Exploitation Level: Medium / Remote
DREAD Score: 6
Vulnerability: Cross-Site Scripting
Patched Version: 3.11.1
During a routine research audit for our Sucuri Web Application Firewall, we discovered a cross-site scripting (XSS) vulnerability affecting 100,000+ users of the YITH WooCommerce Ajax Product Filter plugin.
Current State of the Vulnerability
This security bug was fixed in the 3.11.1 release. We are not aware of any exploit attempts currently using this vulnerability.
Disclosure / Response Timeline
- Jun 4, 2020: Initial contact.
- Jun 22, 2020: Patch is live.
Technical Details
As seen below, the code lacks proper user input sanitization. Successful attacks force victims to execute unwanted actions when they’re authenticated within their user account.
This essentially means that the vulnerability requires user interaction to be successful. If the correct conditions are met, however, an attack may result in malicious scripts executed under the current user context.
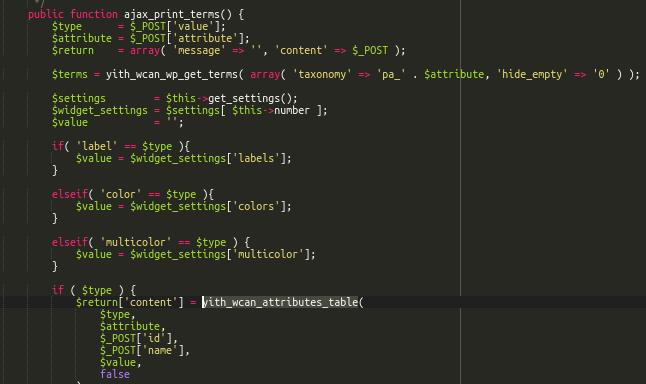
By exploiting this vulnerability, an attacker can perform requests to add unwanted spam content or execute other malicious actions asynchronously based on the privilege level of the victim.
Update as Soon as Possible
To protect against this vulnerability, we strongly encourage YITH WooCommerce Ajax Product Filter users to update their plugin to version 3.11.1 as soon as possible.
Users that are unable to update immediately can leverage the Sucuri Web Application Firewall or equivalent technology to virtually patch the vulnerability.









