Attackers regularly target online gaming accounts as they can quickly sell any transferable items along with account logins to a third party. This scenario has cropped up for years now, and has affected a growing number of popular online games ranging from Runescape to Fortnite.
These games run on their own clients — so stealing logins will only give the attacker access to that specific game (sometimes a few others). To gain broader access, attackers are choosing to target digital distribution clients like Steam or Origin. These clients allow multiple games to be managed under a single account, and include popular games like Counter-Strike: Global Offensive (CSGO) which boast tens of millions of players.
A large player base means there will be a higher demand for the accounts and any associated items — ultimately making it more attractive to bad actors, since they won’t have to wait long for interested buyers. The longer the attacker has to “sit” on the stolen account, the higher the chance of the owner being able to regain access and prevent the attacker from using it.
CS:GO Skin Gambling Phishing Lure
This phishing page was initially reported to us through labs@sucuri.net. Upon investigation, we found it had been set up under a recently registered (2020-03-10) domain csgo500[.]org.
Evidently, this domain had been intentionally selected to mimic the victim site csgo500[.]com, which offers users the ability to gamble in-game CS:GO items on their platform — a feature commonly referred to as skin gambling.
One interesting point to note is that the original domain being imitated by this phishing campaign (csgo500[.]com) has geoblocking enabled, and does not allow entry for requests from the United States. It also prevents access from the Netherlands, Curaçao, France, or any other country where online gambling is prohibited.
On the other hand, the phishing website csgo500[.]org doesn’t mimic this geoblocking and allows requests from these countries.
Before a user can gamble, they must first “fund” their account by transferring in-game items (skins) from their Steam account (or at least validate their existence). To accomplish this, the user needs to log into their Steam account. This is usually done by redirecting the user to the Steam website, the user authenticates as they normally would, and then it redirects them back to the original website.
Phishing Behavior
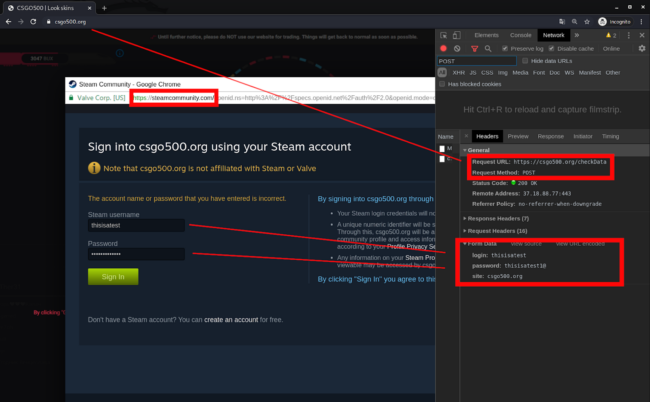
One of the primary red flags is the behavior of the phishing page found on the malicious csgo500[.]org domain, which allows attackers to harvest user credentials from unsuspecting victims.
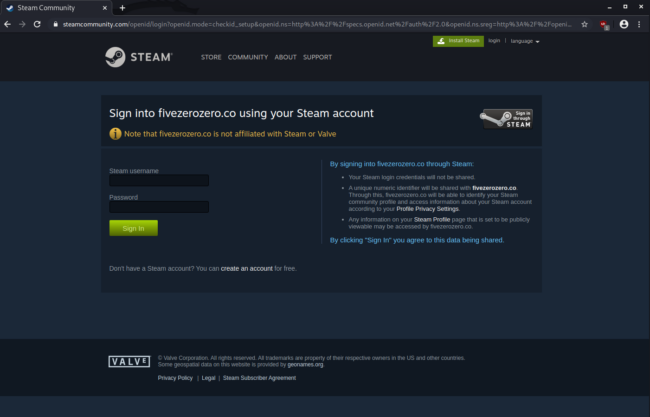
Whenever a user clicks the Sign in button, the phishing site spawns an iframe that spoofs a new Chrome browser to load the official Steam login page, as seen below.
Whenever a victim enters their Steam account username and password and submits the data via a POST request, the malicious csgo500[.]org domain intercepts the login information before sending it to the original Steam website.
