Security Risk: Dangerous
Exploitation Level: Easy
DREAD Score: 6/10
Vulnerability: Persistent XSS
Patched Version: 4.2.4
Last week the WordPress team released a patch that fixed 6 security vulnerabilities. Of the six, you’ll find one that we identified a few months back.
Vulnerability Disclosure Timeline:
May 6th, 2015 – Initial report to WordPress security team
May 8th, 2015 – WordPress security team confirming receipt of the report
July 23th, 2015 – WordPress 4.2.3 released, not fixing the issue
July 24th, 2015 – WordPress security team confirming it will be fixed on the next security release
August 4th, 2015 – Patch made public with the release of WordPress 4.2.4
Technical Details
The bug comes from the preview_theme() function, it is used by WordPress to temporarily preview what a specific theme will look like. It is hooked to the setup_theme action hook, which gets executed every time a theme is to be displayed.
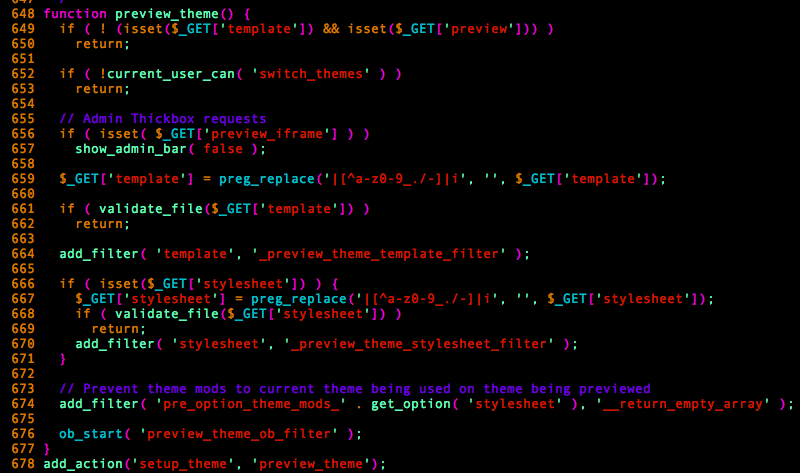
As you can see from the above screenshot, if a logged-in administrator visits one of the site’s pages and uses a few additional $_GET parameters (Which can happen, for example, if he clicks on a malicious link beforehand), this function will set preview_theme_ob_filter as ob_start‘s callback function.
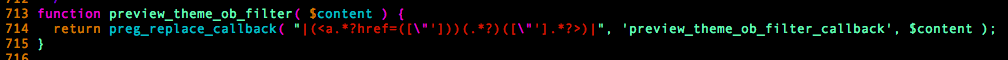
Once ob_start() has gathered all of the page’s content, it will call preview_theme_ob_filter() to grab all HTML links and filter them using the preview_theme_ob_filter_callback function.
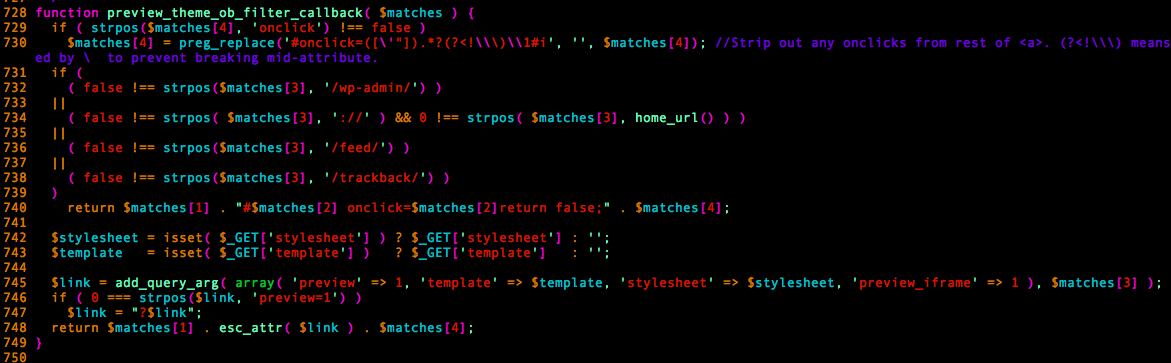
Which will, among other things, remove onclick=” event handlers from the link tags.
Where is the Issue?
The problem occurs when preview_theme_ob_filter_callback removes the onclick=” handlers as it could be used to actually insert new tag attributes to the HTML link by sending a tag similar to the following in a post comment:
<a href='/wp-admin/' title="onclick='" Title='" style="position:absolute;top:0;left:0;width:100%;height:100%;display:block;" onmouseover=alert(1)//'>Test</a>
Where the part in bold is the one that will get removed, accidentally inserting our style and onmouseover attributes, which will print the following link tag in the administrator’s browser:
<a href='/wp-admin/' title="" style="position:absolute;top:0;left:0;width:100%;height:100%;display:block;" onmouseover=alert(1)//'>Test</a>
This bypasses their filters that were in place to disallow javascript from being executed.
Updates Are Out, Ensure You Don’t Miss Them
If your site supports automatic updates, chances are it’s already been patched. If it’s disabled, you’ll want to manually update at your earliest convenience. We also recommend investing in a technology that can help proactively protect against vulnerabilities like the ones recently patch, something like a Website Firewall (WAF).











3 comments
Problem is wordpress security team is not enough. Before release they should find those bugs or vulnerabilities. But they are not making it because team is not enough. WP Security team must grow.
So this has to be done by an admin?
alert(XSS)
Comments are closed.