Website backdoors are a silent yet deadly threat to website security. These stealthy mechanisms bypass standard authentication, providing attackers with persistent, unauthorized access to a website’s backend. Often overlooked, backdoors allow cybercriminals to maintain access long after an initial breach. Understanding the risks they pose and how to mitigate them is essential for website owners who value security, reputation, and operational integrity.
The Threat of Website Backdoors
Backdoors represent a sophisticated level of intrusion, allowing attackers to maintain control of a system without detection. Classified as trojans, backdoors disguise themselves to appear as part of a theme or plugin, and can be encrypted within discreet fine names like .users.php. They enable repeated data breaches, allowing sensitive information such as user credentials, personal data, and financial records to be siphoned off. Attackers can also manipulate site settings, deploy additional malware, or even damage the system’s integrity.
The numbers speak for themselves. In our 2023 Hacked Website Report, 49.21% of compromised websites were discovered to contain at least one backdoor at the time of infection. Our team successfully removed 21,062 backdoors from these infected sites. This alarming statistic highlights the importance of vigilance and proactive measures to combat these silent attackers.
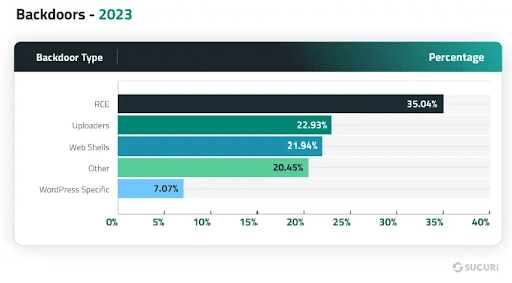
Our latest report also identified the most common backdoor types found on compromised websites in 2023:
Common Backdoors and Their Risks
Backdoors come in various forms, each uniquely tailored to exploit vulnerabilities. Here are the most common types:
Remote Code Execution (RCE) Backdoors
RCE backdoors allow cybercriminals to execute commands on the compromised server. Often embedded in GET/POST parameters or COOKIE values, these deceptively small backdoors enable unauthorized activities like script execution and data manipulation, making them a favorite among attackers.
Uploader Backdoors
Uploader backdoors let attackers upload harmful files directly to a website’s filesystem. Once uploaded, these files can install malware, overwrite legitimate content, or deploy phishing pages designed to exploit unsuspecting visitors.
Web Shell Backdoors
Web shells offer attackers comprehensive control over a server’s environment. They enable database manipulation, file management, and even port scanning. With these powerful tools, attackers can operate freely within a compromised system.
WordPress-Specific Backdoors
Given WordPress’s popularity, it’s no surprise that attackers have tailored backdoors to exploit this platform. These backdoors often disguise themselves as fake plugins or scripts, creating unauthorized admin users or granting attackers dashboard access without authentication.
See our recent post for further insights and detailed analysis of these backdoor threats.
Consequences of Backdoor Breaches
The impact of backdoors is far-reaching and goes beyond mere technical issues:
- Unauthorized Access: Attackers can manipulate content, alter settings, and steal sensitive data.
- Persistent Threats: Designed to remain hidden, backdoors can survive updates and re-infections, ensuring attackers retain control.
- Data Theft: Sensitive information, from credentials to financial data, can be stolen and exploited for fraud or identity theft.
- SEO Penalties: Search engines may detect malicious activity and penalize affected websites, resulting in lower rankings or deindexing.
- Reputation Damage: Breaches erode trust, potentially driving customers away and harming business growth.
How to Mitigate the Backdoor Threat
Protecting your website from backdoors requires a proactive approach. Here are the key steps:
- Keep Software Updated: Regularly update all software, including plugins and themes, to close known vulnerabilities.
- Deploy an Intrusion Detection System (IDS): An IDS monitors for unauthorized changes and suspicious activities, offering early warnings of potential threats.
- Use a Web Application Firewall (WAF): A WAF filters malicious traffic, blocks exploit attempts, and provides virtual patching to secure known vulnerabilities.
- Create Regular Backups: Secure backups allow you to restore your website quickly if it becomes compromised.
- Reset all Passwords: Always use strong passwords and consider using a password manager like KeePass, LastPass, 1Password, or Dashlane.
- Additional Authentication: Use CAPTCHA and multi-factor authentication on your website login.
- Monitor Traffic Patterns: Unusual spikes or repeated login attempts can signal malicious activity.
How Sucuri Helps
Sucuri provides a comprehensive suite of services designed to help website owners prevent and recover from backdoor attacks, keeping their sites secure. Here’s how Sucuri supports your website’s protection:
Website Monitoring Service
- Real-Time Detection: With Sucuri’s monitoring platform, you gain real-time insights into potential threats. The system continuously scans for unauthorized changes, suspicious activity, and other signs of compromise that may indicate a backdoor has been exploited.
- Automated Alerts: If a threat is detected, instant alerts ensure you’re notified immediately, enabling swift action to stop further damage.
Web Application Firewall (WAF)
- Traffic Filtering: The WAF acts as your website’s first line of defense, filtering out malicious traffic and blocking attempts to exploit vulnerabilities or plant backdoors.
- DDoS Mitigation: The firewall also shields your site from Distributed Denial of Service (DDoS) attacks, ensuring uninterrupted accessibility during threats.
- Virtual Patching: Without needing immediate software updates, the WAF virtually patches known vulnerabilities in your website’s components, reducing the risk of exploitation.
- Access Control: Use IP blocklisting and allowlisting to restrict sensitive areas like login pages or admin panels, minimizing the chances of unauthorized access. Add extra layers of protection with CAPTCHA or password requirements for critical sections.
Website Backups
- Routine Backups: Sucuri offers optional backup services, taking regular snapshots of your website. These ensure quick restoration in case of a backdoor attack or any other compromise.
- Secure Storage: Your backups are stored securely, safeguarding your data from breaches and keeping them readily available for recovery.
Advanced Threat Intelligence
- Emerging Threat Defense: A dedicated team of malware researchers continuously identifies and blocks the latest backdoor threats with updated signatures.
- Proactive Protection: Sucuri stays ahead of attackers, offering a defense against both established and emerging techniques that could compromise your website’s security.
Malware Remediation and Cleanup
- Expert Analysts: Sucuri’s seasoned security professionals specialize in detecting and eliminating backdoors. They perform in-depth scans of your website, server, and database to locate and remove malicious code.
- Thorough Restoration: Beyond removing threats, the cleanup process ensures all vulnerabilities and backdoor entry points are sealed, restoring your website to a secure state.
- Post-Infection Support: After cleanup, Sucuri provides ongoing protection to prevent future attacks and maintain your website’s integrity.
By focusing on proactive defense, rapid threat detection, and expert remediation, Sucuri helps ensure your website remains free from backdoors and other security threats.
Act Now to Protect Your Website
Website backdoors are a dangerous threat, and ignoring them puts your website, customers, and reputation at risk. By combining regular updates, proactive monitoring, and security solutions like Sucuri, you can protect your online presence from these hidden threats.
Don’t wait for a breach to take action. Contact Sucuri at info@sucuri.net to secure your website and safeguard your business.