Credential Validation & Authentication Checks
If a valid Steam account username and password is entered on the fake sign in page, attackers perform a quick validation of the login credentials before finally redirecting the victim to the real csgo500[.]com website.
Unless you happen to be viewing these requests in a browser’s developer tools, it can be hard to detect this malicious behavior. But there are still some signs that help show it’s suspicious.
- It will try to show the new iframe as a Chrome window regardless of the browser used, so if you aren’t using Chrome, a Chrome window should not open on its own.
- The iframe for the fake Chrome window doesn’t operate as a normal browser window would. You can’t click things like the address bar or the SSL bar.
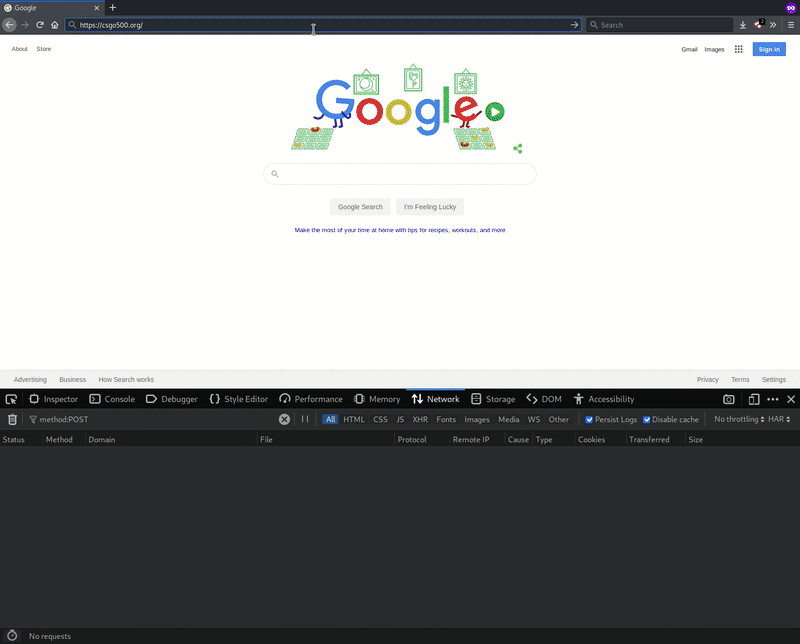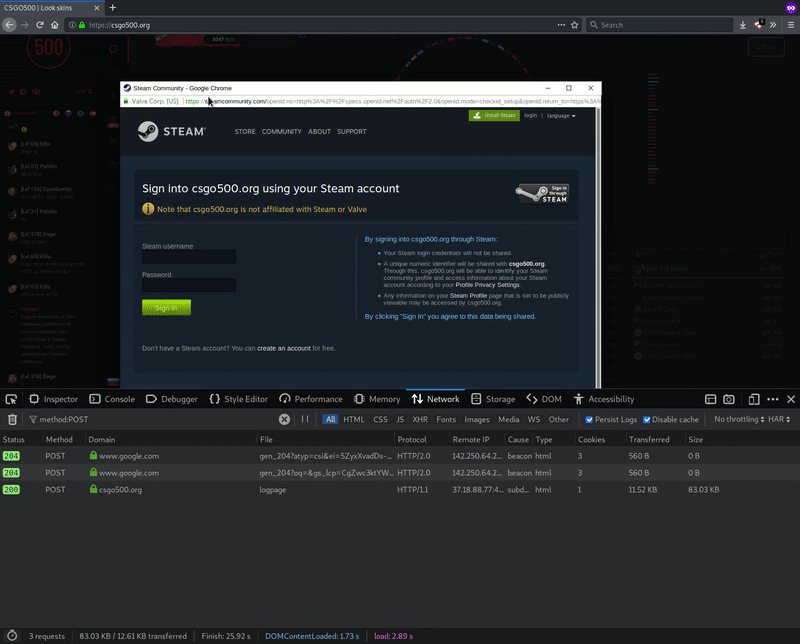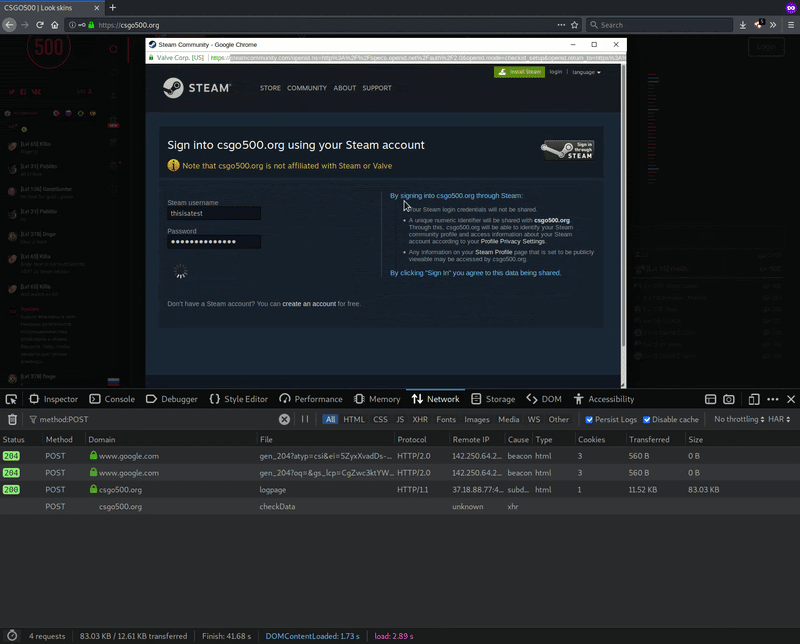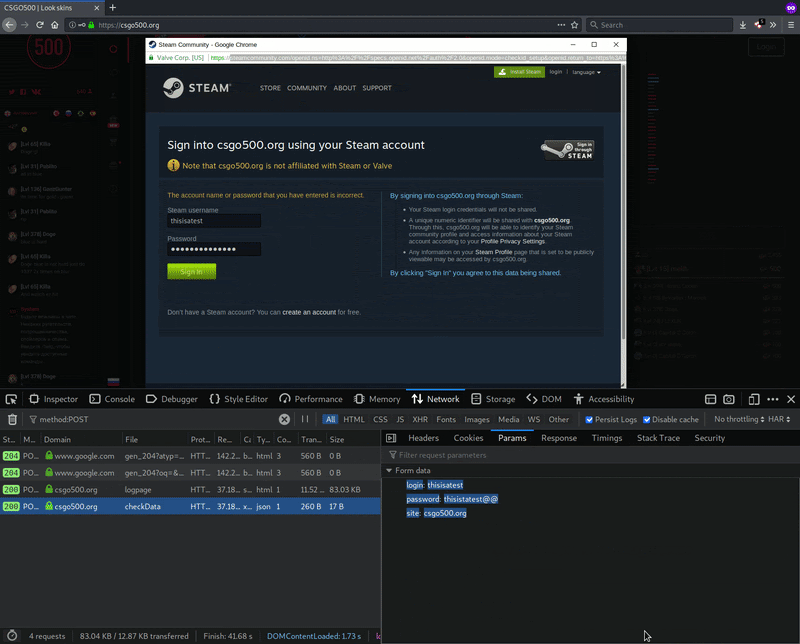
Here’s an example of the POST request the phishing page sent when I was testing it. You can see it is submitted to csgo500[.]org/checkData instead of directly to the Steam web server.
This is not the correct way to authenticate with Steam. Post requests containing plaintext login data shouldn’t be sent to third parties — and the malicious domain has indeed been set up in such a way so it can phish any login information submitted by victims.
In contrast, the legitimate csgo500[.]com domain follows proper development practices and redirects users to Steam’s website for authentication. When the POST request is submitted during login, it is sent to the proper Steam authentication server — and not a third party that can steal it.
Conclusion
A phishing campaign can be tough to detect. Whether you’re a visitor or website owner, bad actors have a lot of clever tricks up their sleeves. As we saw from this campaign, attackers can successfully imitate a domain, two websites, and a Google Chrome popup window.
This is especially concerning for website owners who might be fraudulently imitated. In an example like this, the malicious domain and its website are hosted elsewhere. To best detect if a malicious phishing website is imitating your brand, you’ll likely need to set up some type of brand monitoring system. This can help protect your site from being tarnished by imitation phishing campaigns.