Since September 2022, our research team has tracked a surge in WordPress malware redirecting website visitors to fake Q&A sites via ois[.]is. These malicious redirects appear to be designed to increase the authority of the attacker’s sites for search engines.
PublicWWW results show nearly 15,000 websites have been affected by this malware so far. Our own SiteCheck scanner has detected these redirects on over 2,500 sites during September and October. According to data from our internal cleanups, the file structure of each affected website contains a great deal of infected files — nearly 20,000 detections in total.
What makes this campaign especially unusual is that attackers are found to be promoting a handful of fake low quality Q&A sites.
In this post, we’ll be analysing what this infection does, how the malicious redirects work, and how to mitigate risk and clean up the malware.
Contents:
- Overview
- Commonly infected files
- Evasive techniques
- Redirect scripts
- Evolution of malicious redirects
- Redirects to spammy Q&A sites
- Redirect destinations
- Cleanup instructions
- Mitigation techniques
Overview
Malicious SEO redirects can be described as malware designed to hijack a website in order to abuse its resources (especially website traffic and rankings). Attackers are often found promoting spam for pharma, essay writing services, knockoff designer products — or in this case, fake Q&A sites.
Redirects to spam websites are nothing new. In fact, over 50% of the malware Sucuri cleaned last year was SEO spam. Furthermore, spam accounted for over one third of all malware detections from our SiteCheck tool. That said, spam redirects in particular are not as common with just over 13% of all SEO spam infections classified as a malicious redirect.
Analysis of malicious ois[.]is redirects
Some website malware infections limit themselves to a small number of files, often to limit their footprint and avoid detection. This malware is the opposite — with on average over 100 files infected per website.
Let’s take a look at some of the most common infection locations.
Commonly infected files
The most commonly affected files are core WordPress files, however this malware is also found to infect malicious .php files created by other unrelated malware campaigns.
Here are the top 10 most commonly infected files.
- ./wp-signup.php
- ./wp-cron.php
- ./wp-links-opml.php
- ./wp-settings.php
- ./wp-comments-post.php
- ./wp-mail.php
- ./xmlrpc.php
- ./wp-activate.php
- ./wp-trackback.php
- ./wp-blog-header.php
Our research team has also seen instances where the infection was found in random or pseudo-legitimate file names, including:
- RVbCGlEjx6H.php
- lfojmd.php
- wp-newslet.php
- wp-ver.php
- wp-logln.php
Since the malware intertwines itself with the core operations of WordPress the redirect is able to execute itself in the browsers of whomever visits the site.
Evasive techniques
Next, let’s take a look at the malware itself.
Here’s an example of the malicious code found injected into the main index.php file of an infected WordPress environment:
![Malicious redirects ois.]is black hat malware code sample](https://blog.sucuri.net/wp-content/uploads/2022/11/malicious_redirect_main_wordpress_index_php_file.png)
The snippet near the top of the injection is responsible for checking to see if the website visitor is currently logged in to WordPress.
$ckUjYggTf = 0; foreach($_COOKIE as $vUjUnHvOOoO => $vvvUjUnHvOOoO){ if (strstr(strval($vUjUnHvOOoO), 'wordpress_logged_in')){ $ckUjYggTf = 1; break; } } if($ckUjYggTf == 0 && !strstr(strval($_SERVER['REQUEST_URI']), 'wp-login.php')){
The redirect will not occur if the wordpress_logged_in cookie is present, or if the current page is wp-login.php. This is used as an evasive maneuver to conceal itself from administrators.
Redirect scripts
If the malware does not detect a logged in user or login attempt it then injects the malicious JavaScript code. There are two common variations of redirect scripts currently in circulation.
Basic redirect:
In one variant, we’ve seen attackers use a simple combination of window.location.href and meta refresh redirects, as seen below.
<script>window.location.href='hxxps://ois[.]is/images/logo.png';</script><meta http-equiv='refresh' content='0;URL=hxxps://ois[.]is/images/logo.png'>
Sophisticated redirect:
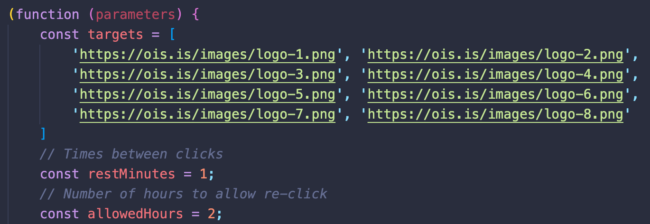
Another more sophisticated variant saves information about the redirect in the visitor’s browser localStorage to make sure they are not redirected more than once in 2 or 6 hours, depending on the variant used. This value is hardcoded in the allowedHours variable.
