When a site gets compromised, the attackers will often leave some piece of malware behind to allow them access back to the site. Hackers want to leave a door open to retain control of the website and to reinfect it continuously. This type of malware is called a backdoor.
What Are Backdoors?
Backdoors are types of malware that allow for remote control of a compromised website by bypassing appropriate authentication methods.
Even after updating a site, changing its passwords, and doing other post-hack procedures, the backdoor might not be removed. Leaving a backdoor in a website allows it to be accessed unexpectedly.
Even though there are backdoors written in all languages, the ones we see the most are done in PHP.
Why Are Backdoors So Hard to Find?
Backdoors are usually very hard to find because they don’t have to be linked anywhere in the site. They don’t need to be big, quite the opposite; they can be very small and go unnoticed.
Actually, most backdoors are designed so that they can be easily confused with non-malicious code. Some of them have passwords, some are heavily encrypted/encoded and they can be located anywhere in a website’s file system or database.
There are two main issues when trying to find a hidden backdoor.
First, in order to easily identify backdoors on your site you would have to know all the files and be familiar with all their content in order to be able to spot the differences.
Second, these functions can also be used legitimately by plugins. Be sure to test any changes because you could break your site by removing benign functions.
Look at this code, would you say it is a backdoor?
![]()
Yes, it is a website backdoor. This code allows attackers to execute any type of code, add files, remove files, and perform other nefarious acts. When you are analysing thousands of lines of code, it can be easy to miss it.
What about this code:![]()
You are right if you said yes. In that code, the majority of the backdoor is hidden inside an image (void.jpg).
Types of Backdoors
Backdoors can appear in different types, here are some examples of backdoors:
Big and complex backdoors:
These are the easiest to spot because they are big. Here is an example of the “Filesman” backdoor, big, complex and easy to find:
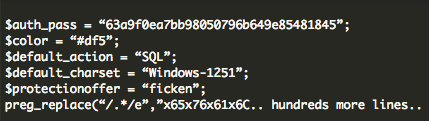
Short and simple backdoors:
Backdoors can also be very short and simple and perform different actions, as seen below.
The following example of a backdoor is used to execute any code from the “php” request:
![]()
CMS specific backdoors:
Some backdoors are specific to a content management system (CMS).
The following example shows a WordPress-based backdoor. This time, the malicious content is hidden inside the database in the wp-options tables.
![]()
Conclusion
These are just some of the many examples of website backdoors that our malware removal and research teams see every day. If you believe your website might have a backdoor, but you are still unsure of how to find it. We have a dedicated team of security analysts that will be happy to find them for you.
Sucuri has been involved specifically in the website security space, analyzing what attackers do and how they do it. This knowledge is at the core of how the technology is built. Get to know our Website Security Platform.