Ever wondered where Cisco store their logs? Or what is the IP address for the Facebook development box? Or how a certain big company organize their IP addresses internally? Or where their database server is located?
Well, that’s easy to find. Just do a quick DNS query to find out:
$ host logserver.cisco.com
logserver.cisco.com has address 10.86.229.184
$ host dev.facebook.com
dev.facebook.com has address 10.8.253.45
$ host oracle.sans.org
oracle.sans.org has address 10.10.10.10
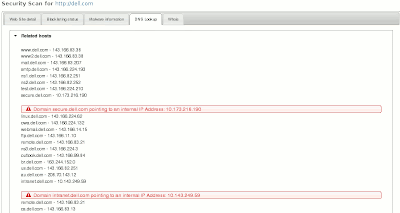
$ host intranet.dell.com
intranet.dell.com is an alias for intranet.ins.dell.com.
intranet.ins.dell.com has address 10.143.5.15
$ host secure.dell.com
secure.dell.com is an alias for insideclassic.ins.dell.com.
insideclassic.ins.dell.com has address 10.175.233.67
Another test. Do you think that Cisco uses git, CVS or SVN?
$ host cvs.cisco.com
cvs.cisco.com is an alias for total.cisco.com.
total.cisco.com has address 171.70.71.26
$ host svn.cisco.com
svn.cisco.com has address 10.86.100.70
$ host git.cisco.com
git.cisco.com is an alias for data-ibm7.cisco.com.
data-ibm7.cisco.com has address 10.93.230.122
Maybe all of them?
What is happening here, you may ask. These companies are not properly separating their internal and external DNS servers, thus leaking their internal structure to the outside.
How bad is that? Well, it makes external attacks much much easier. From DNS cache poisoning to XSS, you can do a lot more when you know where their internal assets are.
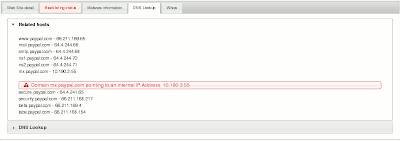
And they are not alone… Try checking where qa.ebay.com or mx.paypal.com or intranet.real.com are. I would image that such large companies would properly separate their DNS.
How did we find this out? Using our scanner:










1 comment
irrelevant comment
Comments are closed.