![ois.]is redirect malware variant uses allowedHours to define redirect frequency](https://blog.sucuri.net/wp-content/uploads/2022/11/allowed_Hours_used_to_define_redirect_frequency.png)
Redirects to logo.png files
In all cases, the malware redirects to .png files. The simple version has just one redirect destination:
- hxxps://ois[.]is/images/logo.png
While the more complex variant chooses one of the following 8 files:
- logo-1.png
- logo-2.png
- logo-3.png
- logo-4.png
- logo-5.png
- logo-6.png
- logo-7.png
- logo-8.png
Evolution of malicious redirects
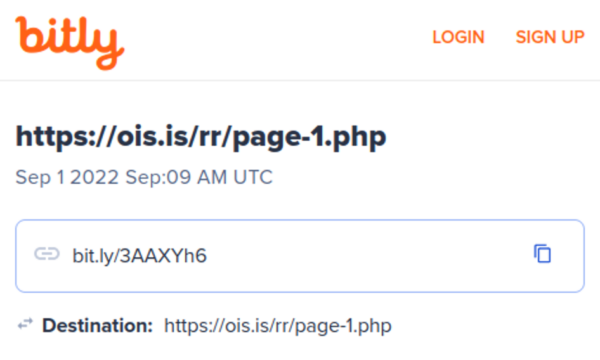
In the beginning of this campaign the attack used the bitly shortened link service hxxps://bit[.]ly/3AAXYh6 that eventually redirected to hxxps://ois[.]is/rr/page-1.php and then to hxxps://ois[.]is/images/logo.png.
According to Bitly, this link was created on September 1, 2022.
Redirects to spammy Q&A sites
An image file is a strange way of initiating a redirect, so let’s take a look at what exactly is loading when we access it.
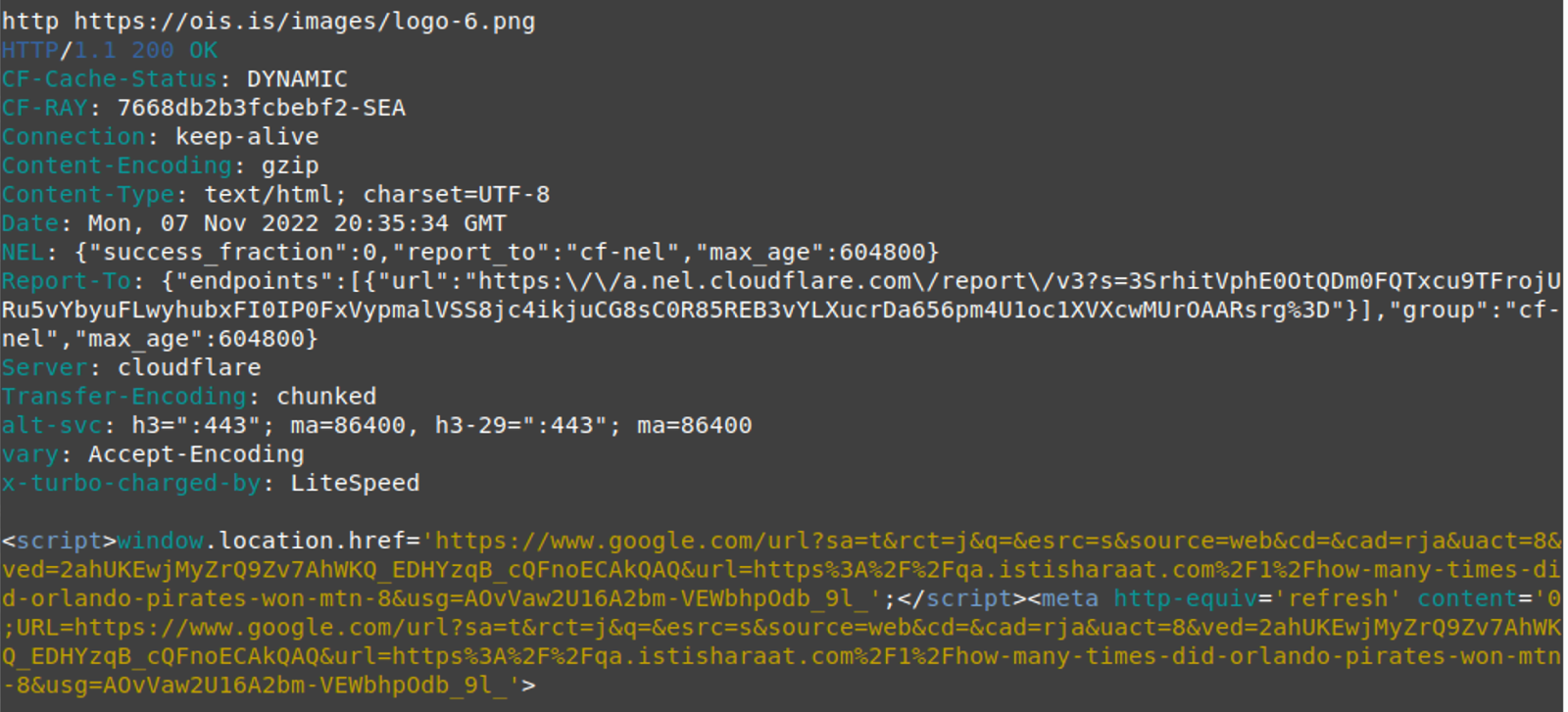
