Recently we wrote about domain renewal scams that used real paper letters to tricks site owners into transferring their domains and renewing them for 3-4x the normal price. However, this is not the only way to make money on expiring domains. Today, we’ll show you another questionable million-dollar business on expired domain names that hurts completely unrelated third-party sites.
Here’s the story. A client’s site began to show annoying “XWINNER COM” ads and they wanted us to investigate the issue and clean the site. The research for this post was performed in collaboration with the Sucuri Labs team, specifically Denis Sinegubko (Unmaskparasites), who identified the source of the issue and some more interesting pieces of the puzzle.
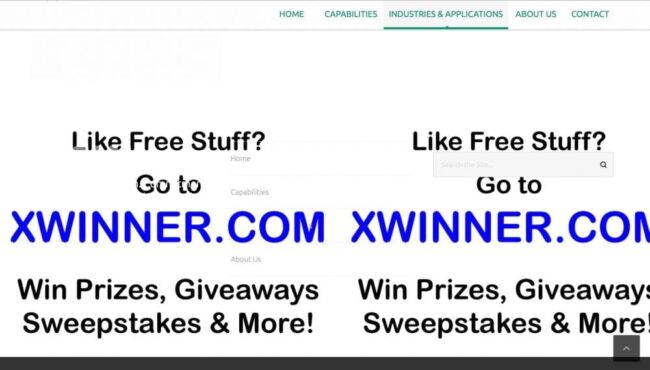
We analyzed HTTP traffic and noticed that the ad images loaded from a third-party site “www .twomediaxthemes .com”. It looked like hackers somehow managed to inject links to those images into theme files.
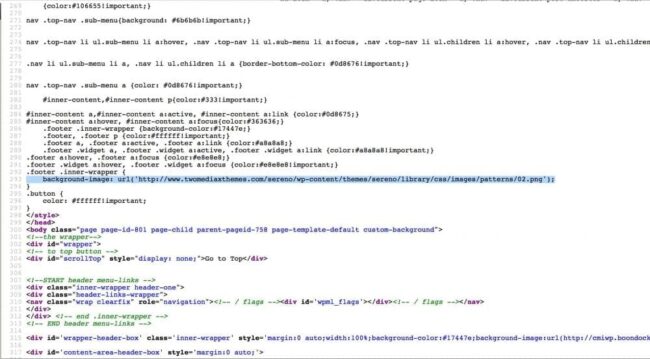
However, such an injection is not typical to site infections. After some more digging, we realized that the unwanted ad image was not hosted on a random malicious website. In fact, the website hosting spammy images was the theme developer’s own site, which was specified in the theme’s metadata.
Theme Name: Sereno Theme URI: http://www .twomediaxthemes .com/sereno Description:Ultra Responsive, Fast, Visual Shortcode Manager, next generation ready Version:1.3.1 Tags: flexible-width, translation-ready, microformats, retina ready, rtl-language-support IMPORTANT: CSS File is located under /library/css/style.css
Parked Domain
When accessing the website (www .twomediaxthemes .com), we were getting a page similar to those found on parked domains and there was no relation with the theme in question:
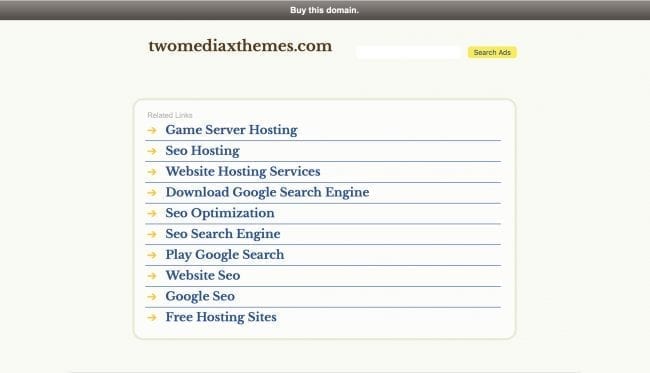
Now it’s getting clear that at some point the theme developers ceased their operations and didn’t renew the domain registration, which meant that websites using their theme couldn’t load the background images for the footer (this didn’t spoil the overall look of the pages though). Then, someone purchased the expired domain and parked it, which according to WHOIS information happened on May 21 2016 – just a week before the client asked us to find the source of the unwanted ads. When the background images began loading again, they were showing the ads.
