Our friends from SpiderLabs, issued a warning today on their blog about increased activity on their honeypots looking to exploit the old JCE (Joomla Content Editor) vulnerability.
JCE is a very popular component that can be found enabled on almost any Joomla site. It has had a few serious vulnerabilities in the past (around 2011 and 2012), and unfortunately we still see thousands of unpatched sites out there. In fact, we get to clean and disinfect many sites compromised through it every single day.
You can read SpiderLabs’ full analysis here: [Honeypot Alert] JCE Joomla Extension Attacks
And an old one we did on UnmaskParasites about the increased scans we started to see for it a few months ago: Unmask: Invasion of JCE Bots
If you run a Joomla site and haven’t patched lately, please do it as soon as possible. If you are still on the Joomla 1.5.x branch, you need to do it today. There are exploits live in the wild for it, and if you have been lucky and didn’t get hacked yet, it will happen soon.
Vulnerability That Has Been Active For a While
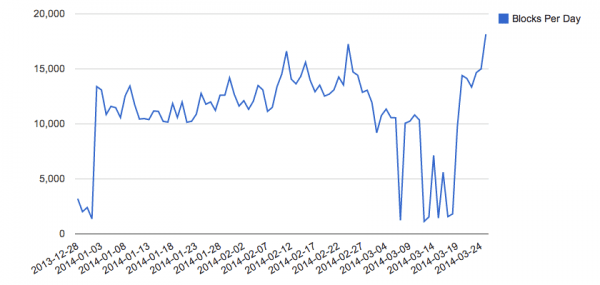
We have been tracking this vulnerability, and exploit attempts related to it in the wild for a while, and after reading the SpiderLabs report we exported our data for it and generated a quick graph where we could see a big bump in the number of exploit attempts over the last few weeks:
The graph seems to go up and down quite a bit and we will follow it closely over the next few days to see how it changes.
Type of Attacks
The attacks we are seeing match what they reported. It starts with a file upload of a GIF file, followed by the rename from the GIF to the PHP extension:
5.249.152.61 - POST /index.php?option=com_jce&task=plugin&plugin=imgmanager&file=imgman
ager&method=form&cid=
HTTP/1.1" 403 0 "-" "BOT/0.1 (BOT for JCE)"
form-data; name=x22upload-dirx22x0Ax0A/x0A-----------------------------41184676334x0AContent-Disposition: form-data; name
=x22Filedatax22; filename=x22x22x0AContent-Type: application/octet-streamx0Ax0Ax0A-----------------------------
41184676334x0AContent-Disposition: form-data; name=x22upload-overwritex22x0Ax0A0x0A-----------------------------4
1184676334x0AContent-Disposition: form-data; name=x22Filedatax22; filename=x22wawalo.gif
5.249.152.61 - POST /index.php?option=com_jce&task=plugin&plugin=imgmanager&file=imgman
ager&version=1576&cid=20
HTTP/1.1" 403 4143 "-" "BOT/0.1 (BOT for JCE)"
json={x22fnx22:x22folderRenamex22,x22argsx22:[x22/wawalo.gifx22,x22wawalo.phpx22]}" "COOKIE:-"
Once the file ends with PHP, it can be executed remotely and gives the attackers full access to the site.
In the example above, they tried to upload the fake image called wawalo.gif, renamed it to wawalo.php, and then later tried to execute it.
Another interesting point is that all exploits seem to use the code available from exploit-db and have a common user agent of “BOT for JCE“. That’s an easy thing to block, but the bad guys can change it easily as well.
If your site is patched, you are protected against this type of exploit. If you cannot upgrade your Joomla site or are afraid things will break, we highly recommend protecting it with a WAF (web site firewall), like CloudProxy.
List of IP Addresses Scanning
We went back over the last 90 days and we identified 5,562 different IP addresses scanning for this type of vulnerability. Most of them seems to be coming from Joomla sites that were already compromised.
So the bad guys hack one site, and use it to scan and exploit others. Below is the list of hosting companies where we are seeing the most compromised sites:
#Number of IPS Hosting Company
227 OVH
152 HETZNER
128 STRATO
104 ONEANDONE
102 PLUSSERVER
85 HOSTEUROPE
84 Locaweb
78 SWEB
76 UNIFIEDLAYER
56 SOFTLAYER
53 DIGITALOCEAN
47 AMAZON
42 IWEB
42 ARUBA
40 MEDIATEMPLE
39 SINGLEHOP
39 FIBERRING
And the full list of IP addresses that we identified in the last 90 days trying to exploit this vulnerability: http://labs.sucuri.net/jce-exploit-ips.txt
If your IP address is in there, you know you are compromised. For hosting companies: Please check if any of your IP addresses are listed in there.










1 comment
jce-exploit-ips.txt file is not avaiable. Could you fix it? Thx.
Comments are closed.