The malware uses the window.location.href function to redirect to a Google search result URL of a spam domain of their choice.
In this case, attackers used a bogus question and answer site:
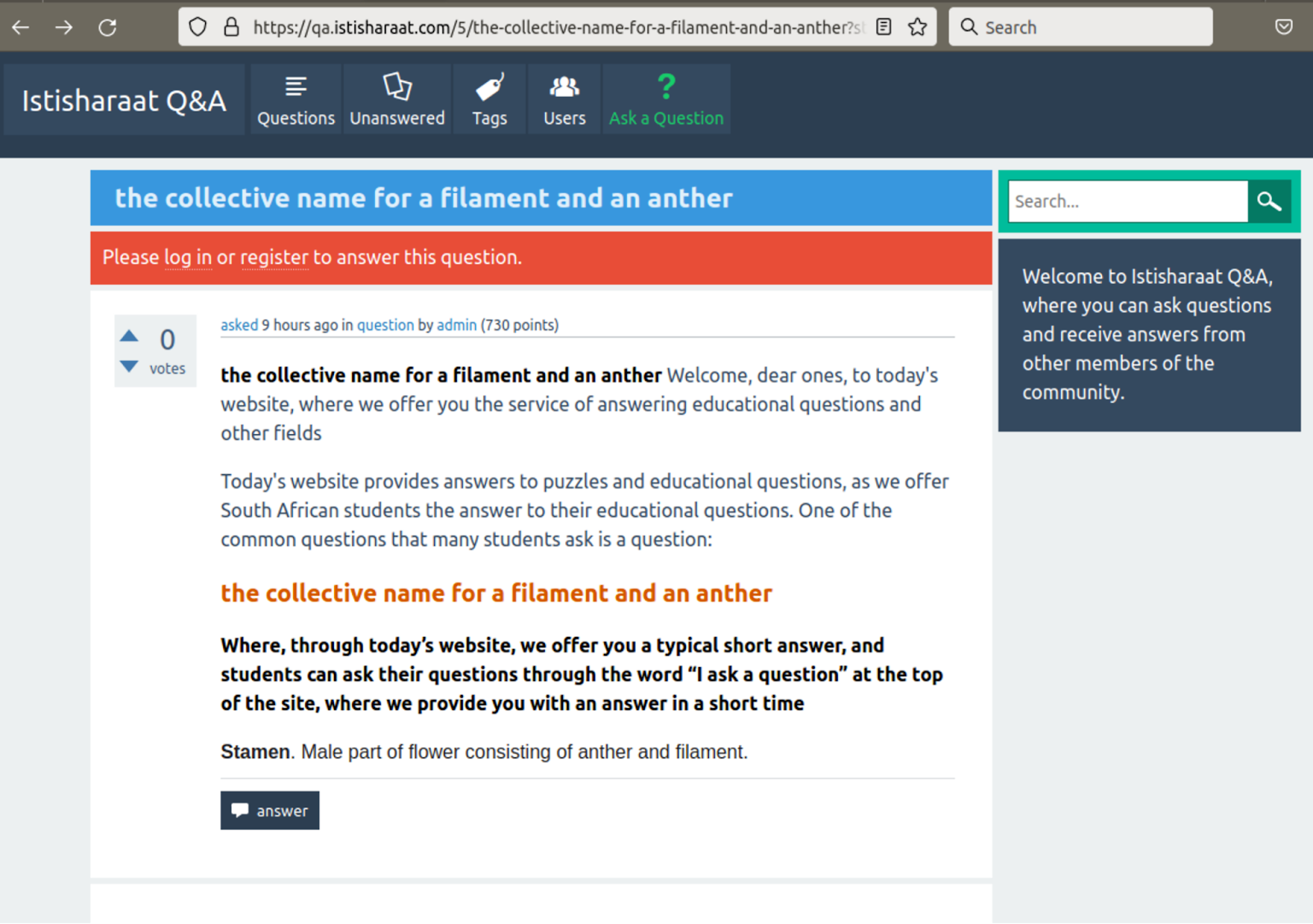
Redirect destinations
We’ve observed attackers rotating the websites that they redirect to. At this point, we have identified the following redirect destinations:
- en.w4ksa[.]com
- peace.yomeat[.]com
- qa.bb7r[.]com
- en.ajeel[.]store
- qa.istisharaat[.]com
- en.photolovegirl[.]com
- en.poxnel[.]com
- qa.tadalafilhot[.]com
- questions.rawafedpor[.]com
- qa.elbwaba[.]com
- questions.firstgooal[.]com
- qa.cr-halal[.]com
- qa.aly2um[.]com
Some of these sites have more than one subdomain (e.g. en. and qa.). You can find many of them using this URLscan.io query.
It’s worth mentioning that most of the sites (including ois[.]is) hide their servers behind the CloudFlare proxy. Additionally the sites seem to be using the same Q&A pattern and are built using the Question2Answer (Q2A) open source Q&A platform. According to their website this platform is currently powering over 24,500 sites in 40 languages.