Special Handling of Image URLs
It’s quite typical for parked domains to show all sorts of ads, but shouldn’t the expired URLs to non-existent images generate 404 errors?… or redirect to the home page? In either case, the response is not a valid image, so it shouldn’t be displayed as a background. We definitely need to dig dipper.
Indeed, if we open an arbitrary image URL in a browser, the site just shows ads or redirects us to some third-party site with ads (annoying but that’s what one can expect from a parked domain). If we try to put the same URL in the img tag and open a web page containing that tag, we see the XWINNER ad.
<img src="http://www .twomediaxthemes .com/this-file-should-not-exist.jpg">
Now we see what’s going on. This domain parking service identifies requests to image files made from within web pages (based on headers) and returns image ads to such requests. It is clear why they do it.
Ads On “Expired” Images
Imagine, you have blog and you need illustrations for your posts. Instead of creating your own illustrations, you just use Google Image search to find relevant images and insert them into your post as hot links. It’s a very common practice because it’s fast and easy and makes your post look great.
However, a few months (days, years) later the domain name of the site that contained the original image expired, and your post now shows an empty space instead of the nice image. You might not even noticed that. A few more months later, the expired domain gets registered and parked by a new owner and the parking service now shows an ad image instead of the original image that you inserted into your post. So when people visit your blog and open that post they see the ads from the domain parking service. The more that pages hotlink to images on expired-and-then-parked domains, the more money the parking service makes.
You don’t get a cent for [unwittingly] displaying ads on your site, moreover, instead of nice images you get ugly ads.
Master of the Expired Domains
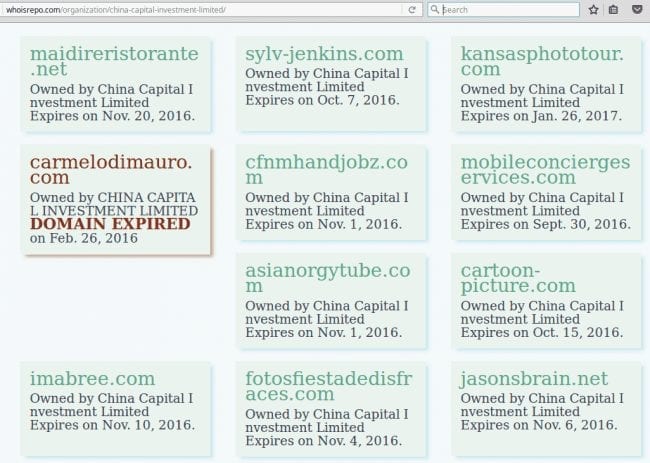
Now the question is how common this practice it. We noticed, that the domain is currently registered by China Capital Investment Limited.
Registrant Organization: China Capital Investment Limited Registrant Street: 3/F Wisdom Centre 37 Hollywood Rd Registrant City: Hong Kong
And this organization is associated with ~107,288 other domains (according to DomainTools). We checked random domains that belonged to them all of them were “parked” and serving image ads. Their own site made it clear that their business was buying and selling domains.
Moreover, while some of their “parked” domains were behind the Incapsula firewall, the others pointed to the server with IP address: 104 .130 .124 .96 (on RackSpace network). All sites on this server have the same behaviour. Even when you request image using the IP address instead of the domain names, you still get the XWINNER ad image, which suggests that this whole server is configured to host “parked” domains. For this IP, DomainTools reports 196,879 domains.
Almost 200,000 domains! That’s a big number. Actually, after we cleaned the site we began to notice those XWINNER images on different other sites. Now let’s do some math. A typical domain name cost in the ballpark of $10. So China Capital Investment Limited paid more than a million dollars for their 100K+ domains. And the whole 104. 130. 124 .96 server costs around $2 million dollars per year. It’s clear that no one pays millions of dollars just to park domains if they don’t expect return on their investment.
Business of Expired Domains
As far as I can tell, China Capital Investment Limited uses the following business model:
- They constantly analyze expired domain names and register those with many live backlinks for one year.
- “Park” the domains (point them to the same server that shows ads for any requests regardless of the domain) and hope that people will click on those active links so that they can make money on ads.
- In addition to clicks on the links, they hope to monetize the ads that they inject instead of expired hotlinked images.
