A malicious redirect is a snippet of code used by attackers with the intention of redirecting visitors to another site; a very common tactic seen in compromised websites.
These redirects often take visitors to phishing, malware, or advertising sites with the intention of capturing sensitive user data, distributing malware and backdoors, or generating advertisement impressions.
We’ve written before about how attackers use expired domains to redirect visitors to malware and ads, or how domains used in abandoned plugins are registered by hackers. Today we look a bit closer at how this can affect unsuspecting websites.
Malicious Redirects In Compromised Websites
Attackers can create malicious redirects in a variety of ways:
- Inserting malicious code into the .htaccess file (a very simple but effective technique, though only possible on Apache servers).
- NGINX servers can have their sites redirected VIA a hacked .ini file.
- CMS core files can be hacked and redirected using both JS and PHP.
- The DNS can be modified and redirected if an attacker gains access to the administration area.
- If a website uses a shared hosting provider, the other sites and root folders of those servers can be infected through cross-site contamination, causing a global redirect.
It’s always in a website owner’s best interest to remove these redirects as quickly as possible to avoid losing traffic, users, and reputation.
Sometimes the source of the malicious redirects can be hidden in vulnerable third-party software components on your website – such as plugins and extensions.
Compromised Plugins & Redirects
In a recent incident response, one of our researchers identified a compromised plugin that impacted multiple websites across the web.
This plugin had not been maintained for several years and was hosted by an expired domain, enmask.com. A visit to the WordPress plugin page reported:
“This plugin hasn’t been updated in over 2 years. It may no longer be maintained or supported and may have compatibility issues when used with more recent versions of WordPress.“
To make matters worse, the domain was purchased by someone with malicious intentions. When the attacker purchased the expired domain and included a malicious redirect, no updates were offered to resolve the issue as the plugin was no longer under development. As a result, multiple websites began serving the malicious content.
On further examination, our researcher found that malicious redirects were coming from a JavaScript file which was loading via the website enmask.com. In turn, this impacted the compromised WordPress plugin Enmask Captcha. The plugin has since been removed from the official WordPress repository.
The code found on the plugin domain included the following snippet:
![]()
The new website owner had configured the server hosting the domain to respond to requests for any javascript file, but always returned the following spam javascript with the redirect:
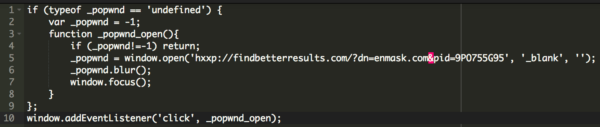
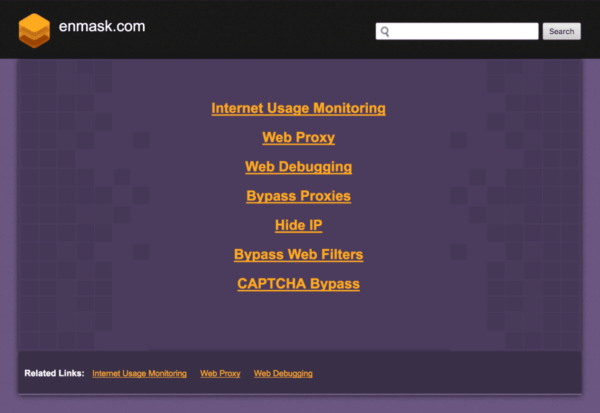
Clicking anywhere on the website caused users to be redirected to this parked page, which was also served by the compromised plugin:
Resolving Malicious Redirects
If you are currently using the Enmask Captcha plugin, we strongly urge you to remove it and replace it with another tool that is actively maintained and supported.
Loading images, scripts or other assets from external websites is not recommended and can potentially leave your website at risk of distributing unwanted content without your consent.
Vulnerabilities found in older themes, and plugins can be easily taken advantage of, which is why it’s important to audit the third-party applications you use on your website to ensure that they’re up-to-date and maintained.
A file integrity monitoring system can also help you track changes across files and revert modifications, which will help mitigate any impact to your website traffic and users. Our monitoring system scans for unauthorized changes to your DNS records so you can know if attackers are redirecting your domain at the DNS level.
If your website has been infected with a malicious redirect and you need help cleaning it up, we’re here to help.