Destination content and spam themes
The attackers’ spam sites are populated with various random questions and answers found to be scraped from other Q&A sites. Many of them have cryptocurrency and financial themes.
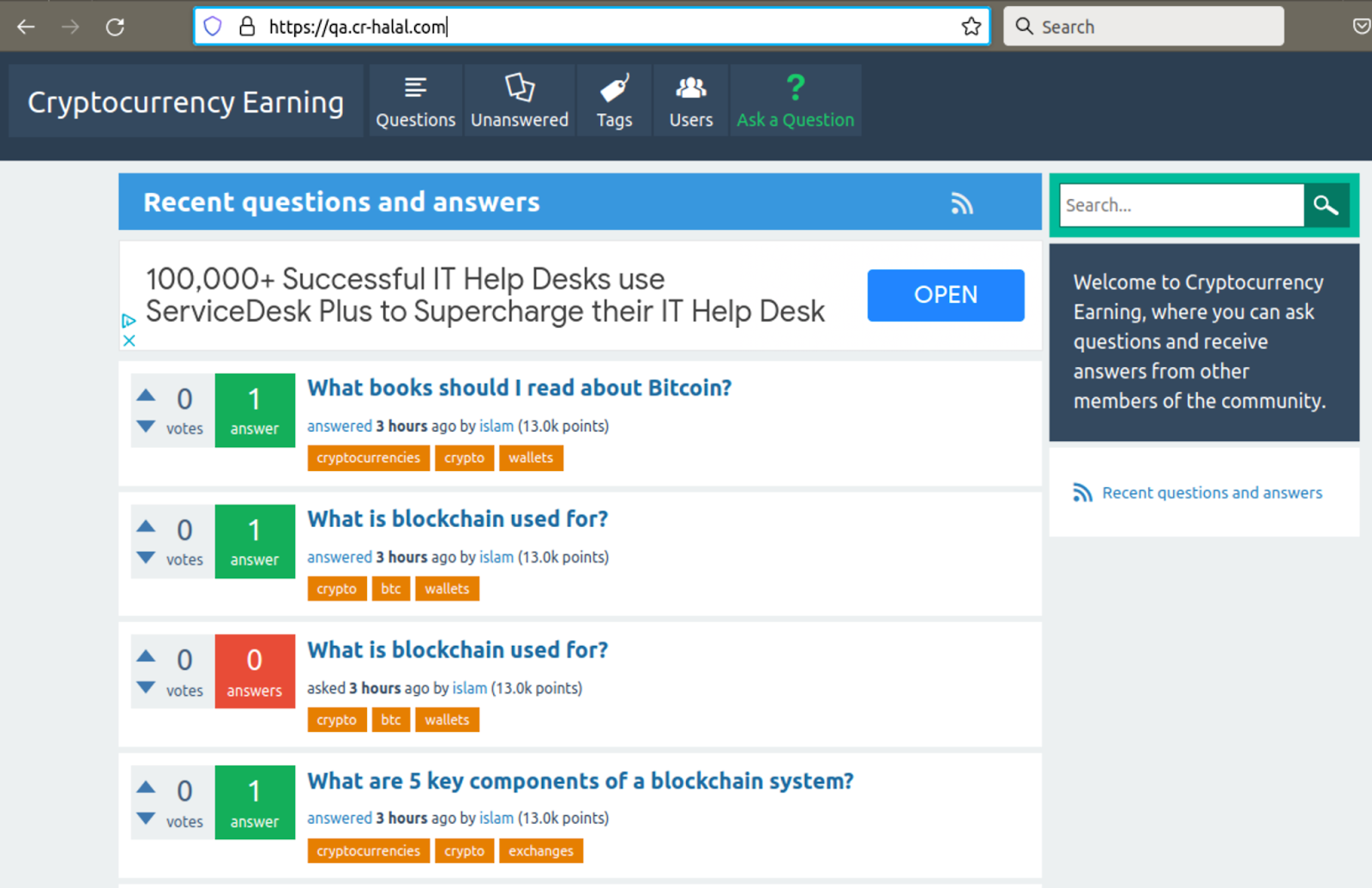
At this point, we haven’t noticed malicious behavior on these landing pages. However, at any given time site operators may arbitrarily add malware or start redirecting traffic to other third-party websites.
Hypothesis
This campaign seems to be trying to increase the authority of their Q&A sites for search engines which is probably why attackers are using Google search result links in their redirects.
It’s possible that these bad actors are simply trying to convince Google that real people from different IPs using different browsers are clicking on their search results. This technique artificially sends Google signals that those pages are performing well in search.
If this is the case, it’s a pretty clever black hat SEO trick that we’ve rarely seen used in massive hack campaigns. However, its effect is questionable given that Google will be getting lots of “clicks” on search results without any actual searches being performed.
This black hat SEO theory is also backed by the fact that the second level domains of the Q&A sites seem to belong to the same people. The hosted websites use similar templates and pretty low quality content (mostly in Arabic language) that is either scraped from some other sites or created for search engines rather than real humans.
The themes of the second level domain sites also speak for themselves. For example, cr-halal[.]com talks about crypto coins and tadalafilhot[.]com has the word tadalafil in the domain name, which is generic name for Cialis – one of the top erectile dysfunction drugs promoted by pharma spam malware campaigns.
Some of the second level domains don’t have actual sites but show the directory index that reveals additional information about the campaign. For example, istisharaat[.]com and aly2um[.]com show the following Q&A subdomains created on April 20, 2021.