- Finally, they offer their domains for sale on Latona’s Domain Marketplace. For example, here are the typical prices for domains they sell (as of June 23d, 2016):
- twomediaxthemes .com – $349
- wesupportkristen .com – $252
- highaltitudecreative .com -$252
- After a year, if a domain is not sold but helped generate more money than the renewal price, it gets renewed, otherwise it is dropped.
What Does This Mean for Web Surfers and Site Owners?
First of all, when clicking on an external link (especially on a link created more than a year ago), you can’t be sure that the site still belongs to the same people. Be ready if it no longer exists, is parked, or changed hands. The latter two variants may also mean that the new site is malicious or will redirect you to malicious pages. For example, the parked pages on the 104 .130 .124 .96 server randomly redirect to various ad services, and given their overall quality, some of them may participate in malvertising.
Secondly, if you use images directly linking to their locations on third-party sites, one day they may simply disappear or turn into unwanted ads. As we showed in this post, it may happen even if you don’t hotlink to third-party images yourself. Such a link may be embedded into your site theme, plugin or any other third-party component.
And finally, the most disturbing issue. After revealing the special handling of the image URLs, we decided to check what happens if we request a JavaScript file. It turns out, .js URLs return the following code:
var x = 'http://' + document.currentScript.src.split("/")[2];
if (top.location != location) {top.location.href = x;
} else {
window.location = x;
}This code redirects a page that loaded the script to the parked domain that shows ads. Unlike image hijacking, which only spoils the look of your web pages, this javascript hijacking simply steals your visitors.
Let’s imagine the following scenario: your active theme or some of the plugins load a third-party JavaScript library (say jQuery plugin) directly from the library developer’s site. Some time later, the developer’s domain expires and the library won’t load. However, it was not critical for the site functionality so you didn’t notice it. A few months laters, the domain gets registered by someone who hijacks all .js URLs, and out of the blue, your site begins redirecting all visitors to a third-party site. Disturbing, isn’t it? This is not a far fetched scenario. We already wrote about how an abandoned jQuery Timers plugin began serving malicious code.
What Can We Learn From This Case?
Loading third-party elements on your site (whether they are static images or executable scripts) always make your site less secure. You leave it at mercy of people and companies that you don’t know and can’t control.
Don’t hotlink images and other static resources from third-party sites. On one hand it may be considered as theft of bandwidth and intellectual property, on another hand, even if you do it with the resource owner permission, your site may become broken or infected should anything happen to the third-party site. In this case, the safer approach will be to upload the resource on your own server and use it from your own domain.
If you really need to load something from third-party domains, choose the resource providers very carefully. You should be confident that they will not cease operation (or move to another domain) during the whole lifespan of your site and that they take security very seriously and can guarantee that loading resources from their sites will not cause any security problems on your site. A good example will be big reputable CDN services that provide common JavaScript libraries and fonts.
If you are a developer of templates, themes, plugins, etc that people can install on their sites, please include all the static resources inside the package instead of linking to them on your site (or any other third-party site). If you lose your interest in maintaining this software in a few years, there still will be sites that use it. If something happens to your site, their sites will be affected too.
Of course, as a site owner, you may be using dozens of third-party themes and plugins and it’s hard to make sure that they all use best practices. I suggest that you begin with an audit of third-party software.
- Minimize your dependency on third-party software – remove anything that you don’t really need or use.
- Update everything – if some package doesn’t have updates for years, it may not be maintained any longer and you should consider finding an alternative to it. Unmaintained software may have security holes that won’t be fixed. Or it (or its domain like in this case) can be hijacked by people with malicious intents.
- Regularly scan your site for broken links – don’t wait until they affect functionality or security of your site. As this post shows, it is important to include images, backgrounds, style sheet and script links in the scan. Programs like Xenu Link Sleuth will help you with this task.
Conclusion
Once again, we see that website security is not only about passwords, file permissions, vulnerabilities and software updates. Almost any decision that you make may affect your site in the long run. Yes, security may be overwhelming if you are a beginner or trying to do everything yourself. That’s why it is important to be able to outsource routine and technically complex tasks such as monitoring, cleanup and attack prevention to professionals.









1 comment
Great article. It is so amazing which business models people use and how the make money.
Comments are closed.