It’s not very often that we see abandoned components being used on a website — but when we do, it’s most often because the website was exhibiting malware-like behavior and we were called to investigate and clean up the site.
Old and abandoned plugins and themes are a good target for opportunistic attackers who are looking for any expired domains that might be used by those components. Once an attacker gets a hold of those domains, they’re able to distribute malware to any users that still have that resource installed on their site. Here’s an example of that exact scenario.
Expired Domain for My Weather Plugin
The plugin was called “My Weather” and one of its main functions was to show weather widgets on a website. The data for weather information was retrieved by the plugin from an external domain (weatherforecastmap[.]com), which happened to expire.
$widget_call_string = 'hxxp://weatherforecastmap[.]com/' . $typeflag; $widget_call_string .= '.php?zona='.$country_name; $widget_call_string .= '_'.$city; $widget_call_string = str_replace(" ", "-", $widget_call_string); $widget_call_string = strtolower($widget_call_string); if($fahrenheitflag != 0) $widget_call_string = str_replace(".php", "F.php", $widget_call_string);
Weather Data Replaced with Malicious Injections
The URL generated by the plugin for the weather data was based on the city and country — for example: hxxps://weatherforecastmap[.]com/weather3F.php?zona=mexico_playa-del-carmen
echo '<script type="text/javascript" src="'.$widget_call_string . '"></script>';
Attackers were able to register the domain and, instead of serving the weather information, they replaced the data source with a malicious JavaScript injection which was loaded on a user’s browser whenever they visited a site using the abandoned My Weather plugin.
Unwanted Browser Add-ons & Advertisements
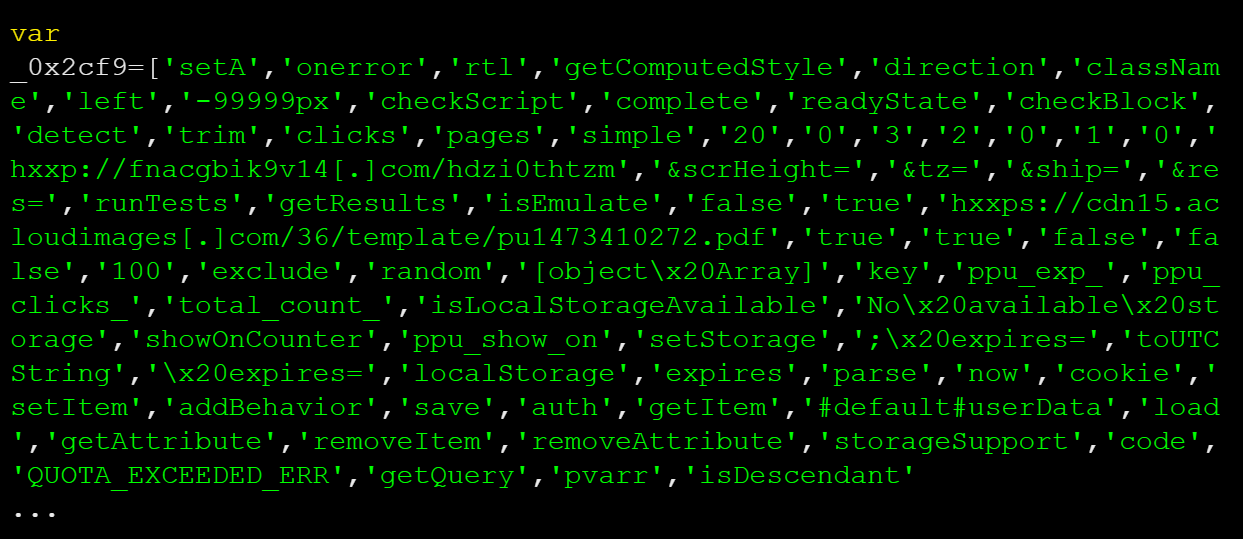
This example clearly demonstrates how outdated and abandoned components can put your site at risk. We recommend keeping all software updated to prevent these types of issues from impacting your site’s reputation — and if you happen to have a plugin, theme, or component on your site that you aren’t using, get rid of it.
Another way to mitigate risk is to add a WAF (Web Application Firewall) to your website. WAFs can prevent many attacks, especially if you have old or outdated plugins which may contain known vulnerabilities — the firewall will be able to virtually patch your software until you get the chance to update or transition to a new one.