Update: Read our new PCI Compliance guide.
This is the fourth post in a series of articles on understanding the Payment Card Industry Data Security Standard – PCI DSS. We want to show how PCI DSS can help anyone going through the compliance process using the PCI SAQ’s (Self Assessment Questionnaires). In the previous articles we have written about PCI, we covered the following:
- Requirement 1: Build and Maintain a Secure Network – Install and maintain a firewall configuration to protect cardholder data.
- Requirement 2: Build and Maintain a Secure Network – Do not use vendor-supplied defaults for system passwords or other security parameters.
- Requirement 3 & 4: Secure cardholder data – Protect stored cardholder data
As we move into the next section, “Maintain a Vulnerability Management Program”, we will talk about Requirements 5 and 6 individually and in more detail.
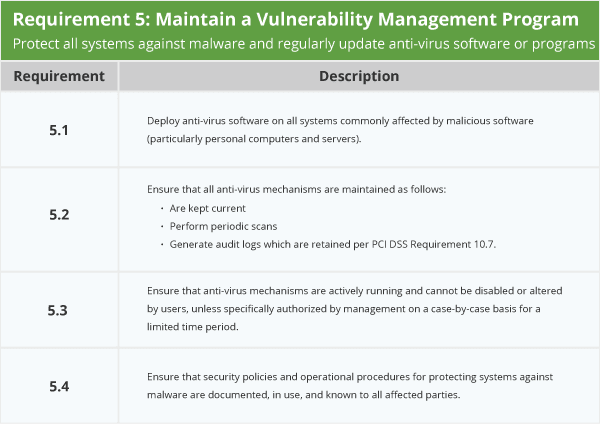
PCI Requirement 5
Protect all systems against malware and regularly update anti-virus software or programs
PCI Requirement 5 shows the need for maintaining a vulnerability management program in order to protect all systems against malware and regularly update anti-virus software or programs.
It is crucial that you run an antivirus software with the latest security patches for your operating system (Windows currently on 10; Mac OS currently on 10.13.6) and for all other programs you use. New vulnerabilities are uncovered and exploited every day.
Also, be mindful of programs like Java, Adobe Flash, etc. and make sure they are up to date too. It is easy to ignore security updates for these applications if you don’t use them very often.
Improve your Computer Security
We have written an extensive post on how to help secure your computer to improve your own personal security. This can help satisfy the PCI 5th requirement across all the machines you’re operating for business purposes.
As business continues to test new channels in reaching consumers, mobile access through our devices will be another security risk to consider.
Improve your Cellphone Security
Safety measures can be built into mobile apps as more and more people connect through Androids and iPhones. A good example I have seen, is blocking access to systems if someone is attempting to connect to a particular version of an app that has a security vulnerability. This is a key security measure due to the fact that even if the vulnerability is fixed on your end, consumers don’t always upgrade their apps to the latest version (let’s be honest with ourselves) and aren’t aware that such a vulnerability exists.
To further help address PCI Requirement 5, here are some other valuable tips:
- Keep malware protection up to date and set to scan files and pages as needed.
- Configure malware protection to perform regular scans and prevent connections to malicious websites.
- Ensure that your antivirus is actively running and cannot be adjusted by unauthorized users (your front clerk, for example) unless specifically asked by management for a limited time.
While ensuring you have all the proper software and systems up to date is a critical step for anyone with an online presence; developing the applications you’ll need also needs to be done with security front of mind.
