A common pattern we see in compromised websites is the presence of backdoors and other malicious code. During Q3 of 2016, we found that 72% of all compromises that we encountered had a PHP-based backdoor hidden within the site. Attackers experiment with various techniques and types of malware to abuse server resources and distribute spam while maintaining access to the site for as long as possible.
In the case of automated attacks, sometimes we’re lucky enough to see hackers access the same website and step on each other’s toes. When multiple hackers try to compromise the same site through similar attacks, we see interesting results.
Backdoor Shell in vBulletin Database
While investigating a case, we found that exact issue regarding a backdoor. One of the most used backdoors is the C99 web shell. For those unfamiliar with it, C99 is a variation of the WSO shell with additional functionalities. It allows the attacker to manage a victim’s website remotely, including executing arbitrary remote commands directly into the system, navigating through a file manager interface, reading arbitrary files, and much more.
While this kind of shell is typically found inside files, we recently found it in a vBulletin database. vBulletin is a prime candidate for backdoors within a database due to the platform’s ability to run PHP directly from the database.
The vBulletin datastore table (more specifically the pluginlist record) is widely used to store malicious content. Through this table, hackers can add arbitrary PHP code which becomes part of any plugin installed on the website. In some cases, the attackers also add the malicious code as its own plugin by adding it on the plugin table.
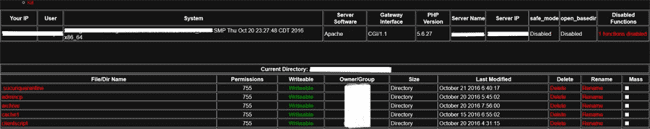
In this case, we saw a regular shell appearing when we accessed /forum.php/subscriptions.php
The path where it is accessible may look strange, but requests in vBulletin are handled by forum.php instead of the common index.php.
Tracing it, we found the culprit in the database within the plugin table:
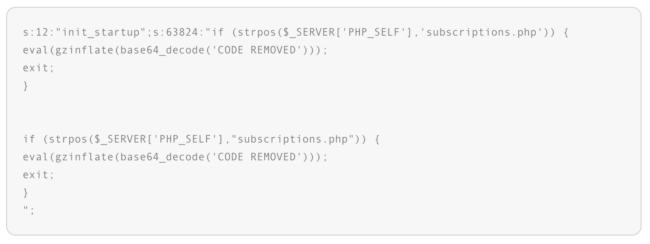
From the image above, we see two records posing as init_startup plugins. This immediately caught our attention since it’s not valid for more than one plugin to have the same name within vBulletin.
We identified the plugins responsible for displaying the shell, however, the investigation doesn’t stop there. Those plugins must still have an occurrence within the pluginlist row inside the datastore table in order for it to actually be enabled and act on the site.
A Tale of Two Hackers
By taking a quick look at those records, we found various pieces of malicious code:
When checking the database entry, we see two sets of code that have the same purpose. This indicates the likelihood of at least two different attackers exploiting the same vulnerability through an automated system and adding the same malware.
The funny thing is that after the first “exit” instruction, the second set of code becomes nonfunctional as it will no longer be read or executed by the server.
In other words, the first attacker compromised the site and then the second one attempted the exact same thing. Unfortunately for them, the init_startup already existed and their attack simply infected the already existing plugin. Since the first infection was the regular shell and not the c99, this means that the c99 did not work.
Global Backdoor in vBulletin
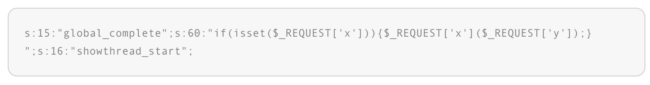
There was also another small but powerful piece of malware injected into the database:
This code renders the entire forum a backdoor regardless of the area you are in. The only requirement is to send an instruction through a request such as $_GET or $_POST:
forum.php?x=shell_exec&y=rm -rf ./
It may look like an extremely simple set of instructions, but it’s more than enough to delete all the files of the site.
Many other sets of instructions can be sent like this to infect the site with other kinds of malware.
Conclusion
This brings up some serious concerns.
What if the infections had some sort of incompatibility between each other?
What if the result was destructive to your website?
A multitude of issues can arise as soon as your website becomes vulnerable, so it’s extremely important to keep it secure and ensure that you have firewall protection to patch security issues and stop hackers from breaking into your website.