Exploitation Level: Easy / Remote
DREAD Score: 8.4
Vulnerability: Stored XSS on Admin dashboard
Patched Version: 4.8.1
The WordPress Slimstat plugin, which currently has over 100k installs, allows your website to gather analytics data for your WordPress website. It will track certain information such as the browser and operating system details, plus page visits to optimize the website analytics.
Versions below 4.8.1 are affected by an unauthenticated stored XSS on the administrator dashboard.
Timeline
- 2019/05/16: Initial disclosure
- 2019/05/20: Patch released (4.8.1)
- 2019/05/21: Blog post released
Details
This vulnerability allows a visitor to inject arbitrary JavasScript code on the plugin access log functionality, which is visible both on the plugin’s access log page and on the admin dashboard index—‚ the default page shown once you log in.
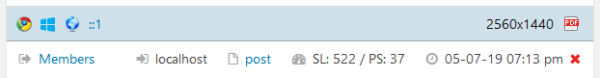
Using the access log, it is possible to see details of the users accessing the website.
These details include ip address, operating system, browser, and the installed plugins of the browser.
These are found by an analytics client-side script which fingerprints the client information and then performs a request to the plugin while giving out its own properties.
A malicious user could forge an analytics request by pretending his browser has a specially crafted plugin to inject arbitrary code on the plugin access log. This will be executed once an admin logs in.
Technical Details
The expected value of plugins are the default-supported browser plugins, such as pdfviewer, flash or java.
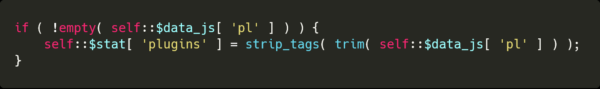
The plugin property is sanitized using the strip_tags php method, removing any tags from the original plugin value.
When viewing the details of an access log entry, among the details are an image of the installed plugins, such as the pdf viewer on this image.

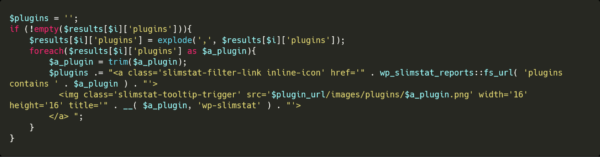
Here is how the image is generated for the plugins, where $a_plugin is the plugin:
Since the plugin has only been sanitized with strip_tags, and that is injected in an attribute, we can escape the attribute by using a single quote, and add an event handler.
By having plugin’onerror=’alert(document.domain) as a plugin, the resulting HTML would be the following:
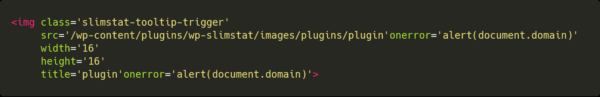
This will trigger the onerror event since the image is invalid, therefore giving a stored XSS.
Update as Soon as Possible
If you’re using a vulnerable version of this plugin, update as soon as possible. In the event where you cannot do this, we strongly recommend leveraging the Sucuri Firewall or equivalent technology to have the vulnerability patched virtually.