A web application firewall (WAF) is a great way to detect and filter incoming malicious requests before they can exploit website vulnerabilities and security flaws. While a WAF helps protect against threats over HTTP/HTTPS, the website can still be hacked from the inside.
Cross-site Contamination
One common way that websites get reinfected is through cross-site contamination, which can occur even when a website is behind a firewall.
Cross-site contamination happens when one website is infected and the malware copies itself into other directories, infecting all sites on the same server. This can happen when there are multiple websites hosted under the ownership of one user (e.g cPanel user). Unless every website is secure behind a WAF, it only takes one unprotected site to cause a massive hack.
Website owners can experience cross-site contamination when they harden and secure their primary website behind a WAF, but don’t apply the same security for “less important” websites in subdirectories (e.g ~/public_html/otherdomain.tld).
If one website becomes infected with malware, the infection can bypass the primary website’s WAF since it doesn’t require HTTP access to the primary website — it can use FTP. Malware that already exists in the file system can not be mitigated by a WAF.
If possible, we recommend placing each website under its own cPanel user to prevent cross-site contamination.
Weak Passwords and Dictionary Attacks
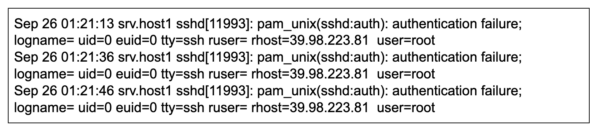
Another reason reinfections occur (despite using a WAF) is because of passwords. Attackers target non-HTTP/S services like FTP or SSH and try brute force / dictionary attacks to compromise users with weak passwords.
Shouldn’t a WAF stop dictionary attacks in the first place? They do — but via HTTP. Malicious users also target services (e.g FTP) that are independent of the server’s HTTP/S service. Their attacks target the server’s hostname or IP address instead of the website address, which is protected by the WAF.
Our WAF is designed to protect the website application. Most web hosts secure their own servers, but they delegate the responsibility of securing website content to the website owner. All the web host promises to fulfill is a specified uptime rate (e.g 99.9%).
How to Prevent Website Reinfections
Due to the potential risk of website reinfections — even under the protection of a firewall — it’s important to audit the services used by your web server(e.g SSH, FTP) and begin hardening their security. Hardening recommendations include changing minor settings like the default SSH port to something other than 22, or more drastic changes like disabling the FTP service altogether.
To make these type of changes, you’ll probably require root access which is limited to VPS or dedicated hosting plans, but regardless of your hosting plan you should be able to audit your existing FTP and SSH user(s) and remove any that are not needed.
Using an independently hosted WAF is a great option for most website owners wanting to secure their website application against malicious traffic. But a direct vulnerability exploit or attack against your website application is not the only way that attackers can infect your website with malware. Make sure you have strong passwords everywhere and don’t forget to protect all websites on your server. You can chat with us if you have any questions.