiting it.
This last turn in our hypothetical scenario is actually common in real life and helps us see the enormous risk that zero-day vulnerabilities introduce to a website.
When the bad actors learn about a security vulnerability before the project’s maintainers, users, and vulnerability researchers do, things can get ugly really fast — that is, until a patch is released.
Why do hackers love zero-days?
Attackers love zero-day vulnerabilities because, with no security patch to stop them, the only thing in their way is the level of exploitability the vulnerability allows. Some vulnerabilities require a certain amount of privileges in order to be exploited – but then again, this depends on the vulnerability.
Attackers are really proactive when it comes to testing if a website is vulnerable or not to specific attack vectors. If this wasn’t enough, attackers are also big fans of automatization. Automated attack tools allow them to scan the internet looking for websites matching specific vulnerabilities and conditions.
How are zero-day vulnerabilities exploited?
When it comes to exploiting zero-day vulnerabilities, hackers usually have a field day. They exploit these unnoticed flaws before a patch or solution has been developed with a combination of skill, persistence, and the use of sophisticated tools designed to detect and exploit these vulnerabilities.
Common methods employed by hackers include injecting malicious code, phishing attacks, or using advanced persistent threats (APTs). These techniques allow them to gain unauthorized access, steal sensitive data, or even take control of your site.
The exploitation of a zero-day vulnerability is a race against time, with hackers trying to maximize their ‘window of opportunity’ before a patch becomes available.
How to protect your site from zero-days
Now that we’ve painted somewhat of a grim picture, let’s focus on the light at the end of the tunnel – protection. Guarding against zero-day vulnerabilities involves several best practices for website security.
Regular software updates, strong and unique passwords, minimal use of third-party plugins, and maintaining a secure hosting environment are some of the ways to fortify your site. We’ve put together a lengthy guide on how to protect your website and secure it from attacks.
But, the truth is that those security best practices should be complemented with other security controls to reduce the attack surface even more!
Web application firewalls are great to prevent zero-day vulnerability exploitations. They leverage defensive mechanisms that allow them to block the behavior that is known to be malicious. Services that offer Intrusion Detection Systems (IDS) can work in tandem to help alert you to any unusual activity.
It’s important to acknowledge that WAFs are not perfect and can be bypassed when a zero-day vulnerability exploits an attack vector that is not yet handled by any existing firewall rules. That’s why we have an amazing research team: to help maintain our rules and keep our WAF ahead of emerging threats.
Recovering from a vulnerability exploit
If you’re a website owner who’s experienced a malware infection as a result of a vulnerability exploit, we want you to know — you’re not alone.
Our team of experienced security analysts is here to help you navigate through this challenging time. We’re equipped with the skills and tools necessary to remediate the infection and clean up the malware on your website.
Getting in touch with us is straightforward: just start a chat or sign up for our platform. We’ll conduct a thorough analysis of your website and clean-up any malicious code. Post clean-up, we’ll also provide you with detailed recommendations to help improve your site’s security and prevent future attacks.
With Sucuri, your website’s security is in safe and capable hands.