Malaysia is having an election this weekend that has been surrounded by issues. We won’t go into the politics, but one of our client’s sites (a popular Malaysian news source that we won’t name), started to suffer a very large scale DDOS (distributed denial of service attack). Reuters also has a similar story about another site and we can confirm what they are saying:
(Reuters) – Ahead of Malaysia’s elections on Sunday, independent online media say they are being targeted in Internet attacks which filter content and throttle access to websites, threatening to deprive voters of their main source of independent reporting.
This specific Malaysian site has been targeted for a couple of weeks, but since May 1st, their sites were hit by a very large botnet.
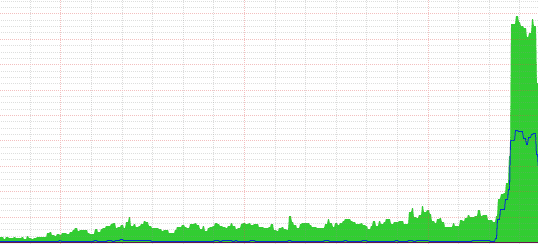
To protect the innocent, we won’t go into much details, but the green in the graph is the outbound data and the blue is the inbound. And that means thousands of simultaneous connections per second being sustained for the last 4 days against them.
Technical details
This DDOS is httpd-based and is targeting their web server. It started by targeting their 404 handler by trying to visit pages that do not exist. What was interesting is the choice of URL they decided to use “FloodFloodFLOOD”:
175.137.68.143 – – [01/May/2013:10:00:38 -0400] “GET /wp-content/uploads/2013/05/FloodFLOODFloodFLOOD.png HTTP/1.1” 404
w – – [01/May/2013:10:00:38 -0400] “GET /wp-content/uploads/2013/05/FloodFLOODFloodFLOODFloodFLOODFLOOD.png HTTP/1.1” 404 0
183.171.176.221 – – [01/May/2013:10:00:38 -0400] “GET /wp-content/uploads/2013/05/FloodFLOODFloodFLOODFloodFLOOD.png HTTP/1.1” 404
That can be easily blocked and filtered, so they quickly switched to more complex types of attacks. Since the site is WordPress, they decided to target the search function to bypass any internal caches and make sure that each page is actually loaded:
175.136.214.155 – – [02/May/2013:11:57:30 -0400] “GET /?s=1367683016682 HTTP/1.1” 200 154 “http://www.erapasca.com/2013/05/pecah-berita-tanda-bn-nak-tumbang.html” “Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.56 Safari/537.36”
175.136.214.155 – – [02/May/2013:11:57:30 -0400] “GET /?s=1367683016683 HTTP/1.1” 200 154 “http://www.erapasca.com/” “Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.56 Safari/537.36”
123.136.106.225 – – [02/May/2013:11:57:30 -0400] “GET /?s=1367682722241 HTTP/1.1” 200 154 “http://www.erapasca.com/2013/05/pecah-berita-tanda-bn-nak-tumbang.html” “Mozilla/5.0 (Linux; Android 4.0.3; GT-P5100 Build/IML74K) AppleWebKit/537.22 (KHTML, like Gecko) Chrome/25.0.1364.169 Safari/537.22”
175.140.99.225 – – [02/May/2013:11:57:30 -0400] “GET /?s=1367682708689 HTTP/1.1” 200 154 “http://siaranradioonline.blogspot.com/search/label/” “Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0; BOIE9;ENUS)”
.. thousands more per second ..
Notice that those referers and user agents are likely fake and just being used to try to bypass any security filter.
Size of the DDOS and their Botnet
What is actually impressive about this attack is the number of IP addresses (bots) being used. Just in the last 24 hrs, 36,367 (yes, 36 thousand different IP addresses ) were used to attack this site. It means that the people behind it have good power. What is interesting is that all IP addresses also come from Malaysian IP ranges and it seems to come from compromised desktops.
Since it is an ongoing event, we won’t give more details and we are working with the proper authorities and the Malaysian CERT to stop them.







3 comments
Thanks for giving me the useful information. I think I need it. Thank you
You say (a popular Malaysian news source that we won’t name) and name the site in logs http://www.erapasca.com/, http://siaranradioonline.blogspot.com.
35k+ bots. BotNet are growing at a fast pace lately.
Comments are closed.