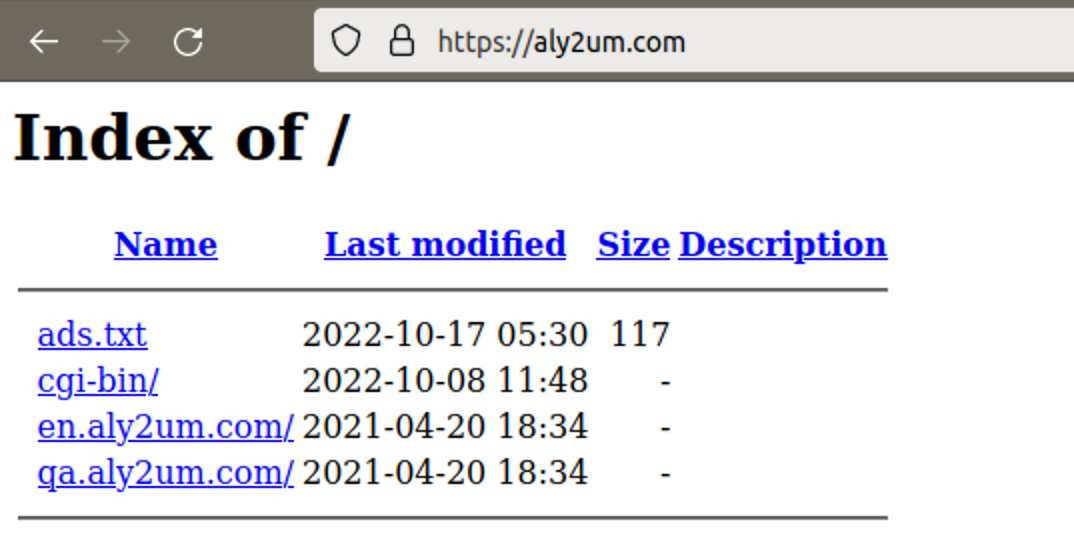
These domains also contain the ads.txt files, seen below.
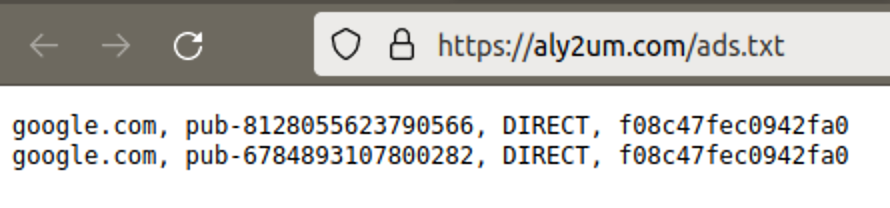
These files simply show that the sites are placing AdSense ads only from Google and the publisher IDs. You can find these ads.txt files on sites that don’t expose their directory listings, too.
More profits from Google AdSense was most likely the original plan for those Q&A sites — but it turned out that creating sites populated with scraped content from other sites didn’t generate enough traffic.
It appears that the site operators eventually resorted to this malware campaign to try and address their main problems:
- Drive more traffic to their fake sites (and hopefully click on Google Ads)
- Boost the sites’ authority using fake search result clicks to make Google rank them better so that they get more real organic search traffic
Cleanup instructions
If you’ve found that your website is a victim of this malware then there are some steps you can take to remove the infection and get your website back to normal operation.
Performing a core file integrity check should be your first step. If you can identify any files with this malware make sure to query your file system for any other files containing the same injection; there are almost certainly going to be quite a few others.
This malware is frequently paired with other injections, particularly those found in bogus .htaccess files or spammy .html files. Search your file system for any recently modified or added files.
For example, if you know that the infection happened within the last two weeks you can run this SSH command to find all files modified within the last 15 days:
$ find . -type f -mtime -15
You’ll also want to ensure that any and all backdoors injected by the attackers have been removed, otherwise reinfection is likely.
For more detailed information, check out our “How to Fix a Hacked WordPress Website” guide.
Mitigation techniques
We have not noticed any obvious single plugin vulnerability exploit that seems to be associated with this spam campaign, although attackers routinely use exploit kits to probe for any common vulnerable software components.
It’s also likely that websites are being compromised from compromised wp-admin administrator panels. For this reason it’s highly recommended to secure your wp-admin panel with 2FA or other access restrictions.
And (as is the case with all other website infections) make sure to change all administrator and access point passwords (such as FTP accounts, cPanel, hosting, etc). You’ll also want to ensure that all software on your website is up to date and patched to the most recent version.
You can place your website behind a firewall to help protect it against attacks. And as always, if your website is hacked and you’d like some help getting everything cleaned up, sign up for our security services and we’ll sort it out for you!
![Massive ois[.]is Black Hat Redirect Malware Campaign Targets WordPress Sites](https://blog.sucuri.net/wp-content/uploads/2022/11/BlogPost_Feature-Image_1490x700_PHP-Login-Stealer-820x386.png)








