Security Risk: High Exploitation Level: Easy CVSS Score: 9.9 / 7.7 Vulnerability: Privilege Escalation, SQL Injection Patched Version: 4.1.5.3
Last week, security researcher at Automattic Marc Montpas recently discovered two severe security vulnerabilities within one of the most popular SEO plugins used by WordPress website owners: All in One SEO. The plugin is used by more than three million websites and if left unpatched could cause some serious headaches for WordPress users.
The Details
Both vulnerabilities require that the attacker have an account on the website, but the account could be as low-level as a subscriber. By default new accounts are ranked as subscriber and do not have any privileges other than writing comments. However, certain vulnerabilities, such as the ones just discovered, allow these subscriber users to have vastly more privileges than they were intended to have. If a WordPress website has account creation enabled, when exploited in tandem, these two security holes allow an attacker to take over an unpatched WordPress website.
Authenticated Privilege Escalation
The first issue found with this plugin is interesting, and can be exploited by simply changing a single character of a request to uppercase. It affects versions 4.0.0 and 4.1.5.2 of All in One SEO. This plugin has access to a number of REST API endpoints, but performs a permission check before executing any commands sent. This ensures that the user has proper permissions to instruct the plugin to execute commands. However, All in One SEO did not account for the subtle fact that WordPress treats these REST API routes as case-insensitive strings. Changing a single character to uppercase would bypass the authentication checks altogether.
When exploited, this vulnerability has the capability to overwrite certain files within the WordPress file structure, effectively giving backdoor access to any attacker. This would allow a takeover of the website, and could elevate the privileges of subscriber accounts into admins.
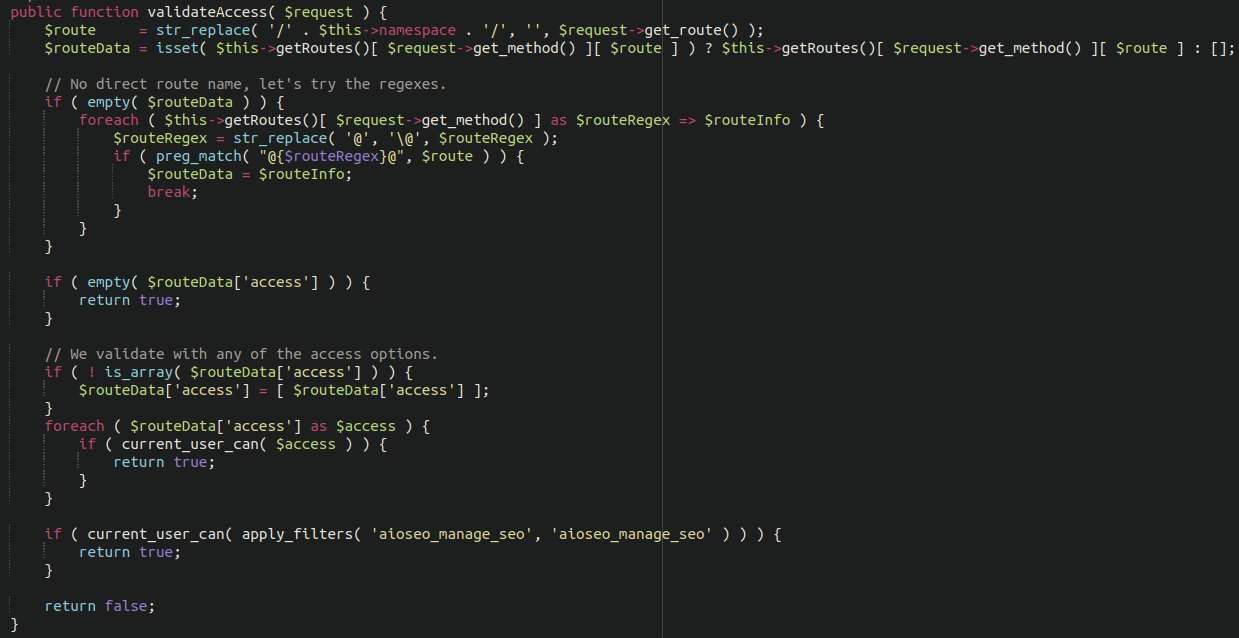
Vulnerable code in All-In-One-SEO WordPress plugin allowing for privilege escalation
Authenticated SQL Injection
The second vulnerability discovered is present in versions 4.1.3.1 and 4.1.5.2 of this plugin. There is a particular endpoint located here:
/wp-json/aioseo/v1/objects
This endpoint isn’t intended to be accessible by low-level accounts. However, since the previous vulnerability described allowed for privilege escalation, the attackers could first elevate their privileges and then execute SQL commands to leak sensitive data from the database, including user credentials and admin information.
