Exploitation Level: Easy / Remote
DREAD Score: 7.5
Vulnerability: Multiple
Patched Version: 4.3.18
NextScripts: Social Networks Auto-Poster is a plugin that automatically publishes posts from your blog to your Social Media accounts such as Facebook, Twitter, Google+, Blogger, Tumblr, Flickr, LinkedIn, Instagram, Telegram, YouTube, WordPress, etc.
During a routine research audit for our Sucuri Firewall, we discovered a post deletion, arbitrary posting in social networks, and arbitrary plugin settings update affecting over 100,000 users of the WordPress plugin.
Disclosure / Response Timeline:
- August 24, 2020: Initial contact attempt.
- August 25, 2020: Technical details sent.
- September 03, 2020: We contacted the WP team directly.
- September 04, 2020: Patch is live.
Current State of the Vulnerability
It can be exploited by any subscriber and potentially by unauthenticated users once an attacker with a subscriber account changes the plugin settings. We are not aware of any exploit attempts currently using this vulnerability.
Technical Details
Vulnerable versions of this plugin are giving access to several functionalities without using the proper restrictions — this can allow a bad actor to do the following:
- Remove Posts (by corrupting the post type and other data)
- Post Arbitrary Information in the site social networks
- Change the plugin settings
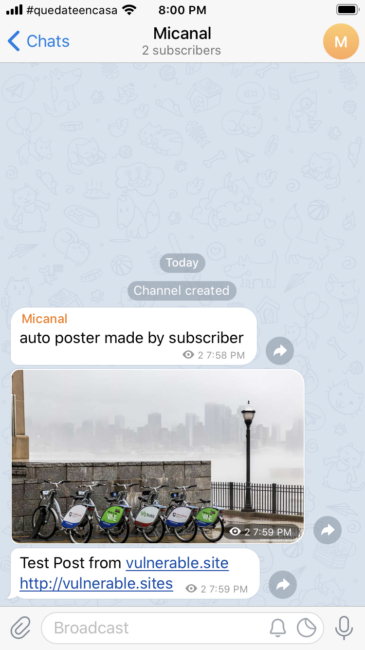
Here’s an example of a message sent by a subscriber to Telegram:
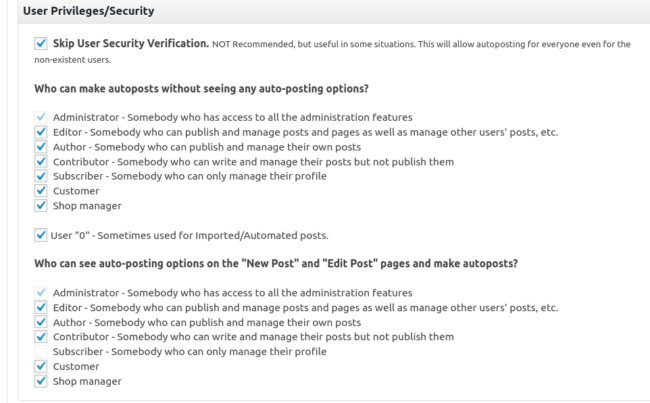
Critical settings that can be activated:
An attacker can leverage multiple attacks by making use of all the functionalities provided by the plugin. We’ll provide more details in our vulnerability digest at the end of this month.
Update as Soon as Possible
To protect against this vulnerability, we strongly encourage NextScripts: Social Networks Auto-Poster users to update their plugin to version 4.3.18 as soon as possible. Users that are unable to update immediately can leverage the Sucuri Firewall or equivalent technology to virtually patch the vulnerability.