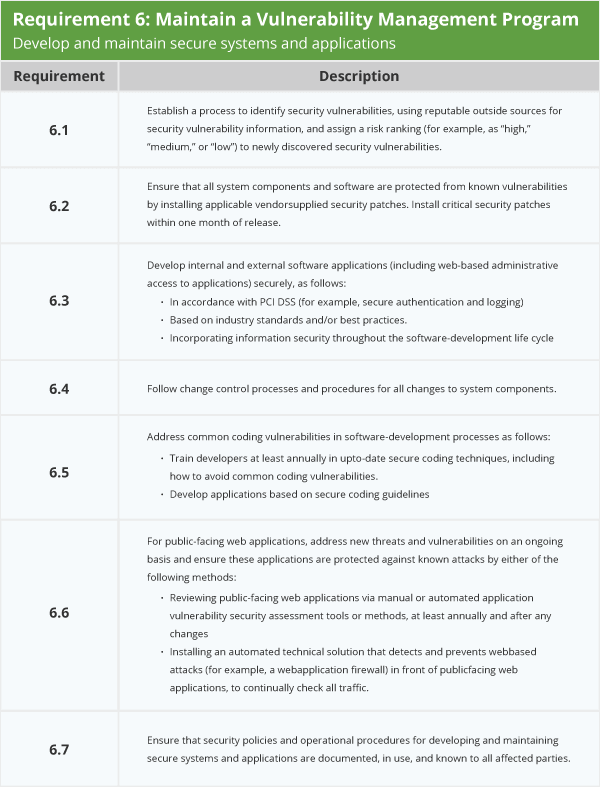
PCI Requirement 6
Develop and maintain secure systems and applications
PCI Requirement 6 shows the need for maintaining a vulnerability management program in order to develop and maintain secure systems and applications.
Ensuring a secure workflow throughout the development and staging process is as key as ensuring your live production site is secure. Bear in mind that vulnerabilities can also generate issues in pre-production (dev) environments.
Introducing New Secure Systems to a Business
Think of it this way. Whenever new systems are introduced or existing ones need to be adjusted, businesses need to make sure to:
- apply secure standards at every step;
- install a change detection system;
- install an antivirus software;
- enable audits logs;
- retain audit logs.
It is better not to run the risk of forgetting about software that is suddenly outdated during the development process. I have elaborated on what things to keep visibility over in a previous post about how to secure your online store.
Addressing Common Code Vulnerabilities
PCI Requirement 6 is designed specifically to address common code vulnerabilities, which can include attack types like:
- SQL injection,
- Improper access control,
- Cross-site request forgery,
- JS Injections
To avoid a data breach as a result of a vulnerability, requirement 6.6 states:
Address new threats and vulnerabilities for public-facing web applications on an ongoing basis and ensure these applications are protected against known attacks….
Adding a Website Application Firewall as a Defense Measure
This is where a Web Application Firewall, or WAF, can be a great benefit to ensuring that you maintain PCI compliance according to this particular requirement.
Our Web Application Firewall helps address the attacks listed above as well as all Layer 7 (HTTP/HTTPS) attacks. If you have never deployed a cloud-based WAF like ours, you can read more on how a WAF works and the benefits of using it.
To further help address PCI Requirement 6, here are some other valuable tips:
- Have licensed and supported software to ensure patches for software vulnerabilities are available for installation. Remove out-of-date software.
- Install updates and security patches in a timely fashion.
- Install security patches within 7 days of release.
Other Tips for Maintaining a Vulnerability Management Program
Depending on the approach you take (managed cloud solution or in-house measures), there are unique actions to take for. Nevertheless, here are some keys that can be of benefit to both approaches:
Subscribe your team to known vulnerability alerts
Having an active vulnerability alert allows you to be notified immediately upon a vulnerability disclosure. Our blog is a great resource for keeping up with important security disclosures.
You can subscribe here to stay updated on new tactics and techniques out there as well.
Scheduled vulnerability scanning
Vulnerability scanning can be an automated process to check your application for vulnerabilities and weaknesses.
This will help uncover vulnerabilities such as SQL Injection and Cross Site Scripting (XSS) which are some of the OWASP Top 10 threats.
Conclusion
Today we have discussed PCI requirements 5 and 6 which demands webmasters to maintain a vulnerability management program.
In upcoming posts of this series, we will touch on the next set of requirements that speak to implementing strong access control measures.