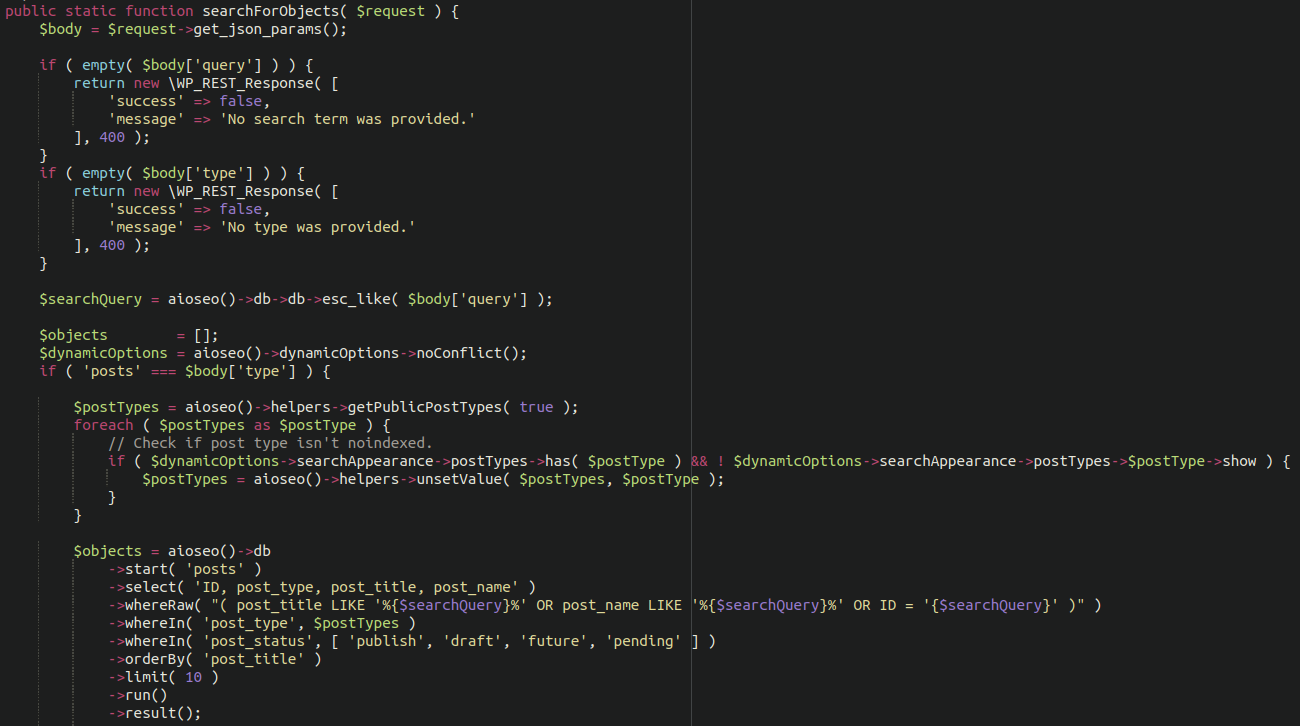
Vulnerable code in All-In-One-SEO WordPress plugin allowing for SQL injection
In Conclusion
If your website is using All in One SEO be sure to update to the most recent version as soon as possible! You will also want to review the administrator users present on your website. Remove any suspect users that you do not recognise, and for good measure change all administrator account passwords. It’s also prudent to add some additional hardening to your administrator panel.
Users of our firewall are protected against these vulnerabilities. Although we always recommend updating out of date plugins to the most recent version, particularly in cases such as these where security issues are present!
Edit: A previous version of this post stated that WordPress has public user creation enabled by default. This was incorrect as it does, in fact, have to be manually enabled by site administrators.









